/
IT Management Interactive Learning - Using technology in education
Digital Transformation in Education Platforms Hardware Software Cross-Platform Computer networks Cloud Computing Power and Potential of Open-Source Movement Motivation Economy Licenses Software Public Participation Information Systems (IS) Introduction Approaches to IS Office automation systems (OAS) DIKW pyramid Transaction Processing System (TPS) Management Information System (MIS) Decision Support Systems (DSS) Executive Information System (EIS) Business Intelligence (BI) Analytics Components and Technologies Conclusion 1. Monolithic Architecture 2. Layered (n-tier) Architecture 3. Service-Oriented Architecture (SOA) 4. Microservices Architecture 5. Event-Driven Architecture Business Process Management System (BPMS) Enterprise Resource Planning (ERP) Enterprise Resource Planning (ERP II) Intelligent Business Process Management (iBPMS) Business Management Systems (BMS) Content Management The role of content production Search Engine Optimization (SEO) Enterprise Content Management (ECM) Knowledge Management System (KMS) Social Network Management System(SNMS) Content Management System (CMS) Document Management System (DMS) Comparison Information Systems (IS) in Education Quizzes, Tests, and Exams Content Authoring Tools Textbooks, Question Project Management Systems (PMS) Compare PMS & PMIS Quality Management Systems (QMS) Affiliate Marketing Management System School Information Management Systems (SIMS) Educational Management Information System (EMIS) Research Management Information System (RMIS) Learning Management Systems (LMS) Virtual Classroom Software Research Information System (RIS) Current Research Information System (CRIS) Research Networking Tools Conclusion Electronic Government Security Issues Technical Issues Social Issues Administrative Issues Legal Issues Ethical Issues Non-Key E-Government Security Issues Key E-Government Security Issues Issues That Are Not Typically Key E-Government Security Issues Conclusion IT Marketing Benefits of Using IT in Business Marketing: Examples of IT in Business Marketing: Challenges and Considerations: Introduction to IT Marketing Key Components of IT Marketing Conclusion Game in Education Management Gamification Video Games Ludology Conclusion BPM (Business Process Management): ERP (Enterprise Resource Planning): Comparison: WebsiteDigital Transformation in Education
Digital Transformation in Education: Leveraging Technology and Information Systems for Effective Educational Management
Introduction:
In today's rapidly evolving digital era, technology and information systems have become indispensable tools that are reshaping the landscape of educational management. "Digital Transformation in Education" explores the transformative potential of technology and information systems in enhancing efficiency, effectiveness, transparency, and accountability in educational institutions. This book serves as a comprehensive guide for educators, administrators, technology leaders, policymakers, and stakeholders interested in understanding and leveraging the power of technology and information systems to drive innovation, excellence, and success in educational management.
Overview:
The book begins by providing a foundational understanding of technology leadership, management, and integration in educational settings, exploring key concepts, trends, challenges, and opportunities related to educational technology and information systems. It delves into various technologies and systems, such as Educational Management Information Systems (EMIS), Learning Management Systems (LMS), school management software, communication and collaboration tools, and data analytics platforms, highlighting their roles, features, benefits, and implementation strategies.
Key Topics:
- Technology Leadership and Vision: Developing a technology vision, strategic planning, and leadership for effective technology integration and management.
- Educational Management Information Systems (EMIS): Managing administrative and operational tasks, student information, faculty and staff management, curriculum and course management, and financial management.
- Learning Management Systems (LMS): Creating, delivering, managing, and tracking educational content and resources for teaching and learning.
- School Management Software: Managing admissions, enrollment, attendance, scheduling, parent and stakeholder engagement, reporting, and analytics.
- Communication and Collaboration Tools: Facilitating effective communication, collaboration, networking, and community engagement among stakeholders.
- Data Analytics and Decision-Making: Utilizing data analytics and insights for informed decision-making, assessment, and continuous improvement.
Features:
- Practical Insights: Real-world examples, case studies, and scenarios illustrating the application and impact of technology and information systems in educational management.
- Best Practices: Strategies, recommendations, and best practices for integrating and managing technology and information systems effectively.
- Guidance and Resources: Tools, resources, templates, and guides to support planning, implementation, and evaluation of technology initiatives.
- Reflection and Discussion Questions: Thought-provoking questions and reflection activities to facilitate deeper understanding, discussion, and application of concepts.
"Digital Transformation in Education" offers a comprehensive and insightful exploration of the transformative potential of technology and information systems in educational management. By providing practical insights, strategies, best practices, and resources, this book empowers educators, administrators, technology leaders, policymakers, and stakeholders to leverage technology effectively to enhance educational management, improve teaching and learning experiences, foster collaboration and communication, and achieve excellence and success in the 21st century.
Whether you are a seasoned educator, a technology enthusiast, or a curious stakeholder, "Digital Transformation in Education" will guide you on a transformative journey to understand, embrace, and harness the power of technology and information systems to shape the future of education and empower learners to succeed in the digital age.
Platforms
Hardware
A hardware platform can refer to an instruction set architecture. For example: ARM or the x86 architecture. These machines can run different operating systems. Smartphones and tablets generally run ARM architecture, these often run Android or iOS and other mobile operating systems.
In computer science, an instruction set architecture (ISA) is a part of the abstract model of a computer, which generally defines how software controls the CPU.[1] A device that executes instructions described by that ISA, such as a central processing unit (CPU), is called an implementation.
ARM, x86, and x64 are different architectures used in the design of microprocessors and CPUs. Each architecture has its own set of characteristics, advantages, and target applications. Here's a comparison between ARM, x86, and x64 architectures based on various factors:
ARM Architecture:
- Design Philosophy: ARM (Advanced RISC Machine) is based on Reduced Instruction Set Computing (RISC) design philosophy, focusing on simplicity, efficiency, and low power consumption.
- Power Efficiency: ARM architectures are known for their power efficiency, making them popular choices for mobile devices, embedded systems, and IoT (Internet of Things) devices.
- Customization: ARM architectures allow for greater customization, enabling manufacturers to design chips tailored to specific requirements and applications.
- Scalability: ARM architectures offer scalability from low-power microcontrollers to high-performance servers, catering to a wide range of devices and applications.
- Licensing Model: ARM Holdings licenses its architecture to other semiconductor companies, allowing them to design and manufacture ARM-based chips.
x86 Architecture:
- Design Philosophy: x86 architecture is based on Complex Instruction Set Computing (CISC) design philosophy, focusing on versatility, performance, and compatibility with legacy software.
- Performance: x86 architectures are known for their high performance, making them popular choices for desktops, laptops, workstations, and servers.
- Compatibility: x86 architectures offer backward compatibility with legacy software and applications, ensuring seamless transition and support for older systems.
- Market Dominance: Intel and AMD are the major players in the x86 market, dominating the desktop, laptop, and server markets with their respective CPU architectures.
- Power Consumption: x86 architectures typically consume more power compared to ARM architectures, making them less suitable for battery-powered devices and mobile applications.
x64 Architecture (x86-64 or AMD64):
- Extension of x86: x64 architecture is an extension of the x86 architecture, introducing 64-bit addressing, registers, and instructions to overcome the limitations of the 32-bit x86 architecture.
- Memory Addressing: x64 architecture supports larger memory addressing (up to 18.4 million TB), enabling better performance for memory-intensive applications and workloads.
- Compatibility: x64 architecture maintains backward compatibility with 32-bit x86 software, allowing users to run both 32-bit and 64-bit applications on x64 systems.
- Performance: x64 architecture offers improved performance for computational tasks, data processing, and multimedia applications compared to 32-bit x86 architecture.
- Adoption: x64 architecture has been widely adopted in desktops, laptops, servers, and workstations due to its performance benefits, compatibility, and support for larger memory capacities.
Comparison Summary
- ARM: Power-efficient, customizable, scalable, popular in mobile and embedded devices.
- x86: High performance, backward compatibility, dominant in desktop, laptop, and server markets.
- x64: 64-bit extension of x86, supports larger memory addressing, improved performance, backward compatibility with 32-bit x86 software.
In conclusion, the choice between ARM, x86, and x64 architectures depends on the specific requirements, applications, and target markets of the devices or systems being designed. While ARM architectures are preferred for power-efficient and mobile applications, x86 architectures dominate the desktop and server markets, and x64 architecture offers improved performance and larger memory addressing for high-end computing and workloads.
Software
A software platform can be either an operating system (OS) or programming environment, though more commonly it is a combination of both. Some of the popular software platforms are:
- Android (ARM64)
- ChromeOS (ARM32, ARM64, IA-32, x86-64)
- Microsoft Windows (IA-32, x86-64, ARM, ARM64)
- Common Language Infrastructure (CLI) by Microsoft, implemented in:
- The legacy .NET Framework that works only on Microsoft Windows.
- The newer .NET framework (simply called ".NET") that works across Microsoft Windows, macOS, and Linux.
- Other implementations such as Mono (formerly by Novell and Xamarin[5])
- iOS (ARMv8-A)
- Linux ( Alpha, ARC, ARM, C-Sky, Hexagon, IA-64, LoongArch, m68k, Microblaze, MIPS, Nios II, OpenRISC, PA-RISC, PowerPC, RISC-V, s390, SuperH, SPARC, x86, Xtensa)
- macOS x86, ARM (Apple silicon)
- PlayStation 4 (x86), PlayStation 3 (PowerPC) and PlayStation Vita (ARM)
- Xbox
Windows, Linux, and macOS are three major operating systems that are widely used across various platforms, each with its own strengths, weaknesses, and unique features. Let's compare these operating systems across different criteria to help you understand their differences and determine which one may be best suited for your needs:
Windows: Windows is a proprietary and commercial operating system developed and distributed by Microsoft, offering a user-friendly, familiar, and integrated platform for desktops, laptops, and servers.
Strengths:
- User-Friendly: Known for its user-friendly interface and ease of use, making it accessible for beginners.
- Software Compatibility: Extensive support for software and applications, including popular productivity tools, games, and business software.
- Hardware Support: Broad hardware support, making it compatible with a wide range of devices and peripherals.
Weaknesses:
- Security: Historically more susceptible to malware, viruses, and security vulnerabilities compared to Linux and macOS.
- Cost: Licensing fees for commercial versions, although Windows 10 offers a free upgrade from older versions.
Key Features:
- DirectX: Leading graphics technology for gaming and multimedia applications.
- Cortana: Built-in virtual assistant for voice commands and search.
- Windows Subsystem for Linux (WSL): Allows running Linux distributions alongside Windows.
- User Interface: Provides a graphical user interface (GUI) and experience with intuitive navigation, controls, and interactions.
- Compatibility: Ensures broad application, hardware, and software compatibility, integration, and support.
- Productivity: Offers productivity tools, applications, and services, such as Microsoft Office, for personal and business use.
- Security: Includes built-in security features, updates, and protections against threats, malware, and vulnerabilities.
Linux: Linux is a free, open-source, and community-driven operating system based on the Linux kernel, offering a customizable, secure, and robust platform for desktops, servers, and embedded systems.
All packages that are included in the official Debian distribution are free according to the Debian Free Software Guidelines. This assures free use and redistribution of the packages and their complete source code. The official Debian distribution is what is contained in the main section of the Debian archive. As a service to our users, we also provide packages in separate sections that cannot be included in the main distribution due to either a restrictive license or legal issues. They include:
- Contrib: Packages in this area are freely licensed by the copyright holder but depend on other software that is not free.
- Non-Free: Packages in this area have some onerous license condition restricting use or redistribution of the software.
- Non-Free-Firmware: This section is restricted to device firmware. While packages in this area basically have the same underlying license restrictions as those in non-free, a special exception has been made for them: even if not being DFSG-free, packages from non-free-firmware are allowed to be included in the official installation images.
Strengths:
- Customization: Highly customizable with various distributions (distros) tailored for different user needs and preferences.
- Security: Generally more secure and less susceptible to malware and viruses compared to Windows.
- Open Source: Open-source nature promotes transparency, collaboration, and community-driven development.
Weaknesses:
- User-Friendly: Some distributions may have a steeper learning curve for beginners compared to Windows and macOS.
- Software Compatibility: Limited support for some commercial software and games, although compatibility has improved over the years.
Key Features:
- Package Managers: Centralized software repositories and package managers (e.g., apt, yum) for easy software installation and updates.
- Terminal: Powerful command-line interface (CLI) for system management and automation.
- Open-Source: Provides access to source code, enabling customization, modification, and distribution of Linux distributions and solutions.
- Security: Offers built-in security features, permissions, and access controls to protect against vulnerabilities, threats, and attacks.
- Flexibility: Supports diverse hardware, architectures, and platforms, including servers, workstations, and embedded devices.
- Stability: Ensures reliability, uptime, and performance through stable and mature releases, updates, and support.
MacOS:
Strengths:
- Integration: Seamless integration with other Apple devices, services, and ecosystem.
- User Experience: Known for its intuitive user interface, design aesthetics, and user experience.
- Security: Generally secure with a strong focus on privacy and security features.
Weaknesses:
- Cost: Apple hardware and macOS can be more expensive compared to Windows and Linux alternatives.
- Software Compatibility: Limited support for some gaming and professional software compared to Windows.
Key Features:
- Continuity: Features like Handoff, Continuity Camera, and Universal Clipboard for seamless device integration.
- App Store: Official App Store for easy software and app installation.
- Time Machine: Built-in backup and restore solution for data protection.
- Design and Experience: Delivers a unique and seamless user experience with a stylish and intuitive interface, design, and aesthetics.
- Integration: Enables seamless integration and synchronization with Apple ecosystem, services, and devices, such as iPhone, iPad, and Apple Watch.
- Productivity: Provides productivity tools, applications, and services, such as iWork and iCloud, for personal and professional use.
- Security: Ensures robust security, privacy, and protection through built-in features, updates, and safeguards against threats and vulnerabilities.
Conclusion:
- Windows: Best for users who prioritize software compatibility, ease of use, and a broad range of hardware support.
- Linux: Ideal for users who prefer customization, open-source software, security, and a diverse range of distributions tailored for different needs.
- macOS: Suitable for users deeply integrated into the Apple ecosystem, value design aesthetics, user experience, and prioritize privacy and security.
Your choice of operating system will depend on your specific needs, preferences, and priorities. Consider factors such as software compatibility, customization, security, user experience, hardware support, and ecosystem integration when choosing between Windows, Linux, and macOS. Each operating system has its own strengths and weaknesses, so it's important to choose the one that best aligns with your requirements and enhances your productivity and user experience.
Web-Based Platforms: Web-based platforms refer to software, applications, tools, and services that operate, run, and perform on web browsers and internet-connected devices, providing access to cloud-based, online, and web-hosted solutions.Features:
- Accessibility: Enables universal access, availability, and usability across devices, platforms, and locations via web browsers and internet connectivity.
- Collaboration: Facilitates collaboration, communication, and sharing through web-based tools, platforms, and services.
- Integration: Supports integration with various web technologies, APIs, and services to enhance functionality, interoperability, and connectivity.
Mobile-Based:
Mobile-based platforms refer to software, applications, tools, and services that operate, run, and perform on mobile devices, such as smartphones and tablets, providing access to mobile apps, services, and experiences. Features:
- Portability: Enables portability, mobility, and on-the-go access to mobile apps, services, and content anytime and anywhere.
- Integration: Supports integration with mobile technologies, sensors, and functionalities to enhance functionality, user experience, and interaction.
- Optimization: Ensures optimization, responsiveness, and performance of mobile apps and services on diverse mobile devices, screen sizes, and resolutions.
Linux, Windows, macOS, web-based, and mobile-based platforms offer diverse, comprehensive, and interconnected computing, communication, and collaboration environments and experiences for users, developers, and organizations in the digital age. By leveraging the unique features, capabilities, and advantages of these platforms, individuals and businesses can create, deploy, manage, and use software, applications, and services across desktops, browsers, mobile devices, and environments to optimize, innovate, and succeed in the dynamic and competitive digital landscape of today's world. Each platform has its strengths, opportunities, and challenges, requiring careful consideration, planning, strategy, and management to maximize value, performance, and success across platforms, technologies, and ecosystems.
Cross-Platform
Cross-platform refers to the ability of software, applications, tools, technologies, and solutions to operate, run, and perform consistently and seamlessly across multiple operating systems, platforms, devices, architectures, and environments, without requiring modifications, adaptations, or customizations for each specific platform. Cross-platform development and compatibility enable users, developers, and organizations to create, deploy, manage, and use software and applications on different platforms, such as Windows, macOS, Linux, iOS, Android, web browsers, and cloud environments, to reach a broader audience, maximize market reach, reduce development costs, and enhance user experience and satisfaction.
Advantages of Cross-Platform:
- Wide Market Reach: Multi-Platform Support: Enables deployment and distribution of software and applications across various platforms, devices, and environments to reach a wider audience and user base.
- Cost-Efficiency and Time Savings: Unified Development: Facilitates unified and streamlined development, coding, and maintenance of software and applications for multiple platforms to reduce development costs, time, and efforts.
- Consistency and User Experience: Unified User Experience: Provides consistent, seamless, and uniform user experience, interface, and interaction across different platforms and devices to enhance user satisfaction and loyalty.
- Flexibility and Adaptability: Platform Agility: Enables flexibility, adaptability, and scalability to adapt and optimize software and applications for evolving platforms, technologies, and market demands.
- Market Agility and Competitive Advantage: Quick Deployment: Supports quick, efficient, and simultaneous deployment and updates of software and applications across platforms to respond to market demands, trends, and competition effectively.
- Maintenance and Support: Unified Maintenance: Simplifies and centralizes maintenance, updates, and support of software and applications for multiple platforms to ensure consistency, reliability, and performance across environments.
Challenges of Cross-Platform:
-
Performance and Optimization:
- Platform Differences: Requires optimization, tuning, and adaptation of software and applications to address performance differences, constraints, and limitations across platforms.
-
Compatibility and Integration:
- Platform Variability: Faces challenges in ensuring compatibility, integration, and interoperability with diverse platforms, technologies, and ecosystems.
-
User Experience and Interface:
- Design Consistency: Encounters difficulties in maintaining design consistency, usability, and accessibility across different platforms, devices, and screen sizes.
-
Development Complexity:
- Technical Challenges: Involves technical complexity, challenges, and learning curves in cross-platform development, debugging, testing, and deployment.
In summary, cross-platform development and compatibility offer numerous advantages and opportunities for users, developers, and organizations to create, deploy, manage, and use software and applications across multiple platforms, devices, and environments. By leveraging cross-platform technologies, tools, frameworks, and solutions, organizations can reach a wider audience, maximize market reach, reduce development costs, enhance user experience and satisfaction, and achieve competitive advantage and growth in the dynamic and diverse digital landscape of today's world. However, cross-platform development also presents challenges and complexities that require careful planning, strategy, design, optimization, and management to address and overcome effectively to ensure success, performance, and quality across platforms and ecosystems.
Computer networks
Computer networks offer numerous advantages that facilitate communication, collaboration, resource sharing, data transmission, and efficient operations for individuals, organizations, and businesses. Below are some of the key advantages of computer networks:
Advantages of Computer Networks:
-
Communication and Collaboration:
- Real-Time Communication: Enables real-time communication and collaboration between users, devices, and systems, regardless of their location and distance.
- Remote Access and Mobility: Facilitates remote access, mobility, and flexibility, allowing users to access and collaborate on resources, files, and applications from anywhere and anytime.
-
Resource Sharing and Management:
- Resource Sharing: Enables efficient and effective sharing and utilization of hardware, software, data, files, printers, and storage devices across the network.
- Centralized Management: Facilitates centralized management, administration, monitoring, and control of network resources, devices, and operations.
-
Data Transmission and Sharing:
- Data Transfer and Sharing: Enables fast, reliable, and secure data transmission, transfer, and sharing between devices, systems, and locations.
- Data Backup and Recovery: Facilitates data backup, storage, recovery, and protection, ensuring data integrity, availability, and security.
-
Cost-Effective and Scalable:
- Cost-Effective: Reduces costs associated with hardware, software, maintenance, and operations by utilizing shared resources, infrastructure, and services.
- Scalability and Flexibility: Enables easy and cost-effective network expansion, scaling, and adaptation to accommodate growing needs, changes, and requirements.
-
Efficient Operations and Productivity:
- Operational Efficiency: Improves operational efficiency, productivity, and performance by automating tasks, processes, and workflows across the network.
- Collaboration Tools and Applications: Facilitates collaboration, teamwork, and innovation by providing access to collaboration tools, applications, and platforms.
-
Security and Protection:
- Network Security: Enhances network security, protection, and defense against cyber threats, attacks, vulnerabilities, and risks by implementing security measures, protocols, and solutions.
- Data Privacy and Confidentiality: Ensures data privacy, confidentiality, and compliance with regulations, standards, and policies by implementing encryption, authentication, and access controls.
-
Integration and Compatibility:
- System Integration: Enables seamless integration, interoperability, and compatibility between different devices, systems, platforms, and technologies across the network.
- Unified Communication: Facilitates unified communication and integration of voice, video, messaging, and collaboration tools and services.
In summary, computer networks offer numerous advantages that enhance communication, collaboration, resource sharing, data transmission, and efficient operations for individuals, organizations, and businesses in the digital age. By leveraging the power and capabilities of computer networks, users, devices, and systems can connect, communicate, collaborate, share, transfer, manage, and protect data, resources, and operations effectively and efficiently across different locations, devices, and platforms. Embracing and adopting computer networks enables individuals, organizations, and businesses to leverage technology, innovation, and connectivity to drive growth, productivity, competitiveness, and success in the digital economy and society.
Types of area networks
Computer networks come in various types, each designed to meet specific needs, requirements, and purposes. The classification of computer networks is based on their size, geographical coverage, topology, and technologies used. Let's explore some of the common types of computer networks:
1. Local Area Network (LAN)
Definition: A Local Area Network (LAN) is a network that connects devices within a limited geographical area, such as a home, office building, or campus.
Characteristics:
- Size: Small geographical area (e.g., a building or campus).
- Topology: Common topologies include bus, ring, star, and mesh.
- Purpose: Facilitates communication, sharing of resources, and collaboration among devices within the same location or organization.
3. Metropolitan Area Network (MAN)
Definition: A Metropolitan Area Network (MAN) is a network that connects devices within a metropolitan area or city.
Characteristics:
- Size: Covers a larger geographical area than LAN but smaller than WAN (e.g., a city or metropolitan area).
- Topology: Utilizes a combination of LAN and WAN technologies and topologies.
- Purpose: Supports communication, connectivity, and collaboration within a metropolitan area or city.
2. Wide Area Network (WAN)
Definition: A Wide Area Network (WAN) is a network that connects devices across a wide geographical area, such as cities, countries, or continents.
Characteristics:
- Size: Large geographical area (e.g., cities, countries, or continents).
- Topology: Often uses public or private telecommunications infrastructure.
- Purpose: Enables communication and connectivity between different locations, branches, or organizations over long distances.
4. Personal Area Network (PAN)
Definition: A Personal Area Network (PAN) is a network that connects personal devices within a short range, typically within a person's workspace or personal space.
Characteristics:
- Size: Very small geographical area (e.g., a room or personal space).
- Topology: Typically wireless technologies such as Bluetooth or Infrared.
- Purpose: Enables connectivity and communication between personal devices, such as smartphones, laptops, tablets, and wearable devices.
In summary, These are some of the common types of computer networks, each designed to meet specific needs, requirements, and purposes. Organizations and individuals can choose and implement the appropriate type(s) of networks based on their size, geographical coverage, topology, technologies, and objectives to enable effective communication, connectivity, collaboration, sharing of resources, and secure access across devices, locations, and users in the dynamic and evolving digital landscape.
Types of network connections
Networking connections can be broadly categorized into two main types: wired connections and wireless connections. Each type has its own advantages, disadvantages, and suitable use cases based on specific requirements, environments, and scenarios.
Wired Connection:
Definition: Wired connections involve connecting devices and systems using physical cables or wires, such as Ethernet cables, to establish a network and enable communication, data exchange, and resource sharing between devices, networks, and systems.
Advantages:
- Reliability: Wired connections offer more stable and reliable connectivity compared to wireless connections, reducing the risk of interference, signal loss, and disconnection.
- Speed: Wired connections typically provide higher data transfer speeds and bandwidth compared to wireless connections, supporting faster and more efficient data transmission, communication, and collaboration.
- Security: Wired connections are generally more secure and less susceptible to unauthorized access, eavesdropping, and cyberattacks compared to wireless connections.
- Consistency: Wired connections provide consistent and predictable performance, latency, and reliability without fluctuations and variability.
Disadvantages:
- Flexibility: Wired connections limit mobility and flexibility due to the physical constraints of cables and wires, restricting device movement, placement, and portability.
- Installation and Maintenance: Wired connections require installation, configuration, and maintenance of cables, connectors, and networking equipment, which can be complex, time-consuming, and costly.
- Scalability: Wired connections may require additional cables, connectors, and equipment to expand and scale the network, increasing complexity and costs.
- Aesthetics: Wired connections can result in cable clutter, mess, and visual clutter, affecting the aesthetics and appearance of the workspace and environment.
Wireless Connection:
Definition: Wireless connections involve connecting devices and systems using wireless technologies, such as Wi-Fi, Bluetooth, and cellular networks, to establish a network and enable communication, data exchange, and resource sharing between devices, networks, and systems without the need for physical cables or wires.
Advantages:
- Flexibility: Wireless connections offer mobility and flexibility, allowing devices to be moved, placed, and used in different locations and environments without the constraints of cables and wires.
- Installation and Maintenance: Wireless connections eliminate the need for cables, connectors, and physical infrastructure, simplifying installation, configuration, and maintenance.
- Scalability: Wireless connections support easy and cost-effective network expansion and scalability without the need for additional cables, connectors, and equipment.
- Aesthetics: Wireless connections result in a clean, clutter-free, and visually appealing environment without the mess, clutter, and visual clutter of cables and wires.
Disadvantages:
- Reliability: Wireless connections may experience interference, signal loss, and connectivity issues due to environmental factors, distance, obstacles, and interference from other devices and networks, affecting reliability and performance.
- Speed: Wireless connections typically offer lower data transfer speeds and bandwidth compared to wired connections, limiting data transmission, communication, and collaboration efficiency.
- Security: Wireless connections are more susceptible to unauthorized access, eavesdropping, and cyberattacks compared to wired connections, requiring robust security measures, encryption, and protection.
- Battery Life: Wireless devices and systems rely on battery power, which may require frequent charging, replacement, and management, affecting usability and convenience.
In summary, wired connections and wireless connections are two main types of networking connections used to establish networks, enable communication, and support collaboration between devices, systems, and networks. While wired connections offer advantages in terms of reliability, speed, security, and consistency but may have limitations in terms of flexibility, installation, maintenance, scalability, and aesthetics, wireless connections offer advantages in terms of flexibility, installation, maintenance, scalability, and aesthetics but may have limitations in terms of reliability, speed, security, and battery life. Organizations, businesses, and individuals can choose and implement the appropriate networking connections and technologies based on their specific requirements, environments, and scenarios to establish reliable, secure, high-performance, and efficient networks to support their communication, collaboration, and operational needs in the digital age.
Types of network topologies
Computer network topology refers to the arrangement or configuration of various elements, devices, and connections in a computer network. The network topology defines how devices and systems are connected, organized, and structured within a network, determining the communication, data transmission, and collaboration capabilities of the network.
Types of Computer Network Topologies:
-
Star Topology:
- Description: In a star topology, each device is connected to a central hub or switch, forming a centralized or hub-and-spoke structure.
- Advantages:
- Centralized management and control.
- Easy to install, configure, and troubleshoot.
- Fault isolation and scalability.
- Disadvantages:
- Dependency on the central hub or switch.
- Single point of failure.
- Limited scalability and expansion.
-
Bus Topology:
- Description: In a bus topology, devices are connected to a single communication line or backbone, forming a linear or daisy-chain structure.
- Advantages:
- Simple and cost-effective.
- Easy to install and expand.
- Flexible and versatile.
- Disadvantages:
- Limited scalability and bandwidth.
- Single point of failure.
- Difficult to troubleshoot and identify faults.
-
Ring Topology:
- Description: In a ring topology, devices are connected in a circular or ring structure, where each device is connected to two neighboring devices.
- Advantages:
- Balanced data traffic and load distribution.
- Redundancy and fault tolerance.
- Data transmission and communication efficiency.
- Disadvantages:
- Single point of failure.
- Difficult to troubleshoot and reconfigure.
- Limited scalability and expansion.
-
Mesh Topology:
- Description: In a mesh topology, devices are interconnected with multiple paths and links, forming a fully interconnected or mesh structure.
- Advantages:
- Redundancy and fault tolerance.
- High reliability and availability.
- Scalability and flexibility.
- Disadvantages:
- Complexity and cost.
- Difficult to install, manage, and troubleshoot.
- Bandwidth consumption and efficiency.
-
Hybrid Topology:
- Description: A hybrid topology is a combination of two or more types of topologies, such as star-ring, star-bus, or mesh-bus, to form a more flexible and versatile network structure.
- Advantages:
- Flexibility and scalability.
- Redundancy and fault tolerance.
- Balanced performance and efficiency.
- Disadvantages:
- Complexity and cost.
- Difficult to design, implement, and manage.
- Limited standardization and compatibility.
In summary, Computer network topology plays a crucial role in defining the structure, organization, and communication capabilities of a computer network, determining how devices and systems are connected, organized, and structured within the network. Each type of network topology, such as star, bus, ring, mesh, and hybrid topologies, offers unique advantages, disadvantages, characteristics, and suitable use cases based on specific requirements, environments, and scenarios. Organizations, businesses, and individuals can choose and implement the appropriate network topology based on their specific needs, requirements, budget, and preferences to establish a reliable, secure, high-performance, and efficient network to support their communication, collaboration, and operational needs in the digital age.
Types of Network Protocols
Network protocols are a set of rules and standards that govern the communication and data exchange between devices, systems, and networks. Common network protocols, such as IP, HTTP, HTTPS, FTP, SCP, POP3, IMAP, and SMTP, facilitate various types of communication, data transmission, and services across the internet and computer networks.
IP (Internet Protocol): IP is a fundamental network protocol that enables data packets to be transmitted and routed between devices and networks on the internet and computer networks. IP, which stands for Internet Protocol, is a set of rules and protocols that govern how data packets are addressed, transmitted, routed, and received over the Internet and other networks. IP is a fundamental protocol in the Internet protocol suite, which also includes TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and others.
Function: IP addresses, routes, and delivers data packets between source and destination devices, ensuring reliable and efficient communication.
Key Characteristics:
- Addressing: Every device connected to a network, including the Internet, is assigned a unique IP address (e.g., IPv4 or IPv6) to identify and locate it on the network.
- Packet Routing: IP facilitates the routing of data packets between source and destination devices, networks, and domains across the Internet.
- Version: IPv4 (Internet Protocol version 4) and IPv6 (Internet Protocol version 6) are the two main versions of IP addressing used today.
Usage:
- Data Transmission: IP is used to transmit and route data packets between devices, networks, and domains.
- Addressing: IP addresses are used to identify and locate devices on networks and the Internet.
- Networking: IP is fundamental to network communication, connectivity, and interoperability.
HTTP (HyperText Transfer Protocol): HTTP (HyperText Transfer Protocol) is a network protocol used for transmitting and retrieving web content, such as web pages, documents, and media, over the internet. HTTP facilitates communication between web browsers and web servers, enabling users to access and interact with websites and web applications.
HTTPS (HTTP Secure): HTTPS (HTTP Secure) is a secure and encrypted version of HTTP, providing secure and private communication and data transmission between web browsers and web servers.HTTPS encrypts and protects sensitive data, such as personal information, passwords, and financial details, from eavesdropping, interception, and cyberattacks.
FTP (File Transfer Protocol): FTP (File Transfer Protocol) is a network protocol used for transferring and sharing files between devices and servers on the internet and computer networks. FTP enables users to upload, download, and manage files and directories on remote servers, facilitating file sharing, synchronization, and backup.
SCP (Secure Copy Protocol): SCP (Secure Copy Protocol) is a secure and encrypted file transfer protocol that enables secure and reliable file copying and transfer between devices and servers. SCP provides secure and private file transfer and synchronization, ensuring data integrity, confidentiality, and protection.
POP3 (Post Office Protocol version 3): POP3 (Post Office Protocol version 3) is a network protocol used for retrieving and downloading emails from a remote email server to a local email client or device. POP3 enables users to access and manage emails on their devices, such as computers, smartphones, and tablets, by downloading emails from the email server.
IMAP (Internet Message Access Protocol): IMAP (Internet Message Access Protocol) is a network protocol used for accessing and managing emails stored on a remote email server from multiple devices and locations. IMAP synchronizes and maintains email folders, messages, and statuses across devices and email clients, enabling seamless and consistent email access and management.
SMTP (Simple Mail Transfer Protocol): SMTP (Simple Mail Transfer Protocol) is a network protocol used for sending and transmitting emails from a sender's email client or device to a recipient's email server. SMTP facilitates the transmission and delivery of emails between email servers and across networks, ensuring reliable and efficient email communication and delivery.
In summary, common network protocols, such as IP, HTTP, HTTPS, FTP, SCP, POP3, IMAP, and SMTP, play a crucial role in facilitating various types of communication, data transmission, and services across the internet and computer networks. Each network protocol serves specific functions and purposes, enabling users, devices, and systems to communicate, access, share, transfer, and manage data, content, and resources effectively and efficiently. Understanding and utilizing common network protocols enables individuals, organizations, and businesses to leverage the power and capabilities of the internet and computer networks to support their communication, collaboration, and operational needs in the digital age.
ISP (Internet Service Provider)
Definition: An Internet Service Provider (ISP) is a company or organization that provides Internet access, services, and connectivity to individuals, businesses, organizations, and other service providers. ISPs connect customers to the Internet through various technologies, such as dial-up, DSL, cable modem, fiber-optic, wireless, and satellite connections.
Key Characteristics:
- Internet Access: ISPs offer various Internet access plans, packages, and technologies to connect customers to the Internet.
- Services: Besides Internet access, ISPs may offer additional services, such as email, web hosting, domain registration, and online storage.
- Infrastructure: ISPs maintain and manage the infrastructure, network, equipment, and resources required to provide Internet services and connectivity.
- Peering and Transit: ISPs establish peering and transit agreements with other ISPs and networks to exchange traffic and access the global Internet.
Usage:
- Internet Access: ISPs provide Internet connectivity to homes, businesses, organizations, and other customers.
- Services: ISPs offer a range of Internet services, packages, plans, and additional services to meet customer needs and requirements.
- Connectivity: ISPs ensure reliable, high-speed, and secure Internet connectivity and access for customers to browse the web, send and receive emails, stream media, and access online services and applications.
In summary, IP (Internet Protocol) is a fundamental protocol that governs how data packets are addressed, transmitted, routed, and received over the Internet and other networks, while an ISP (Internet Service Provider) is a company or organization that provides Internet access, services, and connectivity to customers. IP addresses uniquely identify and locate devices on networks and the Internet, facilitating data transmission and routing, while ISPs connect customers to the Internet through various technologies, offering Internet access, services, and connectivity. Both IP and ISPs play crucial roles in enabling Internet communication, connectivity, access, and services for individuals, businesses, organizations, and other entities in the digital age.
Domain name
A domain name is an identification string that defines a realm of administrative autonomy, authority or control within the Internet. Domain names are used in various networking contexts and for application-specific naming and addressing purposes. In general, a domain name identifies a network domain, or it represents an Internet Protocol (IP) resource, such as a personal computer used to access the Internet, a server computer hosting a website, or the web site itself or any other service communicated via the Internet.
Domain names are formed by the rules and procedures of the Domain Name System (DNS). Any name registered in the DNS is a domain name. Domain names are organized in subordinate levels (subdomains) of the DNS root domain, which is nameless. The first-level set of domain names are the top-level domains (TLDs), including the generic top-level domains (gTLDs), such as the prominent domains com, info, net, edu, and org, and the country code top-level domains (ccTLDs). Below these top-level domains in the DNS hierarchy are the second-level and third-level domain names that are typically open for reservation by end-users who wish to connect local area networks to the Internet, create other publicly accessible Internet resources or run web sites.
Uniform Resource Locator (URL)
A URL (Uniform Resource Locator) is a web address that specifies the location of a resource on the internet, such as a website, web page, file, or service. A URL is composed of several parts that identify and describe the location, protocol, domain, path, and parameters of the resource.
Parts of a URL:
-
Protocol:
- Definition: The protocol specifies the method or protocol used to access and retrieve the resource, such as HTTP (HyperText Transfer Protocol), HTTPS (HTTP Secure), FTP (File Transfer Protocol), or FTPS (FTP Secure).
- Example: http://, https://, ftp://, ftps://
-
Domain Name:
- Definition: The domain name identifies the website or server where the resource is hosted, representing the human-readable name associated with the IP address of the server.
- Example: www.example.com, example.com, subdomain.example.com
- A Top-Level Domain (TLD) is the highest level in the hierarchical Domain Name System (DNS) structure, representing the last segment of a domain name. TLDs are categorized into various types, including generic top-level domains (gTLDs), country code top-level domains (ccTLDs), and sponsored top-level domains (sTLDs).
- 1. Generic Top-Level Domains (gTLDs)
- Definition: Generic Top-Level Domains (gTLDs) are a category of TLDs that are not associated with specific countries or territories. gTLDs are commonly used by organizations, businesses, and individuals worldwide to register domain names for various purposes, including websites, applications, and services.
- Examples of gTLDs:
- .com (commercial)
- .org (organization)
- .net (network)
- .info (information)
- .biz (business)
- .gov (government)
- .edu (education)
- .mil (military)
- 2. Country Code Top-Level Domains (ccTLDs)
- Definition: Country Code Top-Level Domains (ccTLDs) are a category of TLDs that are associated with specific countries or territories, representing the two-letter country code assigned to each country or territory by the International Organization for Standardization (ISO). Examples of ccTLDs:
- .ir (Iran)
- .ru (Russia)
- .us (United States)
- .uk (United Kingdom)
- .de (Germany)
- .fr (France)
- .jp (Japan)
- .cn (China)
- .au (Australia)
- .ca (Canada)
- .in (India)
- 3. Sponsored Top-Level Domains (sTLDs): Sponsored Top-Level Domains (sTLDs) are a category of TLDs that are sponsored by specific organizations, communities, or groups to serve a particular community, industry, or interest. sTLDs are managed and operated by the sponsoring organization or community to ensure that the domain names registered under the sTLD meet specific criteria, requirements, and purposes. Examples of sTLDs:
- .aero (aviation industry)
- .coop (cooperatives)
- .museum (museums)
- .edu (education institutions in the United States)
- .gov (U.S. government entities)
- .int (international organizations)
- .mil (U.S. military entities)
- .post (postal services)
- In summary, Domain Name TLDs (Top-Level Domains) include Generic Top-Level Domains (gTLDs), Country Code Top-Level Domains (ccTLDs), and Sponsored Top-Level Domains (sTLDs), each serving different purposes, requirements, and audiences in the domain name system. gTLDs are generic TLDs used worldwide for various purposes, ccTLDs are country-specific TLDs associated with specific countries or territories, and sTLDs are sponsored TLDs sponsored by specific organizations or communities for particular industries, interests, or communities. Organizations, businesses, and individuals can choose and register domain names under the appropriate TLD based on their location, audience, industry, and purpose to establish their online presence, identity, and branding effectively and efficiently in the digital age.
-
Subdomain:
- Definition: The subdomain is a subdivision or subset of the domain, representing a specific section, department, or service within the main domain.
- Example: www (world wide web), blog, shop, mail
-
Path:
- Definition: The path specifies the location and directory structure of the resource on the server, representing the file or folder hierarchy and organization.
- Example: /directory/, /folder/file.html, /path/to/resource
-
Parameters:
- Definition: The parameters specify additional information, settings, or data required by the resource, such as query parameters, variables, or options.
- Example: ?key=value, ?id=123&name=example, ?search=query
-
Port:
- Definition: The port specifies the network port number used to establish the connection and access the resource on the server, typically used for non-default or specific port configurations.
- Example: :80 (HTTP), :443 (HTTPS), :21 (FTP), :22 (SSH)
-
Anchor or Fragment:
- Definition: The anchor or fragment specifies a specific section or location within the resource, such as a web page, document, or video, allowing direct navigation and access to the specified section or location.
- Example: #section, #anchor, #fragment
Example of a Complete URL:
https://www.example.com/path/to/resource?key=value#section
- Protocol: https://
- Domain Name: www.example.com
- Subdomain: www
- Path: /path/to/resource
- Parameters: ?key=value
- Anchor or Fragment: #section
In summary, a URL (Uniform Resource Locator) is composed of several parts, including the protocol, domain name, subdomain, path, parameters, port, and anchor or fragment, which identify and describe the location, access method, and additional information of the resource on the internet. Each part of the URL plays a crucial role in specifying and accessing the resource, facilitating navigation, retrieval, and interaction with websites, web pages, files, and services on the internet. Understanding and analyzing the different parts of a URL enables users, developers, and administrators to navigate, access, share, and manage web resources effectively and efficiently in the digital age.
DNS (Domain Name System)
Definition: The Domain Name System (DNS) is a hierarchical and decentralized naming system that translates domain names (e.g., www.example.com) into IP addresses (e.g., 192.0.2.1) to enable devices to locate and connect to servers and resources on the Internet. DNS plays a crucial role in Internet communication, connectivity, and interoperability by resolving domain names to IP addresses and vice versa.
Key Characteristics:
- Resolution: DNS resolves domain names to IP addresses and vice versa.
- Hierarchy: DNS operates in a hierarchical and decentralized manner, with various levels and types of DNS servers (e.g., root servers, TLD servers, authoritative servers, recursive servers).
- Caching: DNS servers cache DNS records to improve performance and speed up resolution.
- Queries: DNS servers handle DNS queries and responses to facilitate domain name resolution and connectivity.
Usage:
- Domain Name Resolution: Resolving domain names to IP addresses to enable connectivity and communication.
- Web Browsing: Translating domain names into IP addresses to access websites and web resources.
- Email Delivery: Resolving domain names to IP addresses to deliver emails and facilitate communication.
- Network Configuration: Configuring DNS settings and servers to manage domain name resolution and connectivity.
Proxy
Definition: A proxy server acts as an intermediary between a user's device (e.g., computer, smartphone) and the internet. When a user requests a web page or resource, the request is first sent to the proxy server, which then forwards the request to the target server on behalf of the user, receives the response from the server, and forwards it back to the user. Proxy servers can be used for various purposes, such as improving performance, filtering content, bypassing restrictions, and enhancing privacy and anonymity.
Key Characteristics:
- Anonymity: Proxy servers can mask the user's IP address, providing anonymity and privacy.
- Content Filtering: Proxy servers can filter and block access to specific websites, content, and resources.
- Performance: Proxy servers can cache and deliver content to users more quickly, improving performance and speed.
- Bypass Restrictions: Proxy servers can bypass geographic restrictions, censorship, and content filters.
Usage:
- Privacy and Anonymity: Using a proxy server to hide and mask the user's IP address and location.
- Content Filtering: Implementing content filtering and blocking specific websites, content, and resources.
- Performance Optimization: Caching and delivering content more quickly to users.
- Bypassing Restrictions: Accessing geo-restricted content, bypassing censorship, and content filters.
VPN (Virtual Private Network)
Definition: A Virtual Private Network (VPN) creates a secure, encrypted connection over a public network, such as the internet, enabling users to access and communicate with private networks and resources securely and privately. VPNs encrypt data to ensure confidentiality and security, mask IP addresses and locations for enhanced privacy and anonymity, and enable remote access to private networks and resources.
Key Characteristics:
- Security: VPNs encrypt data to ensure confidentiality and security during transmission.
- Privacy: VPNs mask the user's IP address and location to enhance privacy and anonymity.
- Access Control: VPNs enable remote access to private networks and resources securely.
- Bypass Restrictions: VPNs allow bypassing geographic restrictions, censorship, and content filters.
Usage:
- Remote Access: Connecting to corporate networks, resources, and applications remotely.
- Privacy and Anonymity: Enhancing privacy and anonymity when browsing the internet.
- Bypassing Restrictions: Accessing geo-restricted content, websites, and services.
In summary, Proxy, VPN, and DNS are three distinct technologies used for different purposes in Internet communication, connectivity, and services. A proxy server acts as an intermediary between a user's device and the Internet, a VPN creates a secure, encrypted connection over the Internet for remote access and privacy, and DNS translates domain names into IP addresses to enable domain name resolution and connectivity. While proxy servers can be used for content filtering, performance optimization, and bypassing restrictions, VPNs focus on security, privacy, and remote access, and DNS plays a crucial role in domain name resolution, web browsing, email delivery, and network configuration. Organizations and individuals can leverage proxy, VPN, and DNS solutions to meet their specific needs, requirements, and objectives, ensuring secure, private, and efficient Internet communication, connectivity, and services in the digital age.
Cloud Computing
Cloud computing encompasses various aspects, including architecture, service models, and business models, each playing a crucial role in delivering cloud-based solutions and services to users and organizations. Let's explore the differences and key characteristics of cloud computing architecture, cloud computing service models, and cloud business models:
Cloud Computing Architecture
Cloud computing architecture refers to the design and structure of a cloud computing environment, including the components, infrastructure, and technologies that enable the delivery of cloud services. Key aspects of cloud computing architecture include:
Infrastructure: Physical hardware resources such as servers, storage devices, networking equipment, and data centers that form the foundation of the cloud infrastructure.
Virtualization: Technologies and platforms that enable the creation and management of virtual resources, allowing multiple virtual machines (VMs) or containers to run on a single physical server.
Orchestration: Automation and management tools that coordinate and manage the provisioning, scaling, and deployment of cloud resources and services.
Security: Security measures, protocols, and technologies implemented to protect data, applications, and infrastructure in the cloud environment.
Scalability: Ability to dynamically allocate and scale resources up or down based on demand, ensuring optimal performance and cost-efficiency.
Cloud Computing Service Models
Cloud computing service models define the types of cloud services and capabilities offered to users and organizations. The three primary service models in cloud computing are:
Infrastructure as a Service (IaaS):
Provides virtualized computing resources (e.g., VMs, storage, networking) over the internet.
Users manage and control the operating systems, applications, and middleware, while the cloud provider manages the infrastructure.
Examples: Amazon Web Services (AWS) EC2, Microsoft Azure Virtual Machines, Google Compute Engine.
Platform as a Service (PaaS):
Provides platforms and development environments that enable users to develop, deploy, and manage applications without worrying about the underlying infrastructure.
Users focus on developing and managing applications, while the cloud provider manages the platform, runtime, and middleware.
Examples: Heroku, Google App Engine, Microsoft Azure App Service.
Software as a Service (SaaS):
Provides software applications and services over the internet on a subscription basis.
Users access and use the software applications via web browsers or thin clients, without needing to install or manage the software locally.
Examples: Salesforce, Microsoft Office 365, Google Workspace.
Cloud Computing Architecture: Focuses on the design, infrastructure, and technologies that enable cloud computing environments.
Cloud Computing Service Models: Define the types of cloud services (IaaS, PaaS, SaaS) and capabilities offered to users and organizations.
Together, these aspects form the foundation of cloud computing, providing the infrastructure and services that enable organizations and individuals to leverage the power of cloud technology to innovate, collaborate, and achieve their goals more efficiently and effectively.
VPS (Virtual Private Server)
Definition: A Virtual Private Server (VPS) is a virtualized server environment hosted within a physical server, where each VPS operates independently with its own dedicated resources, operating system, and environment. VPS provides users with more control, flexibility, and isolation compared to shared hosting, allowing them to customize and manage their virtual server according to their specific needs and requirements.
Key Characteristics:
- Isolation: Operates independently with dedicated resources and environment.
- Customization: Offers control, flexibility, and customization options.
- Performance: Provides better performance, stability, and reliability compared to shared hosting.
- Scalability: Allows scaling resources (e.g., CPU, RAM, storage) based on requirements.
- Management: Users are responsible for managing, configuring, and maintaining their VPS, including installing software, managing security, and performing updates.
Usage Scenarios:
- Hosting Websites and Applications: Hosting websites, web applications, and services.
- Development and Testing: Developing, testing, and deploying applications and services.
- Backup and Storage: Storing, backing up, and managing data and files.
- Control and Customization: Need for control, customization, and isolation compared to shared hosting.
Cloud Server
Definition: A Cloud Server is a virtual server hosted and managed within a cloud computing environment, where resources are dynamically provisioned and scaled based on demand. Cloud Server offers scalability, flexibility, and pay-as-you-go pricing, allowing users to deploy and manage virtual servers, applications, and services in the cloud without the need for physical hardware and infrastructure.
Key Characteristics:
- Scalability: Dynamically scales resources based on demand.
- Flexibility: Offers flexibility to choose resources, configurations, and services.
- Reliability: Provides high availability, redundancy, and fault tolerance.
- Pay-as-you-go Pricing: Offers flexible and cost-effective pricing models based on usage.
- Managed Services: Cloud providers often offer managed services, tools, and platforms to simplify management, deployment, and operations.
Usage Scenarios:
- Infrastructure as a Service (IaaS): Deploying and managing infrastructure, platforms, and services.
- Scalable Applications: Hosting scalable and dynamic web applications, services, and workloads.
- Data Backup and Recovery: Storing, backing up, and recovering data and files in the cloud.
- Collaboration and Development: Collaborating, developing, testing, and deploying applications and services in the cloud.
Differences between VPS and Cloud Server:
-
Infrastructure:
- VPS: Hosted within a physical server, offering isolated virtual environments.
- Cloud Server: Hosted within a cloud computing environment, offering scalable and flexible virtual resources.
-
Scalability:
- VPS: Limited scalability based on available resources and configurations.
- Cloud Server: Dynamic scalability, allowing resources to be scaled up or down based on demand and requirements.
-
Management:
- VPS: Users are responsible for managing, configuring, and maintaining their VPS.
- Cloud Server: Cloud providers often offer managed services, tools, and platforms to simplify management and operations.
-
Flexibility and Customization:
- VPS: Offers control, flexibility, and customization options similar to dedicated servers.
- Cloud Server: Offers flexibility to choose resources, configurations, and services, with options for customization based on cloud provider offerings.
-
Pricing:
- VPS: Typically priced based on resource allocation, configurations, and hosting providers.
- Cloud Server: Offers pay-as-you-go pricing models based on usage, resources, and configurations, with options for cost-effective scaling and management.
In summary, VPS (Virtual Private Server) and Cloud Server are two distinct hosting solutions offering different infrastructure, scalability, management, flexibility, and pricing options to meet various hosting needs and requirements. While VPS provides isolated virtual environments within physical servers with control, customization, and limited scalability, Cloud Server offers scalable and flexible virtual resources within a cloud computing environment with dynamic scalability, managed services, and pay-as-you-go pricing. Organizations and individuals can choose between VPS and Cloud Server based on their specific needs, requirements, budget, and preferences to deploy, manage, and scale their websites, applications, and services effectively and efficiently in the digital age.
Power and Potential of Open-Source
Understanding the Power and Potential of Open-Source Software
Open-source refers to a method for designing, developing, and distributing software, hardware, or other types of products or projects that emphasizes transparency, collaboration, and community-driven innovation. The term "open-source" originated from the software development model where the source code of a software program is made available to the public, allowing anyone to view, modify, and distribute the code freely.
Key Principles of Open-Source:
- Open Access: The source code of open-source projects is made available to the public, allowing users to access, study, and modify the code without restrictions.
- Transparency: Open-source projects promote transparency by providing visibility into the development process, decision-making, and code changes, fostering trust and accountability among contributors and users.
- Collaboration: Open-source encourages collaborative development and community participation, allowing individuals, developers, and organizations to work together to improve, enhance, and contribute to the project.
- Freedom: Open-source software grants users the freedom to use, modify, and distribute the software according to the terms of the open-source license, empowering individuals and organizations to adapt the software to their needs and preferences.
Movement
The Free Software Movement is a social and political movement advocating for the freedom to use, study, modify, and distribute software. Rooted in the principles of user freedom, transparency, and community-driven collaboration, the Free Software Movement aims to challenge the proprietary software model dominated by restrictive licenses, vendor lock-in, and lack of user control. Here are the key aspects and principles of the Free Software Movement:
Four Essential Freedoms
The Free Software Movement is built upon four essential freedoms, as defined by the Free Software Foundation (FSF):
- Freedom 0: The freedom to run the program as you wish, for any purpose.
- Freedom 1: The freedom to study how the program works, and change it to make it do what you wish.
- Freedom 2: The freedom to redistribute copies so you can help others.
- Freedom 3: The freedom to distribute copies of your modified versions to others.
Key Principles
- User Freedom: The Free Software Movement emphasizes the importance of user freedom, ensuring that users have the right to control and modify the software they use, rather than being controlled by proprietary software vendors.
- Transparency and Openness: Free software is developed and distributed with full access to the source code, allowing users to study, modify, and understand how the software works. This transparency fosters trust, accountability, and collaborative development.
- Community and Collaboration: The Free Software Movement values community-driven collaboration, encouraging developers, users, and contributors to work together to improve software, share knowledge, and solve problems collaboratively.
- Ethical Considerations: Beyond technical and legal considerations, the Free Software Movement also addresses ethical issues related to software freedom, intellectual property rights, digital rights, and social justice.
Free Software vs. Open Source
While the terms "Free Software" and "Open Source" are often used interchangeably, they represent different philosophies and approaches to software development:
- Free Software: Focuses on user freedom, ethical considerations, and social justice. It emphasizes the importance of software being free as in freedom, not just free as in price.
- Open Source: Focuses on practical benefits, such as collaborative development, quality software, and business advantages. It emphasizes the open development model, peer review, and shared innovation.
Organizations and Advocacy
The Free Software Movement is supported and promoted by organizations such as the Free Software Foundation (FSF), founded by Richard Stallman in 1985, and the Open Source Initiative (OSI). These organizations advocate for software freedom, educate the public about the benefits of free software, and provide resources, tools, and platforms for developers and users to participate in the movement.
Impact and Legacy
The Free Software Movement has had a significant impact on the software industry, influencing the development of open-source software, collaborative development practices, and alternative business models. It has also sparked broader discussions and debates about intellectual property rights, digital freedoms, and the role of technology in society.
In conclusion, the Free Software Movement is a grassroots movement that champions the principles of user freedom, transparency, community collaboration, and ethical considerations in software development. By advocating for the four essential freedoms and promoting the adoption of free software licenses, the movement aims to empower users, foster innovation, and build a more equitable and inclusive digital world.
Motivation
Open source motivation refers to the driving factors, values, and incentives that inspire individuals and organizations to participate in open source communities, contribute to open source projects, and advocate for the principles of open source software development. Understanding open source motivation can provide insights into why people choose to engage in collaborative, transparent, and community-driven initiatives without financial compensation.
Here are some key motivations behind open source participation:
- Community and Collaboration: Many individuals are drawn to open source communities because of the sense of belonging, camaraderie, and collaboration they offer. Working together with like-minded individuals from around the world to solve problems, build software, and share knowledge can be a rewarding and fulfilling experience.
- Learning and Skill Development: Open source projects provide opportunities for individuals to learn new technologies, programming languages, and software development practices. Contributing to open source can help developers enhance their skills, gain hands-on experience, and expand their professional networks.
- Ideological and Philosophical Beliefs: Some individuals are motivated by the principles of openness, transparency, and freedom that underlie the open source movement. They believe in the importance of open access to code, collaborative development, and community-driven innovation as a means to create better software and foster technological advancement.
- Professional Growth and Recognition: Contributing to open source projects can enhance an individual's reputation, credibility, and visibility within the software development community. Many employers value open source contributions as evidence of a developer's expertise, commitment to continuous learning, and ability to work collaboratively on complex projects.
- Problem-Solving and Innovation: Open source projects often address real-world problems and challenges that developers are passionate about solving. The opportunity to contribute to innovative solutions, create impactful software, and make a difference in the world can be a significant source of motivation for many open source contributors.
- Contribution to Common Good: Open source software is often developed and maintained for the benefit of the broader community, rather than for profit. Many individuals are motivated by the desire to contribute to the common good, improve access to technology, and empower others through open source initiatives.
- Freedom and Flexibility: Open source development offers developers the freedom and flexibility to work on projects that interest them, at their own pace, and on their own terms. This autonomy can be appealing to individuals who value independence, creativity, and self-directed learning.
- Personal Satisfaction and Fulfillment: For many open source contributors, the sense of accomplishment, personal growth, and satisfaction derived from creating, improving, or maintaining software that is used and appreciated by others can be a powerful motivator.
In conclusion, open source motivation is multifaceted and can vary widely among individuals based on their personal values, professional goals, interests, and beliefs. Whether driven by community, learning, ideology, recognition, innovation, or personal satisfaction, open source contributors play a crucial role in advancing technology, fostering collaboration, and enriching the global software ecosystem.
Economy
The Open Source Economy refers to an economic model based on the principles of open source software development, transparency, collaboration, and community-driven innovation. In an open source economy, knowledge, resources, and technologies are shared openly and collaboratively, fostering innovation, promoting accessibility, and empowering individuals and communities to participate in economic activities and value creation. Here are some key aspects and characteristics of the Open Source Economy:
Principles of Open Source Economy:
- Openness and Transparency: The Open Source Economy emphasizes transparency in processes, decision-making, and information sharing, allowing for greater accountability, trust, and collaboration among participants.
- Collaborative Innovation: Open source encourages collaborative development and innovation by enabling individuals, organizations, and communities to work together to solve problems, create new technologies, and develop innovative solutions collaboratively.
- Accessibility and Inclusion: Open source promotes accessibility by making knowledge, resources, and technologies freely available to everyone, regardless of geographical location, socioeconomic status, or organizational affiliation.
- Community Engagement: The Open Source Economy values community-driven initiatives, participation, and engagement, allowing individuals and communities to actively contribute to projects, share insights, and shape the direction of developments.
- Shared Value Creation: In an open source economy, value is created and shared collectively among participants, contributors, and stakeholders, rather than being captured and controlled by a few entities or organizations.
Key Components of Open Source Economy:
- Open Source Software: Open source software serves as a foundational element of the open source economy, providing the tools, platforms, and technologies that enable collaborative development, innovation, and value creation across various industries and sectors.
- Open Data and Open Access: Open data initiatives and open access policies promote the sharing and accessibility of data, research, and information, enabling greater transparency, collaboration, and innovation in research, education, and public services.
- Open Hardware and Manufacturing: Open hardware projects and open manufacturing practices enable individuals, makers, and businesses to design, produce, and distribute hardware products and technologies collaboratively, fostering innovation and accessibility in the hardware industry.
- Crowdfunding and Community Funding: Crowdfunding platforms and community funding initiatives enable individuals, startups, and projects to raise funds, support, and resources from a global community of backers, supporters, and contributors, facilitating the development and growth of open source projects and initiatives.
- Collaborative Platforms and Networks: Online platforms, forums, and networks dedicated to open source development, collaboration, and knowledge sharing serve as hubs and catalysts for innovation, community building, and value creation in the open source economy.
Examples of Open Source Economy Initiatives:
- Open Source Software Projects: Projects like Linux, WordPress, and Mozilla Firefox demonstrate the power of open source collaboration, innovation, and community-driven development in creating widely used and impactful software solutions.
- Open Data Initiatives: Governments, organizations, and communities worldwide are adopting open data initiatives to promote transparency, accountability, and innovation by making government data and public information accessible to everyone.
- Open Hardware and Maker Movement: Initiatives like Arduino, Raspberry Pi, and Maker Faire showcase the potential of open hardware and the maker movement in democratizing access to technology, fostering creativity, and empowering individuals to create and innovate.
- Crowdfunding Platforms: Platforms like Kickstarter, Indiegogo, and OpenCollective enable creators, innovators, and projects to raise funds, support, and resources from a global community of backers, enabling the development and growth of open source projects, products, and initiatives.
In summary, the Open Source Economy represents a paradigm shift towards a more collaborative, inclusive, and sustainable economic model that leverages the power of open source principles, technologies, and communities to drive innovation, foster creativity, and create shared value across various industries, sectors, and communities worldwide. By embracing openness, transparency, collaboration, and community engagement, the Open Source Economy offers a transformative approach to economic development, innovation, and value creation that empowers individuals, organizations, and communities to participate, contribute, and thrive in a globally connected and increasingly complex world.
Licenses
Open-source licenses are legal agreements that govern the terms and conditions under which open-source software or hardware can be used, modified, and distributed. Some popular open-source licenses include:
- GNU General Public License (GPL)
- MIT License
- Apache License
- BSD Licenses
- Creative Commons Licenses
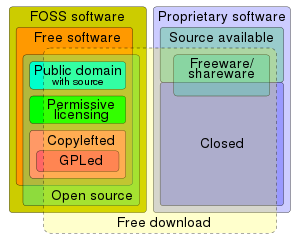
Free and open
Non-free
A software license is a legal agreement that defines the terms and conditions under which software can be used, modified, distributed, and redistributed by users or organizations. There are various types of software licenses, ranging from proprietary licenses that restrict user freedoms to free and open-source licenses that grant users the freedom to use, modify, and distribute the software freely. Here's an example of a free and open-source software (FOSS) license:
GNU General Public License (GPL)
The GNU General Public License (GPL) is one of the most widely used free software licenses, created by Richard Stallman and maintained by the Free Software Foundation (FSF). The GPL is designed to ensure that software remains free and open-source, allowing users to freely use, modify, and distribute the software and its source code.
Key Features of GPL:
- CopyLeft: The GPL uses a "Copyleft" provision, which means that derivative works must also be licensed under the GPL. This ensures that modifications and improvements to the software remain open-source and freely available to the community.
- Source Code Availability: The GPL requires that the source code of the software be made available to users, allowing them to study, modify, and understand how the software works.
- Distribution: The GPL allows users to redistribute the software and its source code freely, either in its original form or as part of a derivative work. However, any modifications or derivative works must also be licensed under the GPL.
- Commercial Use: The GPL does not restrict commercial use of the software. Users are free to use GPL-licensed software for both non-commercial and commercial purposes.
Popular FOSS Projects Licensed under GPL:
- Linux Kernel: The core component of the Linux operating system.
- WordPress: A popular content management system (CMS) for websites.
- LibreOffice: An open-source office productivity suite.
- FFmpeg: a free and open-source software project consisting of a suite of libraries and programs for handling video, audio, and other multimedia files and streams.
- GIMP: GNU Image Manipulation Program(GIMP), commonly known by its acronym GIMP, is a free and open-source raster graphics editor used for image manipulation and image editing, free-form drawing, transcoding between different image file formats, and more specialized tasks. It is extensible by means of plugins, and scriptable.
Conclusion
The GNU General Public License (GPL) is just one example of a free and open-source software (FOSS) license that embodies the principles of software freedom, transparency, and community collaboration. There are many other FOSS licenses, such as the MIT License, Apache License, BSD License, and Mozilla Public License, each with its own set of terms and conditions. When choosing a license for an open-source project, it's essential to consider the goals, values, and requirements of the project, as well as how the chosen license will impact the community of developers, contributors, and users.
Software
Open-source software (OSS) is a type of software whose source code is made available to the public under an open-source license, allowing anyone to view, modify, and distribute the software freely. Some popular examples of open-source software include:
- Linux: An open-source operating system kernel that powers various Linux distributions like Ubuntu, Fedora, and CentOS.
- Apache HTTP Server: An open-source web server software widely used to serve websites and web applications.
- Mozilla Firefox: An open-source web browser developed by the Mozilla Foundation.
- LibreOffice: An open-source office productivity suite that includes word processing, spreadsheets, presentations, and more.
- WordPress: An open-source content management system (CMS) used to create websites, blogs, and online stores.
Open-Source Hardware (OSH):
Open-source hardware (OSH) refers to the design and development of physical products, components, or devices whose design information, schematics, and documentation are made available to the public under an open-source license. Examples of open-source hardware projects include:
- Arduino: An open-source hardware and software platform used for building electronics projects and prototypes.
- Raspberry Pi: A series of small, affordable, and programmable single-board computers designed for education and hobbyist projects.
- Open-source drones: Open-source drone projects that provide designs, software, and hardware specifications for building and customizing drones.
Benefits of Open-Source:
- Cost-Effective: Open-source software and hardware are often available for free or at a lower cost compared to proprietary alternatives, making them more accessible and affordable for individuals and organizations.
- Customization: Open-source projects can be customized and adapted to meet specific needs, preferences, and requirements, allowing users to tailor the software or hardware to their unique use cases.
- Community Support: Open-source communities provide support, resources, and collaboration opportunities for developers, contributors, and users, fostering learning, innovation, and knowledge sharing.
- Transparency and Trust: Open-source promotes transparency and accountability by providing visibility into the code, development process, and decision-making, building trust and confidence among users and contributors.
In conclusion, open-source embodies a collaborative and community-driven approach to designing, developing, and distributing software, hardware, and other types of projects. By embracing openness, transparency, collaboration, and freedom, open-source fosters innovation, empowers individuals and organizations, and creates shared value and opportunities for the global community of developers, contributors, and users.
Public Participation
Public Participation Systems (PPS) refer to frameworks, processes, or platforms designed to engage citizens in decision-making processes, policy development, and community initiatives. These systems aim to foster transparency, inclusivity, and collaboration between government entities, organizations, and the public.
Here are some key aspects and characteristics of Public Participation Systems:
- Transparency: PPS aim to provide clear information about government decisions, policies, and projects, allowing citizens to understand and participate in the decision-making process effectively.
- Inclusivity: Public Participation Systems strive to involve a diverse range of stakeholders, ensuring that different voices, perspectives, and interests are represented in the decision-making process.
- Accessibility: PPS often utilize various channels and platforms to engage citizens, including public meetings, online forums, surveys, mobile apps, and social media, making participation accessible to a broader audience.
- Collaboration: These systems encourage collaboration between government agencies, organizations, and the public to co-create solutions, develop policies, and implement initiatives that address community needs and priorities.
- Feedback Mechanisms: PPS incorporate mechanisms for collecting feedback, ideas, and suggestions from citizens, enabling continuous dialogue and iterative improvement of policies and programs.
- Empowerment: By involving citizens in decision-making processes, Public Participation Systems empower individuals and communities to have a voice in issues that affect them, fostering a sense of ownership and civic responsibility.
- Accountability: PPS promote accountability by holding government entities and organizations responsible for engaging with the public, implementing agreed-upon initiatives, and transparently reporting on outcomes and progress.
Examples of Public Participation Systems include:
- Public Hearings and Meetings: Traditional forums where citizens can voice their opinions, ask questions, and provide feedback on proposed policies, projects, or initiatives.
- Online Engagement Platforms: Websites, forums, or social media platforms where citizens can participate in discussions, surveys, or crowdsourcing initiatives related to specific topics or issues.
- Citizen Advisory Boards and Committees: Formal groups of citizens appointed to advise government agencies or organizations on specific issues, projects, or policies.
- Community Workshops and Focus Groups: Interactive sessions designed to gather input, ideas, and insights from citizens on local projects, planning processes, or community development initiatives.
- Public Comment Periods: Designated periods during which citizens can submit written comments, suggestions, or concerns about proposed regulations, plans, or projects.
Overall, Public Participation Systems play a crucial role in promoting democratic governance, fostering civic engagement, and building trust between government entities, organizations, and the public. They help ensure that decisions and policies reflect the needs, values, and priorities of the community, leading to more effective and inclusive outcomes.
Github
Public Participation Systems (PPS) and GitHub may seem like two different entities, but they can be connected in various ways to enhance collaboration, transparency, and public engagement in software development, policy-making, and community initiatives. Here's how Public Participation Systems can leverage GitHub:
- Open Source Projects: GitHub is a popular platform for hosting open-source software projects. Governments, organizations, and community groups can use GitHub to develop open-source solutions, tools, or applications that address public needs or challenges. Citizens can contribute to these projects by submitting code, reporting issues, or suggesting improvements, fostering collaboration between developers and the public.
- Policy Development: GitHub can be used as a platform for drafting, reviewing, and collaboratively editing policy documents, regulations, or guidelines. By hosting policy drafts on GitHub, governments and organizations can invite public feedback, comments, and contributions, making the policy-making process more transparent and inclusive.
- Data Sharing and Transparency: GitHub can be utilized to host datasets, data visualizations, and analysis tools related to government projects, initiatives, or research. By sharing data on GitHub, governments and organizations can promote transparency, encourage public scrutiny, and facilitate data-driven decision-making.
- Community Engagement: GitHub can serve as a platform for hosting community forums, discussions, or Q&A sessions related to specific projects, initiatives, or issues. Governments and organizations can create repositories or organizations on GitHub dedicated to community engagement, where citizens can ask questions, share ideas, and participate in discussions with developers, policymakers, and fellow community members.
- Education and Training: GitHub can be used as a platform for hosting educational resources, tutorials, or training materials related to technology, coding, or policy-making. Governments, organizations, and community groups can create repositories or organizations on GitHub dedicated to educational initiatives, where citizens can access learning resources, participate in workshops, or contribute to educational content.
- Issue Tracking and Management: GitHub's issue tracking features can be used to manage public feedback, suggestions, or concerns related to specific projects, initiatives, or issues. Governments and organizations can create public repositories on GitHub where citizens can report issues, submit suggestions, or track the progress of ongoing projects, fostering transparency and accountability.
- Collaboration and Partnerships: GitHub can facilitate collaboration and partnerships between governments, organizations, developers, and the public. By creating public repositories, organizations, or initiatives on GitHub, governments and organizations can invite external contributors, experts, or stakeholders to collaborate on projects, share resources, or co-create solutions.
In summary, GitHub can be integrated into Public Participation Systems to enhance collaboration, transparency, and public engagement in various domains, including software development, policy-making, community initiatives, and education. By leveraging GitHub's features and capabilities, governments, organizations, and community groups can create more inclusive, transparent, and collaborative environments that empower citizens to contribute to projects, shape policies, and participate in decision-making processes.
Wiki
Public Participation Systems (PPS) and wikis can be combined to create effective platforms for collaboration, knowledge sharing, and public engagement. Wikis are collaborative websites that allow users to create, edit, and organize content collectively, making them well-suited for hosting information, documents, and discussions related to public participation initiatives. Here's how Public Participation Systems can integrate with wikis to enhance transparency, inclusivity, and collaboration:
- Documentation and Resources: Wikis can serve as repositories for public participation guidelines, best practices, training materials, and resources. Governments, organizations, or community groups can create wiki pages dedicated to educating citizens about the public participation process, providing guidance on how to get involved, and sharing relevant resources and tools.
- Policy Development and Review: Wikis can be used to draft, review, and collaboratively edit policy documents, regulations, or guidelines. By hosting policy drafts on wikis, governments and organizations can invite public feedback, comments, and contributions, making the policy-making process more transparent and inclusive.
- Project Collaboration: Wikis can facilitate collaboration between stakeholders, project teams, and the public by providing a platform to document project goals, timelines, milestones, and progress. Governments, organizations, or community groups can create wiki pages for specific projects or initiatives, where participants can contribute ideas, share updates, and collaborate on tasks.
- Community Engagement: Wikis can host community forums, discussions, or Q&A sessions related to specific projects, initiatives, or issues. Governments and organizations can create wiki pages or sections dedicated to community engagement, where citizens can ask questions, share ideas, and participate in discussions with developers, policymakers, and fellow community members.
- Transparency and Accountability: Wikis promote transparency by providing a public platform where documents, discussions, and decisions are documented and accessible to all stakeholders. By using wikis to host meeting minutes, decision logs, and project updates, governments and organizations can foster accountability and ensure that the public can track the progress and outcomes of public participation initiatives.
- Knowledge Sharing and Learning: Wikis can be used to share knowledge, insights, and lessons learned from public participation initiatives. Governments, organizations, or community groups can create wiki pages dedicated to documenting case studies, success stories, and challenges faced during the implementation of public participation projects, providing valuable insights for future initiatives.
- Accessibility and Inclusivity: Wikis are accessible platforms that allow users to contribute and access information from anywhere, at any time. By using wikis for public participation initiatives, governments and organizations can ensure that citizens with diverse backgrounds, abilities, and preferences can easily participate in discussions, contribute to projects, and access resources.
In summary, integrating wikis into Public Participation Systems can enhance collaboration, transparency, and public engagement by providing a platform for sharing information, facilitating discussions, documenting decisions, and fostering collaboration between stakeholders. By leveraging the collaborative nature of wikis, governments, organizations, and community groups can create more inclusive, transparent, and effective public participation initiatives that empower citizens to contribute to projects, shape policies, and participate in decision-making processes.
Information Systems (IS)

The following are types of information systems used to create reports, extract data, and assist in the decision making processes of middle and operational level managers.
Introduction
Approaches to information systems indeed form a multidisciplinary field, combining technical, behavioral, managerial, and organizational perspectives to understand, design, implement, and manage information systems effectively. Among the various approaches, the Technical and Behavioral approaches stand out as key paradigms, each offering unique insights and methodologies for approaching information systems.
1. Technical Approach
Technical Approach emphasizes the technical aspects, components, and functionalities of information systems. It focuses on the design, development, implementation, and management of hardware, software, databases, networks, and other technical elements. Key components of the Technical Approach include:
- System Design and Architecture: Designing the structure, components, and interactions of information systems.
- Software Development: Developing and implementing software applications, platforms, and solutions.
- Hardware Infrastructure: Selecting, configuring, and managing hardware devices, servers, and equipment.
- Data Management: Designing, implementing, and managing databases, data storage, retrieval, and processing.
- Network Management: Establishing, managing, and maintaining networks, connections, and communication infrastructures.
- Security and Compliance: Implementing security measures, protocols, and compliance standards to protect information assets.
2. Behavioral Approach
Behavioral Approach focuses on the human, organizational, social, and cultural aspects of information systems. It emphasizes understanding and managing the behaviors, attitudes, perceptions, motivations, and interactions of individuals, groups, and organizations related to information systems. Key components of the Behavioral Approach include:
- User Behavior and Adoption: Understanding and managing user behaviors, attitudes, perceptions, motivations, and adoption of information systems.
- Organizational Culture and Structure: Aligning information systems with organizational culture, values, structures, and dynamics.
- Change Management: Facilitating organizational change, adoption, and acceptance of information systems.
- Stakeholder Engagement: Engaging, communicating, and collaborating with stakeholders to address their needs and concerns related to information systems.
- Human-Computer Interaction: Designing and managing interfaces, interactions, and experiences between users and information systems.
Approaches to IS
The multidisciplinary nature of approaches to information systems combines technical, behavioral, managerial, and organizational perspectives to address the complexities, challenges, and opportunities in designing, implementing, and managing information systems effectively.
- Technical Expertise: Requires expertise in technology, software development, hardware infrastructure, data management, and network management to design, develop, implement, and manage information systems.
- Behavioral Insights: Requires understanding of human behavior, organizational dynamics, stakeholder engagement, change management, and human-computer interaction to address user needs, adoption challenges, organizational culture, and change management related to information systems.
- Managerial and Organizational Skills: Requires managerial and organizational skills to align information systems with business goals, manage projects, resources, stakeholders, and governance, and ensure strategic alignment, value delivery, and organizational excellence.
In summary, approaches to information systems as a multidisciplinary field integrate technical, behavioral, managerial, and organizational perspectives to understand and manage information systems effectively. By combining the Technical Approach and Behavioral Approach, organizations can design, implement, and manage information systems that are technically robust, aligned with organizational needs and culture, user-friendly, and capable of driving organizational excellence, innovation, and success in the digital age. This integrated, multidisciplinary approach enables organizations to harness the full potential of information systems to achieve strategic goals, enhance user satisfaction, foster innovation, and gain competitive advantages in the dynamic and evolving digital landscape.
Office automation systems (OAS)
Office automation systems (OAS) support communication and productivity in the enterprise by automating workflow and eliminating bottlenecks. OAS may be implemented at any and all levels of management.
DIKW pyramid
The DIKW pyramid, also known variously as the DIKW hierarchy, wisdom hierarchy, knowledge hierarchy, information hierarchy, information pyramid, and the data pyramid, refers loosely to a class of models.
The DIKW pyramid is a conceptual framework that represents the hierarchical structure of data, information, knowledge, and wisdom, illustrating the transformation and progression of raw data into valuable insights and actionable wisdom. The DIKW pyramid is often used to describe the stages of data processing and understanding in various fields, including information science, knowledge management, and data analytics.
DIKW Pyramid Layers:
- Data: Raw, unprocessed facts, observations, and measurements collected from various sources. Characteristics:
- Structure: Represents individual data points, records, or values.
- Context: Lacks context, meaning, and relevance on its own.
- Example: Numbers, dates, names, and observations without interpretation or analysis.
- Information: Processed and organized data that has been transformed into a meaningful context, adding structure, relevance, and interpretation.Characteristics:
- Structure: Organized and structured data with context and relevance.
- Context: Provides context, meaning, and relevance to data through categorization, classification, and organization.
- Example: Data presented in tables, charts, graphs, or reports with added context and interpretation.
- Knowledge: Insights, understanding, and awareness derived from information through analysis, synthesis, and interpretation, representing the application of information and experience. Characteristics:
- Structure: Represents understanding, insights, and awareness derived from analyzing and interpreting information.
- Context: Integrates information with experience, expertise, and understanding to generate insights and knowledge.
- Example: Insights, patterns, trends, and conclusions derived from analyzing and interpreting information and data.
- Wisdom: The ability to make informed decisions, solve problems, and apply knowledge and insights effectively in practical situations, representing the highest level of understanding and application. Characteristics:
- Structure: Represents the ability to apply knowledge, insights, and understanding effectively in decision-making and problem-solving.
- Context: Involves understanding, experience, judgment, intuition, and ethics in applying knowledge and insights.
- Example: Making informed decisions, solving complex problems, and applying knowledge effectively in practical situations based on experience, expertise, and ethical considerations.
DIKW Pyramid Visualization: The DIKW pyramid is often visualized as a hierarchical pyramid or pyramid-shaped diagram, with data at the base, followed by information, knowledge, and wisdom ascending towards the top of the pyramid, illustrating the transformation and progression of data into wisdom.
In summary, the DIKW pyramid provides a conceptual framework for understanding the transformation and progression of data into valuable insights and actionable wisdom, illustrating the stages of data processing, understanding, and application from raw data to informed decision-making and problem-solving. By recognizing and leveraging the stages of the DIKW pyramid, organizations and individuals can effectively manage, analyze, interpret, and apply data and information to generate insights, knowledge, and wisdom, driving innovation, growth, and success in the digital age.
Master Data Management (MDM)
Master Data Management (MDM) is a comprehensive method of defining and managing an organization's critical data to provide a single point of reference. MDM ensures data consistency, accuracy, and reliability across various systems, applications, and departments within an organization. It involves creating and maintaining a master data repository or database, defining data standards, rules, and governance, and implementing processes and technologies to manage and synchronize master data across the enterprise.
Key Components of MDM:
-
Master Data Repository:
- Centralized Database: A centralized repository or database to store, manage, and maintain master data (e.g., customer, product, employee).
- Data Models: Data models and schemas to define the structure, relationships, and attributes of master data.
-
Data Governance:
- Policies and Standards: Establishing data governance policies, standards, rules, and best practices.
- Data Quality: Ensuring data quality, accuracy, consistency, and reliability through data cleansing, validation, and enrichment.
-
Data Integration and Synchronization:
- Integration: Integrating and synchronizing master data across various systems, applications, and platforms.
- Data Exchange: Enabling data exchange and sharing between different departments, systems, and stakeholders.
-
Data Quality and Cleansing:
- Data Quality: Improving data quality through data cleansing, deduplication, validation, and enrichment.
- Monitoring: Monitoring and maintaining data quality over time through continuous monitoring, validation, and governance.
-
Data Security and Privacy:
- Security: Implementing security measures, controls, and protocols to protect master data from unauthorized access, breaches, and threats.
- Privacy: Ensuring data privacy, compliance, and adherence to regulations, standards, and policies (e.g., GDPR, CCPA).
-
Data Lifecycle Management:
- Lifecycle: Managing the lifecycle of master data from creation, modification, and storage to archiving and deletion.
- Auditing and Tracking: Auditing, tracking, and managing data changes, history, versions, and lineage.
Benefits of MDM:
- Data Consistency: Ensuring data consistency, accuracy, and reliability across the organization.
- Improved Decision Making: Providing trusted, reliable, and actionable data for better decision making and analytics.
- Operational Efficiency: Streamlining processes, reducing errors, and improving efficiency through automated and synchronized data management.
- Compliance and Governance: Ensuring compliance with regulations, standards, and policies, and establishing effective data governance.
- Customer Experience: Enhancing customer experience, satisfaction, and loyalty through improved data quality, insights, and personalization.
Challenges of MDM:
- Complexity: Managing and maintaining master data across diverse systems, applications, and departments.
- Data Quality: Ensuring and maintaining data quality, accuracy, and consistency over time.
- Integration: Integrating and synchronizing master data with legacy systems, new applications, and third-party sources.
- Change Management: Managing organizational change, resistance, and adoption of MDM processes, technologies, and governance.
- Cost and Resources: Allocating sufficient resources, budget, and expertise for MDM initiatives, technologies, and governance.
In summary, Master Data Management (MDM) is a comprehensive approach to managing an organization's critical data to ensure consistency, accuracy, and reliability across various systems, applications, and departments. MDM involves creating a centralized master data repository, defining data governance, standards, and rules, implementing data integration and synchronization, ensuring data quality and cleansing, and managing data security, privacy, and lifecycle. While MDM offers numerous benefits, such as improved data consistency, decision making, operational efficiency, compliance, and customer experience, it also presents challenges, including complexity, data quality, integration, change management, and cost. Organizations can leverage MDM solutions, technologies, and best practices to address these challenges and unlock the full potential of their data to drive innovation, growth, and success in the digital age.
Transaction Processing System (TPS)
A Transaction Processing System (TPS) is a type of information system that facilitates the collection, processing, storage, retrieval, and management of transactions, which are individual actions, operations, or events, such as sales, purchases, payments, orders, reservations, and withdrawals, performed by users, customers, employees, and systems within an organization or business. TPS plays a crucial role in supporting and automating routine, repetitive, and operational transactions and activities to ensure accurate, efficient, reliable, and timely processing, execution, and management of transactions to maintain and enhance business operations, productivity, and performance.
The diagram below explains what ACID means in the context of a database transaction.
-
Atomicity
The writes in a transaction are executed all at once and cannot be broken into smaller parts. If there are faults when executing the transaction, the writes in the transaction are rolled back.
So atomicity means “all or nothing”.
-
Consistency
Unlike “consistency” in CAP theorem, which means every read receives the most recent write or an error, here consistency means preserving database invariants. Any data written by a transaction must be valid according to all defined rules and maintain the database in a good state.
-
Isolation
When there are concurrent writes from two different transactions, the two transactions are isolated from each other. The most strict isolation is “serializability”, where each transaction acts like it is the only transaction running in the database. However, this is hard to implement in reality, so we often adopt loser isolation level.
-
Durability
Data is persisted after a transaction is committed even in a system failure. In a distributed system, this means the data is replicated to some other nodes.
Components of Transaction Processing System (TPS):
-
Input Devices:
- Data Entry: Enables users, employees, and systems to input, capture, and record transaction data, information, and details using input devices, such as keyboards, scanners, and touchscreens.
-
Processing Logic:
- Transaction Processing: Performs and executes transaction processing logic, rules, and operations to validate, verify, calculate, update, and manage transaction data, information, and records.
-
Database Management System (DBMS):
- Data Storage and Retrieval: Manages and maintains transaction data, records, and information in databases, enabling storage, retrieval, indexing, and management of data to support transaction processing and operations.
-
Output Devices:
- Data Output and Reporting: Enables users, employees, and systems to retrieve, view, and generate transaction reports, documents, and outputs using output devices, such as monitors, printers, and displays.
Advantages of Transaction Processing System (TPS):
-
Accuracy and Precision:
- Error Reduction: Ensures accurate, consistent, and error-free processing, calculation, and management of transactions to minimize errors, discrepancies, and inaccuracies in transaction data and records.
-
Efficiency and Productivity:
- Automated Processing: Facilitates automated and streamlined transaction processing, execution, and management to enhance efficiency, productivity, and performance of business operations and activities.
-
Reliability and Availability:
- Continuous Operation: Provides reliable, continuous, and uninterrupted transaction processing and availability to support business operations, services, and activities without delays or downtime.
-
Data Integrity and Security:
- Data Protection: Ensures data integrity, security, and protection of transaction data and records through encryption, authentication, access control, and compliance with regulations, standards, and policies.
-
Decision Making and Analysis:
- Data Analysis and Insights: Enables data analysis, reporting, and insights generation from transaction data to support decision making, planning, forecasting, and optimization of business operations, strategies, and performance.
In summary, Transaction Processing System (TPS) is a critical component of information systems that supports and facilitates the collection, processing, storage, retrieval, and management of transactions within organizations and businesses. TPS plays a vital role in ensuring accurate, efficient, reliable, and timely processing and management of transactions to maintain and enhance business operations, productivity, performance, and success. By leveraging the power and capabilities of TPS, organizations and businesses can optimize and streamline their transaction processing and operations to achieve operational excellence, customer satisfaction, competitive advantage, and growth in the dynamic and competitive business environment of today's world.
Management Information System (MIS)
Local databases, can be small, simplified tools for managers and are considered to be a primal or base level version of a MIS.
A Management Information System (MIS) is a specialized type of information system that facilitates the collection, processing, storage, retrieval, analysis, and dissemination of information and data to support and enhance decision-making, management, planning, control, coordination, and operations within organizations and businesses. MIS integrates people, processes, technologies, and data to provide managers, executives, employees, and stakeholders with timely, relevant, accurate, and actionable information, insights, and reports to optimize and improve organizational performance, productivity, efficiency, and competitiveness in the dynamic and competitive business environment.
Components of Management Information System (MIS):
- Hardware:
- Infrastructure: Includes servers, computers, workstations, storage devices, and networking equipment to support MIS operations and functionalities.
- Software:
- Applications and Solutions: Encompasses database management systems (DBMS), reporting tools, analytics software, and customized applications to facilitate data management, analysis, and reporting.
- Data:
- Information and Knowledge: Involves structured, unstructured, and semi-structured data, information, and knowledge generated, collected, and stored in databases, files, and repositories to support MIS functions and operations.
- People:
- Users and Stakeholders: Comprises managers, executives, employees, and stakeholders who use, manage, and benefit from MIS to support decision-making, planning, and operations.
- Processes:
- Operations and Workflows: Involves procedures, workflows, and activities performed by people, systems, and technologies to collect, process, analyze, and disseminate information and data within the organization.
Advantages of Management Information System (MIS):
- Decision Support:
- Informed Decision-Making: Provides managers and executives with timely, relevant, and accurate information, insights, and reports to support informed decision-making, planning, and strategy formulation.
- Operational Efficiency:
- Streamlined Operations: Enhances operational efficiency, productivity, and performance by automating, optimizing, and integrating business processes, workflows, and activities.
- Data Management:
- Centralized Data: Facilitates centralized and secure management, storage, retrieval, and maintenance of organizational data, information, and knowledge to ensure data integrity, consistency, and availability.
- Strategic Planning:
- Planning and Forecasting: Supports strategic planning, forecasting, and alignment of organizational goals, objectives, and resources to optimize and enhance organizational growth, competitiveness, and sustainability.
- Communication and Collaboration:
- Effective Communication: Improves communication, collaboration, and coordination among departments, teams, and stakeholders by providing access to shared information, resources, and tools.
- Competitive Advantage:
- Market Insight: Provides market insights, trends, and analysis to identify opportunities, challenges, and threats to stay competitive and innovative in the marketplace.
Challenges of Management Information System (MIS):
- Integration and Compatibility:
- System Integration: Faces challenges in integrating, aligning, and compatibility with existing systems, technologies, and infrastructures within the organization.
- Data Quality and Governance:
- Data Integrity: Encounters issues with data quality, consistency, accuracy, and governance, requiring proper management, validation, and maintenance of data and information.
- Security and Privacy:
- Data Protection: Concerns with security, privacy, and protection of sensitive and confidential information, requiring robust security measures, policies, and compliance with regulations and standards.
- Cost and Investment:
- Financial Constraints: Involves costs, investments, and financial resources required for development, implementation, maintenance, and support of MIS within the organization.
In summary, Management Information System (MIS) is a critical and integral component of organizations and businesses that leverages technology, people, processes, and data to facilitate decision-making, management, planning, control, and operations. MIS empowers managers, executives, employees, and stakeholders with timely, relevant, accurate, and actionable information and insights to optimize and enhance organizational performance, productivity, efficiency, and competitiveness in the dynamic and competitive business landscape. By embracing and adopting MIS, organizations can achieve operational excellence, strategic alignment, competitive advantage, growth, and success by leveraging the power and capabilities of information, technology, and innovation in the interconnected and digital world of today's business environment.
Decision Support Systems (DSS)
Decision support systems (DSSs) are computer program applications used by middle and higher management to compile information from a wide range of sources to support problem solving and decision making. A DSS is used mostly for semi-structured and unstructured decision problems.
Ideally, an intelligent decision support system(IDSS) should behave like a human consultant: supporting decision makers by gathering and analysing evidence, identifying and diagnosing problems, proposing possible courses of action and evaluating such proposed actions. The aim of the AI techniques embedded in an intelligent decision support system is to enable these tasks to be performed by a computer, while emulating human capabilities as closely as possible.
Executive Information System (EIS)
Executive information system (EIS) is a reporting tool that provides quick access to summarized reports coming from all company levels and departments such as accounting, human resources and operations.
An Executive Information System (EIS) is a specialized type of Management Information System (MIS) designed specifically to support the information and decision-making needs of senior executives, managers, and decision-makers within organizations and businesses. EIS provides a user-friendly, interactive, and intuitive interface to enable executives and managers to access, analyze, and visualize key performance indicators (KPIs), metrics, reports, and insights related to organizational performance, strategies, operations, finances, markets, customers, competitors, and trends. EIS empowers executives and managers with timely, relevant, accurate, and actionable information to support strategic planning, decision-making, forecasting, problem-solving, and leadership in the dynamic and competitive business environment.
Components of Executive Information System (EIS):
-
User Interface:
- Dashboard and Visualization: Provides customizable dashboards, graphs, charts, and visualizations to present and display key performance indicators (KPIs), metrics, and insights in a clear, concise, and interactive manner.
-
Data Integration and Analytics:
- Data Sources and Integration: Integrates and aggregates data from various sources, systems, and databases to provide a unified and consolidated view of organizational data, information, and insights.
- Analytical Tools and Capabilities: Includes advanced analytical tools, algorithms, and capabilities to analyze, interpret, and visualize data to identify patterns, trends, correlations, and insights.
-
Reporting and Presentation:
- Reports and Summaries: Generates and presents comprehensive and summarized reports, summaries, and presentations to provide executives with insights and overviews of organizational performance, operations, and strategies.
-
Alerts and Notifications:
- Real-Time Alerts: Sends real-time alerts, notifications, and updates to executives and managers regarding critical events, issues, and opportunities requiring attention, action, or intervention.
-
Collaboration and Communication:
- Communication and Collaboration: Facilitates communication, collaboration, and sharing of information, insights, and reports among executives, managers, teams, and stakeholders to enhance teamwork, coordination, and alignment.
Advantages of Executive Information System (EIS):
-
Strategic Decision-Making:
- Informed Decision-Making: Empowers executives and managers with timely, relevant, and accurate information and insights to support strategic planning, decision-making, and leadership.
-
Performance Monitoring:
- Performance Evaluation: Enables monitoring, evaluation, and analysis of organizational performance, KPIs, metrics, and goals to assess progress, achievements, and areas for improvement.
-
Operational Efficiency:
- Efficient Operations: Enhances operational efficiency, productivity, and performance by providing executives with insights, reports, and tools to optimize and streamline operations, processes, and workflows.
-
Competitive Advantage:
- Market Insight and Analysis: Provides market insights, trends, and analysis to identify opportunities, threats, and competitive advantages to stay ahead in the marketplace.
-
Alignment and Coordination:
- Strategic Alignment: Facilitates alignment, coordination, and synchronization of organizational goals, strategies, and resources among executives, managers, and teams to achieve shared objectives and success.
Challenges of Executive Information System (EIS):
-
Data Quality and Integrity:
- Data Accuracy: Faces challenges with data quality, accuracy, consistency, and integrity, requiring proper management, validation, and maintenance of data sources and integration.
-
Integration and Compatibility:
- System Integration: Encounters issues with integration, alignment, and compatibility with existing systems, technologies, and data sources within the organization.
-
Security and Privacy:
- Data Protection: Concerns with security, privacy, and protection of sensitive and confidential information, requiring robust security measures, policies, and compliance with regulations and standards.
-
Cost and Investment:
- Financial Constraints: Involves costs, investments, and financial resources required for development, implementation, maintenance, and support of EIS within the organization.
In summary, Executive Information System (EIS) is a critical and valuable tool for senior executives, managers, and decision-makers to access, analyze, and visualize key information, insights, and reports related to organizational performance, strategies, operations, and market dynamics. EIS empowers executives with the information, tools, and capabilities to support strategic planning, decision-making, forecasting, problem-solving, and leadership to drive organizational success and competitiveness in the dynamic and competitive business environment. By embracing and adopting EIS, organizations can achieve strategic alignment, operational excellence, competitive advantage, growth, and success by leveraging the power and capabilities of information, technology, and innovation in the interconnected and digital world of today's business landscape.
Business Intelligence (BI)
Business Intelligence (BI) and Analytics Tools: BI and analytics tools provide businesses with insights into their operations, performance, and market trends. These tools analyze data from various sources, such as ERP, CRM, and SCM systems, to generate reports, dashboards, and visualizations that inform decision-making and strategic planning.
Analytics
Data Analytics, Business Intelligence, and Data Science are closely related fields that involve working with data to derive insights, make informed decisions, and drive business growth. While they share similarities, each field has its own focus, methodologies, and applications. Let's explore the differences and key characteristics of Data Analytics, Business Intelligence, and Data Science:
Data Analytics
Focus: Data Analytics focuses on analyzing datasets to identify trends, patterns, and insights that can be used to make data-driven decisions.
Methodology:
- Descriptive Analytics: Examines historical data to understand what has happened.
- Diagnostic Analytics: Investigates data to determine why something happened.
- Predictive Analytics: Uses statistical models and machine learning algorithms to forecast future trends and outcomes.
- Prescriptive Analytics: Recommends actions and strategies based on analysis and insights.
Applications:
- Marketing analytics
- Customer segmentation
- Financial analysis
- Operational efficiency
- Performance tracking
Tools and Technologies: Excel, SQL, Tableau, Power BI, Python, R
Business Intelligence (BI)
Focus: Business Intelligence focuses on collecting, analyzing, and presenting business data to support decision-making and strategic planning.
Methodology:
- Data Collection: Gathers data from various sources, including databases, CRM systems, and spreadsheets.
- Data Transformation: Cleans, transforms, and prepares data for analysis and reporting.
- Data Analysis: Analyzes data to generate insights, trends, and visualizations.
- Reporting and Dashboards: Presents data and insights through reports, dashboards, and interactive visualizations.
Applications:
- Performance reporting
- Sales analytics
- Financial reporting
- Market research
- Competitive analysis
Tools and Technologies: Tableau, Power BI, QlikView, SAP BusinessObjects, MicroStrategy
Data Science
Focus: Data Science combines statistics, programming, and domain knowledge to extract insights from complex and large datasets, build predictive models, and solve business problems.
Methodology:
- Data Collection: Gathers and cleans data from various sources.
- Data Exploration: Explores and visualizes data to understand patterns, correlations, and relationships.
- Data Modeling: Builds statistical models, machine learning algorithms, and predictive models to analyze data and make predictions.
- Deployment: Implements and integrates models into production systems or applications to drive insights and decision-making.
Applications:
- Predictive analytics
- Machine learning
- Natural language processing
- Image recognition
- Fraud detection
Tools and Technologies: Python, R, TensorFlow, Scikit-learn, Spark, SQL
Comparison Summary
- Data Analytics: Focuses on analyzing datasets to identify trends, patterns, and insights for decision-making. It includes descriptive, diagnostic, predictive, and prescriptive analytics and is often used for marketing, customer segmentation, and financial analysis.
- Business Intelligence (BI): Focuses on collecting, analyzing, and presenting business data to support decision-making and strategic planning. It involves data collection, transformation, analysis, and reporting and is used for performance reporting, sales analytics, and financial reporting.
- Data Science: Combines statistics, programming, and domain knowledge to extract insights from complex datasets, build predictive models, and solve business problems. It includes data collection, exploration, modeling, and deployment and is used for predictive analytics, machine learning, and natural language processing.
In summary, while Data Analytics, Business Intelligence, and Data Science share similarities in working with data to derive insights and make informed decisions, they differ in focus, methodologies, and applications. Data Analytics focuses on analyzing datasets for insights, Business Intelligence focuses on collecting and presenting business data for decision-making, and Data Science combines statistics, programming, and domain knowledge to solve complex problems and build predictive models. Each field plays a crucial role in leveraging data to drive business growth, innovation, and competitive advantage in today's data-driven world.
Components and Technologies
Ref: Approach to Building and Implementing Business Intelligence Systems
https://kissflow.com/workflow/bpm/difference-between-bpm-and-erp/
Data Mining:
Definition: Data Mining is the process of discovering patterns, trends, insights, correlations, and knowledge from large volumes of structured and unstructured data using various techniques, algorithms, and methods. Data Mining enables organizations to analyze and extract valuable information and insights from data to support decision-making, forecasting, prediction, and strategic planning.
Key Components:
- Data Collection and Integration: Collects and integrates data from various sources and systems.
- Data Cleaning and Preprocessing: Cleans, transforms, and preprocesses data to prepare it for analysis.
- Data Mining Algorithms: Applies algorithms and techniques to discover patterns, trends, and insights in data.
- Pattern Recognition and Prediction: Identifies patterns, trends, correlations, and predictions in data.
- Insights and Visualization: Presents insights, findings, and visualizations to convey information and insights.
OLAP (Online Analytical Processing):
Definition: OLAP (Online Analytical Processing) is a technology that enables users to analyze multidimensional data interactively from multiple perspectives and dimensions to facilitate complex analysis, reporting, and decision-making. OLAP provides tools and features to perform ad-hoc queries, drill-down, roll-up, slice, dice, pivot, and rotate data to explore and analyze data dynamically and interactively.
Key Components:
- Multidimensional Data Modeling: Models data in dimensions, hierarchies, and cubes for analysis.
- Ad-Hoc Queries and Analysis: Enables users to perform ad-hoc queries and analysis interactively.
- Drill-Down and Roll-Up: Allows users to drill-down to detailed data and roll-up to summarized data.
- Slice and Dice: Enables users to slice and dice data by dimensions and criteria.
- Visualization and Reporting: Provides visualizations, dashboards, and reports for data analysis.
Data Warehouse:
Definition: A Data Warehouse is a centralized repository or database that integrates, consolidates, cleans, transforms, and stores data from multiple sources and systems to support reporting, analysis, business intelligence, and decision-making within organizations. A Data Warehouse provides a structured and organized environment to store historical and current data for easy access, retrieval, and analysis.
Key Components:
- Data Integration and ETL (Extract, Transform, Load): Integrates, cleans, transforms, and loads data from various sources into the Data Warehouse.
- Data Modeling and Schema: Models data and defines schemas, structures, and relationships in the Data Warehouse.
- Data Storage and Management: Stores, manages, and organizes data in a structured and organized manner.
- Data Access and Retrieval: Enables users to access, retrieve, and query data from the Data Warehouse.
- Data Security and Compliance: Ensures data security, access control, encryption, and compliance with regulations and standards.
KPIs (Key Performance Indicators):
Definition: Key Performance Indicators (KPIs) are measurable values and metrics that organizations use to evaluate and assess performance, efficiency, effectiveness, and success in achieving strategic objectives, goals, and targets. KPIs provide insights, benchmarks, and indicators to monitor, measure, and manage performance across various departments, functions, and operations.
Key Components:
- Performance Metrics and Indicators: Defines and measures performance metrics, values, and indicators.
- Targets and Goals: Sets and defines targets, goals, and benchmarks for performance.
- Monitoring and Tracking: Monitors and tracks KPIs and performance metrics in real-time or over time.
- Analysis and Reporting: Analyzes, visualizes, and reports on KPIs and performance data.
- Decision-making and Strategy: Supports decision-making, planning, and strategy development based on KPIs and insights.
Analytics in Business Intelligence (BI):
Definition: Business Intelligence (BI) is a technology-driven process and approach that enables organizations to analyze, visualize, and leverage data, insights, and intelligence to make informed decisions, drive business performance, and achieve strategic objectives. BI encompasses various tools, technologies, platforms, and practices, including data mining, OLAP, data warehousing, KPIs, analytics, dashboards, and reporting.
Key Components:
- Data Integration and Management: Integrates, cleans, manages, and organizes data from various sources and systems.
- Data Analysis and Exploration: Analyzes, explores, and visualizes data to discover insights, patterns, and trends.
- Reporting and Dashboards: Generates reports, dashboards, and visualizations to present insights, findings, and analytics.
- Decision Support and Strategy: Provides decision support tools, features, and insights to support decision-making, planning, and strategy development.
- Collaboration and Sharing: Facilitates collaboration, sharing, and communication of insights, reports, and analytics among users, departments, and stakeholders.
In summary, Data Mining, OLAP, Data Warehouse, KPIs, and Analytics play crucial roles in Business Intelligence (BI) by providing tools, techniques, platforms, and practices to analyze, explore, visualize, and leverage data, insights, and intelligence to make informed decisions, drive business performance, achieve strategic objectives, and succeed in the dynamic and evolving business landscape.
By integrating and leveraging Data Mining, OLAP, Data Warehouse, KPIs, and Analytics in BI initiatives and strategies, organizations can optimize, manage, and enhance performance, efficiency, productivity, decision-making, planning, and success across various departments, functions, and operations in the dynamic and competitive business environment.
Architectural patterns in computer science
Architectural patterns in computer science refer to reusable solutions to common problems in software architecture. They provide a template or blueprint that can be used to guide the design and development of software systems. Here are some common architectural patterns:
1. Monolithic Architecture: A monolithic architecture is a single-tiered software application in which different components are combined into a single program on a single platform. All functionalities are managed and served from a single codebase.
Benefits:
- Simplicity: Easy to develop and deploy initially.
- Performance: Direct communication within the application without the overhead of network calls.
- Testing: Easier to perform end-to-end testing in a single environment.
Drawbacks:
- Scalability: Hard to scale parts of the application independently.
- Maintenance: Difficult to maintain and update as the application grows.
- Deployment: Any changes require redeploying the entire application.
2. Layered (n-tier) Architecture: A layered architecture organizes the system into layers, each with specific responsibilities. Common layers include presentation, business logic, and data access layers.
Benefits:
- Separation of Concerns: Each layer handles a specific part of the application, making it easier to manage.
- Modularity: Layers can be developed and updated independently.
- Reusability: Common functionalities can be reused across different parts of the application.
Drawbacks:
- Performance: Additional layers can introduce latency.
- Complexity: Managing dependencies between layers can become complex.
3. Service-Oriented Architecture (SOA): SOA is an architectural pattern where services are provided to other components by application components, through a communication protocol over a network. Uses an Enterprise Service Bus (ESB) to manage communication between services.
Benefits:
- Interoperability: Different services can be integrated regardless of the platforms they run on.
- Reusability: Services can be reused across different applications.
- Scalability: Individual services can be scaled independently.
Drawbacks:
- Complexity: More complex to design and manage.
- Performance Overhead: Network communication between services can introduce latency.
4. Microservices Architecture: Microservices architecture structures an application as a collection of loosely coupled services, each responsible for a specific business capability. Each service can be developed, deployed, and scaled independently.
Benefits:
- Scalability: Services can be scaled independently.
- Resilience: Failure of one service does not affect others.
- Flexibility: Easier to adopt new technologies for different services.
Drawbacks:
- Complexity: More complex to manage due to the number of services.
- Network Overhead: Increased communication over the network can introduce latency.
- Data Consistency: Managing data consistency across services can be challenging.
5. Event-Driven Architecture: In an event-driven architecture, services communicate through events. An event is a significant change in state, often signaled by the creation of a message. Typically uses a message broker (e.g., Kafka) to handle event distribution.
Benefits:
- Decoupling: Services are loosely coupled and communicate asynchronously.
- Scalability: Easier to scale as services operate independently.
- Real-Time Processing: Suitable for applications that require real-time data processing.
Drawbacks:
- Complexity: More complex to implement and manage.
- Event Management: Ensuring reliable event delivery and handling can be challenging.
6. Client-Server Architecture: The client-server architecture divides the system into two parts: clients and servers. Clients request services and servers provide them. Commonly used in web applications where the client is the web browser and the server is the backend server.
Benefits:
- Modularity: Clients and servers can be developed independently.
- Centralized Control: Easier to manage and update the server.
Drawbacks:
- Scalability: Server can become a bottleneck as the number of clients increases.
- Maintenance: Requires managing both client and server components.
7. Peer-to-Peer (P2P) Architecture: In a peer-to-peer architecture, each node (peer) in the network can act as both a client and a server. Peers share resources directly with each other without a central server.
Benefits:
- Scalability: High scalability as each peer contributes resources.
- Fault Tolerance: No single point of failure.
Drawbacks:
- Security: Harder to secure as control is decentralized.
- Complexity: More complex to manage and coordinate peers.
8. Pipe-and-Filter Architecture: In a pipe-and-filter architecture, the system is divided into components (filters) that process data in stages. The data flows through pipes between filters. Often used in data processing systems.
Benefits:
- Modularity: Filters can be reused and combined in different ways.
- Scalability: Individual filters can be scaled independently.
Drawbacks:
- Latency: Each stage adds processing time, which can introduce latency.
- Error Handling: Managing errors across multiple stages can be challenging.
Conclusion
Each architectural pattern has its strengths and weaknesses and is suitable for different types of applications and business needs. Selecting the right architecture is crucial for the success of a software project and should be based on factors such as scalability, complexity, maintenance, performance, and specific business requirements. Understanding these patterns helps in making informed decisions to design robust and efficient systems. sdfasfasdfasdsdfdfArchitectural patterns provide a structured approach to designing and implementing Business Intelligence (BI) and Enterprise Resource Planning (ERP) systems, ensuring they are scalable, maintainable, and efficient. Here’s how different architectural patterns can help BI and ERP systems:
1. Monolithic Architecture
Business Intelligence (BI)
- Integrated Data Management: Monolithic architecture simplifies the integration of various BI components, ensuring seamless data flow and consistency.
- Performance Optimization: Direct calls within a single application improve performance for data processing and analytics tasks.
- Simplified Development: Easier to develop and deploy initially, which is beneficial for small to medium-sized BI solutions.
ERP
- Unified Platform: Combines all ERP modules (finance, HR, supply chain) into a single application, ensuring seamless communication and data consistency.
- Ease of Deployment: Simplifies deployment and reduces infrastructure complexity.
- Cost-Effectiveness: Lower infrastructure costs compared to distributed systems, making it suitable for smaller organizations.
2. Layered (n-tier) Architecture
Business Intelligence (BI)
- Separation of Concerns: Divides BI system into layers (presentation, business logic, data access), enhancing maintainability and scalability.
- Reusability: Common services and components can be reused across different layers, improving efficiency.
- Improved Security: Layers can implement security measures independently, ensuring robust data protection.
ERP
- Modular Design: Allows different ERP modules to be developed and maintained independently, improving flexibility and manageability.
- Enhanced Security: Security can be enforced at different layers, protecting sensitive business data.
- Scalability: Individual layers can be scaled based on demand, improving overall system performance.
3. Service-Oriented Architecture (SOA)
Business Intelligence (BI)
- Modular Services: BI components (data collection, processing, analytics) can be developed as independent services, facilitating easier updates and maintenance.
- Interoperability: SOA enables integration of BI systems with diverse data sources and external applications.
- Scalability: Independent services can be scaled as needed, enhancing performance and responsiveness.
ERP
- Flexibility and Adaptability: ERP functions are encapsulated into services that can be updated or replaced independently, ensuring the system adapts to changing business needs.
- Reusability and Integration: Services can be reused across different business units and integrated with other enterprise systems.
- Improved Maintenance: Individual services can be maintained and upgraded without affecting the entire system.
4. Microservices Architecture
Business Intelligence (BI)
- High Scalability: Each microservice can be scaled independently, allowing the BI system to handle varying workloads efficiently.
- Fault Tolerance: Failure of one microservice doesn’t impact the entire BI system, enhancing reliability.
- Real-Time Processing: Microservices can process and analyze data in real-time, providing timely insights.
ERP
- Decoupling of Modules: ERP functions are split into microservices, allowing for independent development, deployment, and scaling.
- Agility: Faster development cycles and the ability to adopt new technologies for different services.
- Event-Driven Architecture: Using tools like Kafka, ERP systems can implement event-driven designs, improving real-time processing and integration capabilities.
5. Event-Driven Architecture
Business Intelligence (BI)
- Asynchronous Processing: Enables real-time data processing and analytics through event streams.
- Scalability: Event-driven systems can handle high data volumes and scale horizontally.
- Flexibility: BI components can be added or modified without disrupting the entire system.
ERP
- Real-Time Data Flow: Event-driven architecture ensures real-time updates and communication between ERP modules.
- Decoupling: Loose coupling of services improves system flexibility and resilience.
- Scalability and Performance: Handles large volumes of transactions efficiently, improving overall system performance.
Conclusion: Architectural patterns offer tailored solutions for designing robust, scalable, and maintainable BI and ERP systems. By choosing the appropriate pattern, organizations can ensure their BI and ERP systems are well-suited to meet current and future business demands. Here’s a summary of how each pattern helps:
- Monolithic Architecture: Simplifies initial development and deployment; best for smaller systems.
- Layered Architecture: Provides clear separation of concerns, enhancing maintainability and scalability.
- Service-Oriented Architecture (SOA): Offers flexibility, reusability, and interoperability.
- Microservices Architecture: Enables high scalability, resilience, and agility.
- Event-Driven Architecture: Facilitates real-time processing and decoupling of components.
The choice of architectural pattern should be based on the specific needs, scale, and complexity of the BI and ERP systems, ensuring they support the organization’s strategic goals effectively.
Business Process Management System (BPMS)
Business Process Management System (BPMS) is an integrated software platform designed to model, automate, manage, and optimize business processes, workflows, tasks, and operations within organizations. BPMS provides tools and features to design, execute, monitor, analyze, and improve business processes to enhance efficiency, agility, productivity, and performance.
Key Components:
- Process Modeling and Design: Enables modeling, design, and visualization of business processes and workflows.
- Process Automation and Execution: Automates and executes business processes, tasks, and activities.
- Monitoring and Analytics: Monitors, analyzes, and reports on process performance, KPIs, and metrics.
- Integration and Connectivity: Integrates with other systems, applications, and databases to streamline operations.
- Collaboration and Communication: Facilitates collaboration, communication, and teamwork among users.
Enterprise Resource Planning (ERP):
Definition: Enterprise Resource Planning (ERP) is an integrated software solution designed to manage and streamline core business processes, operations, functions, and activities across various departments, functions, and units within organizations. ERP provides a centralized platform to integrate and automate business processes, workflows, tasks, and data to enhance efficiency, productivity, collaboration, visibility, control, and decision-making.
Key Components:
- Finance and Accounting: Manages financial accounting, budgeting, forecasting, cash flow, assets, liabilities, expenses, revenue, and financial reporting.
- Human Resources (HR): Handles recruitment, onboarding, training, development, performance management, payroll, benefits, and employee relations.
- Supply Chain Management (SCM): Manages inventory, orders, procurement, logistics, warehousing, distribution, and supplier relationships.
- Customer Relationship Management (CRM): Manages sales, marketing, customer engagement, leads, opportunities, campaigns, and customer interactions.
Comparison:
|
Criteria
|
Business Process Management System (BPMS)
|
Enterprise Resource Planning (ERP)
|
|
Focus
|
Business Process Modeling and Automation
|
Core Business Process and Operations
|
|
Primary Objective
|
Optimize and Automate Business Processes
|
Streamline and Integrate Business Processes
|
|
Key Components
|
Process Modeling, Automation, Monitoring
|
Finance, HR, SCM, CRM
|
|
Integration
|
Integrates with Various Systems and Processes
|
Integrated Platform for Departments and Functions
|
|
Customization
|
Customizable Process Design and Automation
|
Customizable Modules and Functions
|
|
User Base
|
Process Designers, Managers, Analysts
|
Employees, Departments, Managers, Executives
|
|
Analytics and Reporting
|
Process Performance, KPIs, Metrics
|
Financial, Operational, Customer Analytics
|
|
Collaboration
|
Collaboration and Communication Tools
|
Collaboration Features for Departments and Teams
|
Conclusion:
-
Business Process Management System (BPMS) is focused on modeling, automating, managing, and optimizing business processes and workflows within organizations. BPMS provides tools and features to design, execute, monitor, analyze, and improve business processes to enhance efficiency, agility, productivity, and performance.
-
Enterprise Resource Planning (ERP) focuses on integrating and automating core business processes, operations, functions, and activities across various departments, functions, and units within organizations. ERP provides a centralized platform to manage and streamline finance, HR, SCM, CRM, and other core business processes to enhance efficiency, productivity, collaboration, visibility, control, and decision-making.
While both BPMS and ERP aim to streamline and optimize business processes, they have distinct focuses and objectives:
-
BPMS is specialized for business process modeling, automation, and management to optimize and improve specific processes and workflows within organizations.
-
ERP is more comprehensive and focuses on integrating and automating core business processes, functions, and activities across various departments and units to provide an integrated platform for managing finance, HR, SCM, CRM, and other core business processes effectively and efficiently.
Organizations may adopt BPMS, ERP, or both depending on their needs, objectives, and requirements to enhance business process management, streamline operations, improve efficiency, and achieve their goals in the dynamic and evolving business landscape.
Enterprise Resource Planning (ERP)
Enterprise Resource Planning (ERP) Systems: ERP systems integrate core business processes and functions, such as finance, human resources, procurement, inventory management, and customer relationship management (CRM), into a unified system. This integrated approach allows for real-time data sharing, improved collaboration, and streamlined operations across the organization.
Enterprise resource planning (ERP) software facilitates the flow of information between all business functions inside the boundaries of the organization and manage the connections to outside stakeholders.[9]
Enterprise Resource Planning (ERP) is an integrated software solution and platform designed to facilitate and manage the core business processes, operations, functions, and activities of organizations, businesses, and enterprises across various departments, functions, and units. ERP integrates and centralizes data, information, processes, and resources from different departments, functions, and systems into a unified, standardized, and cohesive system to enhance efficiency, productivity, collaboration, visibility, control, and decision-making in organizations.
Components of Enterprise Resource Planning (ERP):
- Finance and Accounting:
- Financial Management: Manages financial accounting, budgeting, forecasting, cash flow, assets, liabilities, expenses, revenue, and financial reporting.
- Cost Management: Controls and monitors costs, expenses, and financial performance to optimize profitability, liquidity, and financial health.
- Human Resources (HR):
- Human Resource Management (HRM) Systems: HRM systems manage employee information, payroll, benefits administration, recruitment, performance evaluations, and training and development. These systems help businesses streamline HR processes, improve workforce management, and enhance employee engagement and productivity.
- HR Management: Handles recruitment, onboarding, training, development, performance management, payroll, benefits, and employee relations.
- Talent Management: Manages talent acquisition, retention, succession planning, and career development to foster a skilled and engaged workforce.
- Benefits of Business Management Systems:Improved Efficiency: Streamlined processes and automated workflows reduce manual tasks and improve operational efficiency.
Enhanced Collaboration: Integrated systems enable better communication and collaboration between departments and teams.
Data-Driven Decision Making: Access to real-time data and insights facilitates informed decision-making and strategic planning.
Cost Reduction: Optimized operations, reduced manual errors, and better resource allocation lead to cost savings.
Scalability: Flexible and modular systems can adapt to the changing needs and growth of the business.In summary, Business Management Systems play a crucial role in helping organizations streamline operations, improve efficiency, and make informed decisions by integrating and optimizing various business processes and functions. Whether it's an ERP system, CRM platform, or BI tool, businesses can leverage these systems to achieve their goals, drive growth, and remain competitive in today's dynamic business environment.
- Supply Chain Management (SCM):
- SCM systems manage and optimize supply chain processes, including procurement, production, inventory management, logistics, and distribution. These systems help businesses enhance supply chain visibility, reduce costs, improve supplier relationships, and ensure timely delivery of products and services.
- Inventory Management: Manages inventory, stock, orders, procurement, logistics, warehousing, and distribution to optimize supply chain operations.
- Procurement and Purchasing: Streamlines procurement, purchasing, sourcing, supplier management, and contract management to ensure cost-effective and efficient sourcing.
- Customer Relationship Management (CRM):
- Customer Relationship Management (CRM) Systems: CRM systems focus on managing relationships and interactions with customers and prospects. These systems help businesses track customer interactions, manage sales pipelines, automate marketing campaigns, and analyze customer data to improve engagement and satisfaction. Customer Relationship Management (CRM) managing and analyzing customer interactions and data to improve customer relationships and enhance satisfaction.
- Sales and Marketing: Manages sales, marketing, customer engagement, leads, opportunities, campaigns, and customer interactions to enhance customer acquisition, retention, and satisfaction.
- Service and Support: Provides service, support, maintenance, and after-sales services to meet customer needs, expectations, and requirements.
- Manufacturing and Production:
- Production Planning: Plans, schedules, and controls production, manufacturing, operations, resources, and capacity to optimize production efficiency and effectiveness.
- Quality Management: Ensures quality control, assurance, compliance, and improvement in manufacturing, production, and operations to meet quality standards and requirements.
Advantages of Enterprise Resource Planning (ERP):
- Integrated and Centralized System: Provides a unified, centralized, and integrated platform to manage and streamline core business processes, operations, functions, and activities across the organization.
- Enhanced Efficiency and Productivity: Automates and optimizes business processes, tasks, workflows, and operations to enhance efficiency, productivity, and performance.
- Improved Visibility and Control: Offers real-time visibility, insights, analytics, and reporting to monitor, analyze, and control business operations, performance, and outcomes.
- Streamlined Collaboration and Communication: Facilitates collaboration, communication, and teamwork among departments, teams, and stakeholders to foster innovation, creativity, and synergy.
- Scalability and Flexibility: Provides a scalable, flexible, and adaptable platform to support growth, expansion, and changes in business needs, requirements, and environments.
Challenges of Enterprise Resource Planning (ERP):
- Implementation and Integration: Encounters challenges with ERP implementation, integration, customization, configuration, and alignment with organizational needs and systems.
- User Adoption and Training: Faces issues with user adoption, resistance, training, and change management requiring education, support, and engagement to encourage and sustain usage.
- Cost and Investment: Involves high costs, investments, expenses, and budgets for ERP licensing, implementation, customization, maintenance, and support requiring financial planning and management.
- Customization and Flexibility: Limits customization, flexibility, and adaptability of ERP systems to meet unique, specific, and evolving business needs, processes, and requirements.
In summary, Enterprise Resource Planning (ERP) is a comprehensive and integrated software solution designed to streamline, optimize, and manage core business processes, operations, functions, and activities across organizations, businesses, and enterprises. ERP enables organizations to achieve enhanced efficiency, productivity, collaboration, visibility, control, and decision-making by integrating and centralizing data, information, processes, and resources into a unified, standardized, and cohesive system. By embracing and adopting ERP, organizations can optimize business performance, competitiveness, growth, innovation, and success in the dynamic and evolving landscape of today's digital, global, and interconnected business world.
Enterprise Resource Planning (ERP II)
Enterprise Resource Planning (ERP) and ERP II are two generations of software systems designed to manage and integrate core business processes within an organization. Here are the key differences between ERP and ERP II:
-
ERP (Enterprise Resource Planning):
- ERP systems originated in the 1990s and were primarily focused on automating and integrating internal business processes such as finance, human resources, manufacturing, supply chain management, and customer relationship management.
- ERP systems typically consist of modules or applications that address specific functional areas of the organization, such as finance/accounting, HR/payroll, inventory management, and sales.
- ERP systems are centralized and provide a single source of truth for data, allowing different departments within the organization to access and share information in real-time.
- ERP systems streamline business operations, improve efficiency, and provide better visibility into key business metrics and performance indicators.
-
ERP II (Enterprise Resource Planning II):
- ERP II emerged in the early 2000s as an evolution of traditional ERP systems, with a broader scope and enhanced capabilities to support collaboration and integration with external partners, suppliers, and customers.
- ERP II systems extend beyond the internal operations of the organization and incorporate external stakeholders into the business processes, creating a more interconnected and collaborative business ecosystem.
- ERP II systems include features such as supply chain management, customer relationship management (CRM), e-commerce, and business intelligence/analytics to facilitate collaboration, data exchange, and decision-making across the entire value chain.
- ERP II systems often leverage emerging technologies such as cloud computing, mobile applications, social media integration, and data analytics to enable real-time information sharing, collaboration, and business insights.
- ERP II systems enable organizations to become more agile, responsive, and customer-centric by integrating internal processes with external partners and leveraging data-driven insights to drive strategic decision-making.
In summary, while traditional ERP systems focus on internal business processes and operational efficiency, ERP II systems extend beyond the organization's boundaries to integrate external stakeholders and support collaboration across the entire value chain. ERP II systems leverage advanced technologies and data analytics to enable real-time information sharing, decision-making, and customer engagement, driving business innovation and competitive advantage.
Intelligent Business Process Management (iBPMS)
Intelligent Business Process Management (iBPMS) is an advanced and integrated software platform that combines traditional Business Process Management (BPM) capabilities with Artificial Intelligence (AI), Machine Learning (ML), Predictive Analytics, and other intelligent technologies to automate, optimize, manage, and enhance business processes, workflows, tasks, and operations within organizations.
Key Components:
- Business Process Modeling and Design: Enables modeling, designing, and visualizing business processes, workflows, and tasks.
- Process Automation and Orchestration: Automates and orchestrates business processes, tasks, and activities across systems, departments, and functions.
- Intelligent Decision-making and Recommendations: Applies AI, ML, and analytics to make intelligent decisions, predictions, and recommendations.
- Real-time Monitoring and Analytics: Monitors, analyzes, and reports on process performance, KPIs, and metrics in real-time.
- Collaboration and Integration: Facilitates collaboration, communication, and integration among users, systems, and stakeholders.
- Adaptive and Dynamic Processes: Adapts and adjusts processes dynamically based on changes, events, and insights.
- User Experience and Engagement: Enhances user experience, engagement, and satisfaction with intuitive interfaces and features.
- Security and Compliance: Ensures process security, data protection, access control, and compliance with regulations and standards.
Key Benefits:
- Automation and Efficiency: Automates repetitive, manual, and routine tasks to improve efficiency, productivity, and operational performance.
- Optimization and Agility: Optimizes and streamlines business processes, workflows, and operations to enhance agility, flexibility, and responsiveness.
- Insights and Intelligence: Provides insights, intelligence, and analytics to support decision-making, forecasting, and planning.
- Collaboration and Integration: Facilitates collaboration, communication, and integration among users, systems, departments, and stakeholders.
- Innovation and Transformation: Promotes innovation, transformation, and digitalization of processes, operations, and business models.
- Customer Experience and Satisfaction: Enhances customer experience, satisfaction, and loyalty with improved processes, services, and interactions.
Integration in Organizations:
Intelligent Business Process Management (iBPMS) is increasingly adopted and integrated into organizations across various industries and sectors to automate, optimize, manage, and enhance business processes, workflows, tasks, and operations effectively and efficiently.
- Industry Applications: iBPMS is applied in industries such as finance, healthcare, manufacturing, retail, logistics, telecommunications, and more to improve processes, operations, and services.
- Digital Transformation: iBPMS plays a crucial role in digital transformation initiatives by enabling organizations to innovate, transform, and digitalize processes, operations, and business models.
- Technology Integration: iBPMS integrates with emerging technologies and platforms, including AI, ML, IoT, Cloud, and more, to leverage intelligent capabilities and features.
- Strategic Initiatives: iBPMS supports strategic initiatives, initiatives, projects, and programs aimed at improving performance, competitiveness, growth, and success in the dynamic and evolving business landscape.
In summary, Intelligent Business Process Management (iBPMS) is an advanced and integrated approach to Business Process Management (BPM) that leverages intelligent technologies, capabilities, and features to automate, optimize, manage, and enhance business processes, workflows, tasks, and operations within organizations effectively and efficiently.
iBPMS enables organizations to achieve automation, efficiency, optimization, agility, insights, intelligence, collaboration, innovation, transformation, customer experience, and success in the dynamic and evolving business landscape by integrating traditional BPM with AI, ML, analytics, and intelligent technologies effectively.
Business Management Systems (BMS)
Business Management Systems (BMS) refer to integrated systems, processes, and tools designed to streamline and optimize various aspects of business operations, including planning, execution, monitoring, and control. These systems aim to improve efficiency, productivity, and decision-making across different functional areas of an organization. Business Management Systems can encompass a wide range of components and modules tailored to meet the specific needs and requirements of businesses across various industries.
Here are some key components and characteristics of Business Management Systems:
The following are types of information systems used to create reports, extract data, and assist in the decision making processes of middle and operational level managers.
Marketing information systems are management Information Systems designed specifically for managing the marketing aspects of the business.
Accounting information systems are focused accounting functions.
Human resource management systems are used for personnel aspects.
Content Management
The role of content production
Creating content on the web is crucial for researchers for several reasons:
- Dissemination of Research Findings: Publishing research content online allows researchers to share their findings with a broader audience beyond academic circles. This helps disseminate knowledge and contributes to the advancement of the field.
- Visibility and Impact: By publishing research content online, researchers can increase the visibility and impact of their work. Online platforms provide a global reach, allowing researchers to reach a wider audience and potentially attract collaborators, funding, and opportunities for further research.
- Building Reputation and Credibility: Regularly creating and sharing high-quality research content online helps researchers establish their reputation and credibility in their field. Consistently producing valuable and insightful content enhances researchers' visibility and positions them as thought leaders in their area of expertise.
- Networking and Collaboration: Online platforms facilitate networking and collaboration among researchers from different institutions and disciplines. By sharing their research content online, researchers can connect with peers, exchange ideas, and collaborate on projects, leading to interdisciplinary research opportunities and new insights.
- Engagement with Stakeholders: Creating content on the web allows researchers to engage with various stakeholders, including policymakers, industry professionals, and the general public. By translating their research findings into accessible and understandable content, researchers can contribute to informed decision-making and public discourse on important issues.
- Access to Resources and Information: Online platforms provide researchers with access to a wealth of resources and information relevant to their research interests. By actively participating in online communities, forums, and social media platforms, researchers can stay updated on the latest developments, trends, and opportunities in their field.
- Promoting Open Science and Transparency: Publishing research content online promotes open science principles, including transparency, reproducibility, and accessibility. Making research findings openly available online allows other researchers to verify and build upon existing work, fostering collaboration and innovation.
- Educational Outreach: Research content created on the web can serve as educational resources for students, educators, and lifelong learners. Researchers can use online platforms to share educational materials, tutorials, and resources, helping to inspire and educate the next generation of researchers and professionals.
- Attracting and Engaging Audiences: High-quality content attracts visitors to your website, social media profiles, or other online platforms. Engaging content keeps them interested, encourages interaction, and fosters a sense of community around your brand.
- Building Brand Authority and Trust: Regularly producing valuable, informative, and relevant content establishes your expertise and authority in your industry or niche. This helps build trust with your audience and positions your brand as a credible source of information.
- Improving Search Engine Visibility: Search engines prioritize websites that consistently produce fresh, relevant, and high-quality content. By regularly updating your website with new content, you can improve your search engine rankings and visibility, driving organic traffic to your site.
- Driving Traffic and Conversions: Content marketing plays a crucial role in driving traffic to your website and converting visitors into leads or customers. Compelling content that addresses the needs and pain points of your target audience can influence their purchasing decisions and drive conversions.
- Supporting Customer Education and Engagement: Content provides an opportunity to educate your audience about your products, services, and industry-related topics. By addressing common questions, concerns, and challenges, you can help customers make informed decisions and build long-term relationships.
- Fostering Brand Loyalty and Advocacy: By consistently delivering valuable content that resonates with your audience, you can foster brand loyalty and advocacy. Satisfied customers are more likely to engage with your brand, refer others, and become brand advocates themselves.
- Staying Competitive: In today's digital landscape, content production is a cornerstone of online marketing strategies. To stay competitive, businesses need to invest in creating high-quality content that stands out from the competition and captures the attention of their target audience.
- Adapting to Changing Consumer Behaviors: Consumer behaviors and preferences are constantly evolving, especially in the digital realm. By regularly producing content and staying attuned to audience feedback, businesses can adapt their strategies to meet changing consumer needs and expectations.
- Building Online Presence: Content creation is crucial for establishing and maintaining an online presence. Whether you're an individual, a small business, or a large corporation, having a presence on the web through websites, blogs, social media, or other platforms is vital for visibility and credibility.
- Engaging with Audiences: Content serves as a means to engage with your target audience, whether it's through informative articles, entertaining videos, engaging social media posts, or interactive website content. By creating valuable and relevant content, you can capture the attention of your audience and foster meaningful interactions.
- Driving Traffic and Conversions: High-quality content attracts visitors to your website or online platforms, driving traffic and potentially leading to conversions. Whether your goal is to generate leads, increase sales, or grow your audience, compelling content can help drive the desired actions from your audience.
- Establishing Authority and Expertise: Creating and sharing valuable content in your niche or industry helps establish your authority and expertise. By providing valuable insights, tips, and information, you can position yourself or your brand as a trusted resource and thought leader in your field.
- Improving Search Engine Visibility: Search engines prioritize websites and content that are relevant, authoritative, and regularly updated. By consistently creating high-quality content optimized for search engines, you can improve your website's visibility and rankings in search engine results pages (SERPs).
- Building Relationships and Trust: Content creation fosters relationships with your audience by providing value, addressing their needs, and offering solutions to their problems. Over time, this builds trust and loyalty, leading to stronger relationships and increased customer retention.
- Demonstrating Brand Personality and Values: Content allows you to showcase your brand's personality, values, and culture. Whether it's through storytelling, behind-the-scenes glimpses, or user-generated content, you can humanize your brand and connect with your audience on a deeper level.
- Educating and Informing: Content serves as a powerful tool for educating and informing your audience about your products, services, industry trends, and relevant topics. By sharing valuable insights and expertise, you can help your audience make informed decisions and solve their problems.
- Staying Competitive: In today's digital landscape, content creation is essential for staying competitive. With countless brands and individuals vying for attention online, creating high-quality, engaging content sets you apart and helps you stand out from the competition.
In summary, creating content on the web is essential for researchers to disseminate their findings, increase their visibility and impact, build their reputation, collaborate with peers, engage with stakeholders, access resources, promote open science, and contribute to educational outreach efforts. By leveraging online platforms effectively, researchers can maximize the reach and influence of their research and make a meaningful contribution to their field and society as a whole.
Search Engine Optimization (SEO)
Search Engine Optimization (SEO) is the practice of optimizing a website to improve its visibility and ranking in search engine results pages (SERPs). The goal of SEO is to increase organic (non-paid) traffic to a website by making it more relevant and authoritative in the eyes of search engines like Google, Bing, and Yahoo. Here are key components and strategies of SEO:
- Keyword Research: Identify relevant keywords and phrases that users are likely to search for when looking for products, services, or information related to your business.
- On-Page SEO: Optimize on-page elements such as titles, meta descriptions, headings, URLs, and content with target keywords to make them more relevant to search queries.
- Content Quality and Relevance: Create high-quality, informative, and engaging content that meets the needs of your target audience and provides value. Content should be original, well-written, and optimized for search engines.
- Technical SEO: Improve website structure, navigation, and performance to enhance crawling and indexing by search engine bots. This includes optimizing site speed, mobile-friendliness, URL structure, internal linking, and fixing technical issues.
- Link Building: Acquire high-quality backlinks from reputable websites to improve your site's authority and credibility. This can be done through guest blogging, influencer outreach, directory submissions, and content promotion.
- User Experience (UX) Optimization: Ensure a positive user experience by improving site usability, accessibility, and readability. This includes optimizing page layout, design, and navigation to make it easy for users to find what they're looking for.
- Local SEO: Optimize your website for local search by creating and optimizing Google My Business listings, local citations, and geo-targeted content. This is especially important for businesses targeting local customers.
- Analytics and Monitoring: Use tools like Google Analytics and Google Search Console to track website performance, monitor keyword rankings, and analyze user behavior. This data can help identify areas for improvement and measure the effectiveness of your SEO efforts.
- Continuous Optimization: SEO is an ongoing process that requires regular monitoring, analysis, and optimization. Stay updated on search engine algorithm changes, industry trends, and best practices to maintain and improve your website's search visibility over time.
By implementing these SEO strategies and best practices, businesses can increase their online visibility, attract more organic traffic, and ultimately, achieve their digital marketing goals.
Enterprise Content Management (ECM)
Enterprise Content Management (ECM) refers to the strategies, processes, and technologies used by organizations to capture, manage, store, preserve, and deliver information and documents related to their business operations. ECM systems are designed to streamline document management, improve collaboration, ensure regulatory compliance, and enhance information access and retrieval across the enterprise. Here are key components and features of ECM:
- Document Capture: ECM systems facilitate the capture of various types of documents and content, including paper documents, electronic files, emails, images, and multimedia files. This can be done through scanning, digital ingestion, email integration, and automated data capture technologies.
- Document Management: ECM platforms provide centralized repositories for storing, organizing, and managing documents and content in a structured and secure manner. This includes version control, document check-in/check-out, metadata tagging, and access controls to ensure document integrity and security.
- Workflow Automation: ECM systems automate business processes and workflows related to document management, review, approval, and collaboration. Workflow automation streamlines document routing, task assignment, notifications, and escalations, improving efficiency and productivity.
- Records Management: ECM solutions offer records management capabilities to classify, retain, and dispose of records in accordance with legal, regulatory, and compliance requirements. This includes retention policies, records retention schedules, audit trails, and e-discovery capabilities.
- Document Collaboration and Sharing: ECM platforms facilitate collaboration among users by enabling real-time document sharing, co-authoring, and commenting. Users can collaborate on documents from any location and device, improving teamwork and productivity.
- Search and Retrieval: ECM systems provide advanced search capabilities to quickly locate and retrieve documents and information based on metadata, full-text search, and content indexing. This ensures users can find the information they need when they need it, reducing search time and increasing efficiency.
- Security and Access Control: ECM solutions enforce security policies and access controls to protect sensitive information and prevent unauthorized access, modification, or deletion of documents. This includes user authentication, encryption, role-based permissions, and audit trails.
- Integration and Interoperability: ECM platforms integrate with other enterprise systems and applications, such as ERP, CRM, and collaboration tools, to ensure seamless information exchange and interoperability. Integration enables ECM to serve as a central repository for all enterprise content.
- Compliance and Governance: ECM systems help organizations maintain compliance with regulatory requirements, industry standards, and internal policies governing document management and information security. This includes compliance reporting, policy enforcement, and risk management.
Overall, Enterprise Content Management (ECM) plays a critical role in managing the lifecycle of information and documents within organizations, from creation and capture to storage, distribution, and disposition. By implementing ECM solutions, businesses can improve operational efficiency, enhance collaboration, mitigate risks, and achieve better control and visibility over their content assets.
Knowledge Management System (KMS)
Knowledge Management System (KMS) is a specialized software solution and platform designed to facilitate the creation, organization, storage, retrieval, sharing, dissemination, and management of knowledge, information, expertise, and intellectual assets within organizations, businesses, institutions, and communities. KMS enables individuals, teams, departments, and organizations to capture, document, categorize, collaborate, and leverage knowledge and insights to enhance decision-making, problem-solving, innovation, learning, productivity, performance, and competitiveness in the dynamic and evolving landscape of knowledge-based economies and industries.
Components of Knowledge Management System (KMS):
- Knowledge Creation and Capture:
- Content Management: Enables creation, editing, formatting, and management of knowledge content, documents, articles, reports, and multimedia.
- Knowledge Capture: Facilitates capturing, documenting, and recording of tacit and explicit knowledge, expertise, insights, experiences, and best practices from individuals, teams, and departments.
- Knowledge Organization and Storage:
- Taxonomies and Ontologies: Provides taxonomies, ontologies, and classification schemes to organize, structure, and categorize knowledge content, resources, and information.
- Knowledge Repositories: Offers centralized repositories, databases, libraries, and knowledge bases to store, archive, and manage knowledge assets, documents, data, and information.
- Knowledge Retrieval and Search:
- Search and Retrieval: Enables search, retrieval, and access to knowledge content, resources, documents, data, and information using keywords, tags, filters, and advanced search capabilities.
- Knowledge Discovery: Supports knowledge discovery, exploration, and navigation to uncover, explore, and access relevant knowledge, insights, and resources.
- Knowledge Sharing and Collaboration:
- Collaboration Tools: Integrates collaboration tools, platforms, and features to facilitate knowledge sharing, communication, interaction, and collaboration among individuals, teams, and communities.
- Community and Social Learning: Promotes community, social learning, networking, and engagement to foster sharing, collaboration, and exchange of knowledge, ideas, and experiences.
- Knowledge Security and Governance:
- Access Control and Permissions: Implements access control, permissions, and security measures to protect, secure, and manage access to sensitive and confidential knowledge, information, and data.
- Compliance and Governance: Ensures compliance with knowledge management policies, regulations, standards, and governance for integrity, ethics, and responsible management of knowledge assets and resources.
Advantages of Knowledge Management System (KMS):
- Enhanced Decision-Making and Problem-Solving: Enables informed decision-making, problem-solving, and innovation by providing access to relevant, timely, and accurate knowledge, information, insights, and expertise.
- Increased Productivity and Efficiency: Optimizes utilization, sharing, and application of knowledge and expertise to enhance productivity, efficiency, and performance across individuals, teams, and organizations.
- Fostering Innovation and Learning: Fosters a culture of innovation, creativity, learning, and continuous improvement by encouraging knowledge sharing, collaboration, experimentation, and exploration.
- Knowledge Retention and Continuity: Preserves, captures, and retains organizational knowledge, expertise, and intellectual assets to ensure continuity, sustainability, and resilience amid organizational changes, transitions, and challenges.
- Competitive Advantage and Growth: Provides a competitive advantage, positioning, and differentiation by leveraging and leveraging organizational knowledge, insights, capabilities, and expertise to drive growth, differentiation, and success in the marketplace.
Challenges of Knowledge Management System (KMS):
- Knowledge Silos and Fragmentation:
- Knowledge Silos: Faces challenges with knowledge silos, fragmentation, duplication, inconsistency, and isolation requiring integration, alignment, and synchronization of knowledge across individuals, teams, and departments.
- Adoption and Engagement:
- User Adoption: Encounters issues with user adoption, engagement, motivation, and participation requiring training, awareness, communication, and incentives to encourage and sustain knowledge sharing and collaboration.
- Content Quality and Relevance:
- Content Management: Faces challenges with content quality, relevance, accuracy, currency, completeness, and maintenance requiring governance, standards, guidelines, and quality assurance.
- Technology and Integration:
- Technology Integration: Encounters issues with technology integration, compatibility, scalability, and alignment with existing systems, platforms, and infrastructures requiring investment, innovation, and IT support.
In summary, Knowledge Management System (KMS) is a pivotal platform and tool for facilitating, managing, and enhancing the creation, organization, storage, retrieval, sharing, dissemination, and management of knowledge, information, expertise, and intellectual assets within organizations and communities. KMS empowers individuals, teams, departments, and organizations with the capabilities, tools, and resources to capture, document, categorize, collaborate, and leverage knowledge and insights to enhance decision-making, problem-solving, innovation, learning, productivity, performance, and competitiveness in the dynamic and evolving landscape of knowledge-based economies and industries. By embracing and adopting KMS, organizations can optimize knowledge management, collaboration, communication, learning, growth, and success to achieve organizational goals, objectives, and aspirations in the interconnected, competitive, and knowledge-driven world of today and tomorrow.
Social Network Management System(SNMS)
A Social Network Management System (SNMS) is a software platform or tool designed to manage, monitor, and analyze social media channels and interactions from a single dashboard. It enables individuals, brands, or organizations to streamline their social media marketing efforts, engage with their audience, and monitor their social media performance across various social networks such as Facebook, Twitter, Instagram, LinkedIn, YouTube, and more.
Key Features of Social Network Management System
- Social Media Monitoring: Tracks mentions, comments, likes, shares, and other interactions across multiple social media platforms in real-time.
- Content Scheduling and Publishing: Enables users to schedule and publish posts, tweets, images, and videos across multiple social media channels at optimal times.
- Engagement and Interaction: Facilitates engagement with followers, fans, and users by responding to comments, messages, and mentions directly from the dashboard.
- Analytics and Reporting: Provides comprehensive analytics, insights, and reports on social media performance, audience engagement, growth, and ROI.
- Social Listening: Monitors conversations, trends, and discussions related to specific keywords, hashtags, or topics to gain insights into audience preferences, sentiments, and behaviors.
- Team Collaboration: Offers collaboration tools and features to manage multiple users, roles, permissions, and workflows within the social media management team.
- Content Curation: Helps users discover, curate, and share relevant content, articles, news, and trends to keep their audience informed and engaged.
- Social CRM Integration: Integrates with Customer Relationship Management (CRM) systems to manage and track social media interactions, leads, and customer relationships.
- Advertising and Promotion: Provides tools for creating, managing, and optimizing social media advertising campaigns and promotions across various platforms.
Benefits of Social Network Management System
- Efficiency and Productivity: Streamlines social media management tasks, reduces manual efforts, and improves productivity by centralizing social media activities and workflows.
- Audience Engagement: Enhances audience engagement, interaction, and relationship-building by providing tools to monitor, respond, and engage with followers and users effectively.
- Data-Driven Decisions: Enables data-driven decision-making by providing actionable insights, analytics, and performance metrics to optimize social media strategies and campaigns.
- Brand Consistency: Ensures brand consistency and messaging across all social media channels by providing centralized control over content, visuals, and communications.
- Compliance and Security: Ensures compliance with social media policies, regulations, and industry standards, while implementing security measures to protect social media accounts and data.
- ROI and Performance Tracking: Enables tracking and measurement of social media ROI, performance, and KPIs to evaluate the effectiveness of social media marketing efforts and investments.
Popular Social Network Management Platforms
- Hootsuite: A widely-used social media management platform that offers a comprehensive suite of tools for managing, monitoring, and analyzing social media channels.
- Buffer: A user-friendly social media management platform that enables users to schedule, publish, and analyze social media content across various platforms.
- Sprout Social: A robust social media management and analytics platform that offers engagement, publishing, monitoring, and reporting tools for businesses and agencies.
- HubSpot Social Media Management: Part of the HubSpot CRM platform, it provides tools for social media monitoring, publishing, engagement, and analytics.
- SocialBee: A social media management tool that offers content scheduling, posting, and automation features to help businesses maintain an active presence on social media.
In summary, a Social Network Management System plays a pivotal role in managing and optimizing social media marketing efforts by providing tools, features, and insights to streamline social media management, engage with the audience, and monitor performance effectively. Whether it's scheduling posts, responding to comments, analyzing data, or running advertising campaigns, a well-equipped social network management system can help individuals, brands, and organizations navigate the complexities of social media marketing and achieve their social media goals more efficiently and effectively.
Content Management System (CMS)
Definition: A Content Management System (CMS) is a software platform that enables users to create, manage, publish, and organize digital content, such as text, images, videos, and documents, on websites and online platforms. CMS provides tools and features to design, customize, and manage website content, structure, navigation, and appearance without requiring technical expertise or coding knowledge.
Key Components:
- Content Creation and Editing: Enables users to create, edit, and format digital content using a WYSIWYG editor.
- Content Organization and Management: Organizes and manages content into categories, tags, and folders for easy navigation and retrieval.
- Content Publishing and Distribution: Publishes and distributes content to websites, platforms, and channels.
- User Management and Permissions: Manages user roles, permissions, and access to content and features.
- Design and Customization: Customizes website design, layout, themes, and templates.
Headless CMS and traditional CMS
Headless CMS and traditional CMS are two different approaches to content management systems, each with its own advantages and use cases:
Traditional CMS:
- Monolithic Structure: Traditional CMS platforms typically come with a built-in frontend and backend. They are designed to manage content, handle presentation logic, and serve web pages all in one package.
- Coupled Frontend and Backend: In traditional CMS, the frontend (presentation layer) and backend (content management and database) are tightly coupled. This means that content creation, management, and display are all tightly integrated into a single system.
- Ease of Use: Traditional CMS platforms often provide user-friendly interfaces for content editors and administrators to create, edit, and publish content without needing technical expertise.
- Template-based Approach: Traditional CMS platforms use templates to define the structure and layout of web pages. Content creators use these templates to add content, and the CMS handles the presentation automatically.
- Limited Flexibility: While traditional CMS platforms are easy to use and set up, they may offer limited flexibility in terms of customizing the frontend or integrating with external systems.
Headless CMS:
- Decoupled Architecture: Headless CMS decouples the backend (content management) from the frontend (presentation layer). This means that content is managed separately from how it is displayed.
- Content API: Headless CMS provides content via APIs (RESTful or GraphQL), allowing developers to retrieve content and display it on any device or platform, such as websites, mobile apps, IoT devices, etc.
- Flexibility and Customization: With a headless CMS, developers have complete control over the presentation layer. They can use any frontend technology (such as React, Vue.js, Angular) to build custom user interfaces and experiences.
- Scalability: Headless CMS platforms are highly scalable and can handle large volumes of content and traffic since the frontend and backend are decoupled.
- Content Reuse: Content stored in a headless CMS can be reused across multiple channels and platforms, allowing for consistent messaging and branding.
- Future-proofing: By separating content from presentation, headless CMS provides a future-proof solution that can adapt to new technologies and devices without requiring a complete overhaul of the content management system.
Decoupled CMS:
- Hybrid Approach: Decoupled CMS is a combination of traditional and headless CMS. It provides the option to use the built-in frontend of the CMS or decouple the frontend for custom development.
- Separation of Concerns: Similar to headless CMS, decoupled CMS separates content management from content presentation. However, it still offers the option to use the built-in frontend for content display.
- Flexibility: Decoupled CMS provides flexibility for organizations that require some level of customization in the frontend but also want the convenience of built-in features for content presentation.
- Content API: Decoupled CMS platforms often offer APIs for accessing content, allowing developers to build custom frontend applications while still leveraging the CMS for content management.
Use Cases:
-
Traditional CMS: Ideal for websites and applications where content editors need a user-friendly interface to manage content, and customization of the frontend is not a priority.
-
Headless CMS: Suitable for projects where flexibility, scalability, and content reuse across multiple channels and platforms are important. Commonly used for websites, mobile apps, IoT applications, digital signage, etc.
-
Decoupled CMS: Offers a middle ground for organizations that require some level of customization in the frontend but also want the convenience of built-in features for content presentation. Often used in projects where flexibility and scalability are desired without sacrificing ease of use for content editors.
Document Management System (DMS)
Definition: A Document Management System (DMS) is a software platform designed to capture, store, manage, retrieve, track, and secure documents, files, and records within organizations. DMS provides tools and features to digitize, organize, categorize, index, version control, and archive documents and files to enhance collaboration, accessibility, security, and compliance.
Key Components:
- Document Capture and Scanning: Digitizes and captures documents and files using scanning and OCR technologies.
- Document Storage and Retrieval: Stores and retrieves documents and files in a centralized repository or cloud storage.
- Document Organization and Indexing: Organizes, categorizes, and indexes documents and files for easy navigation and retrieval.
- Document Collaboration and Sharing: Facilitates collaboration, sharing, and co-authoring of documents and files among users.
- Document Security and Compliance: Ensures document security, access control, encryption, and compliance with regulations and standards.
Comparison
| Criteria |
Content Management System (CMS) |
Document Management System (DMS) |
| Focus |
Digital Content and Website Management |
Document and File Management |
| Primary Objective |
Manage, Publish, and Organize Content |
Capture, Store, and Manage Documents |
| Key Components |
Content Creation, Publishing, Design |
Document Capture, Storage, Retrieval |
| Content Types |
Web Content, Images, Videos, Documents |
Documents, Files, Records |
| User Base |
Content Creators, Editors, Administrators |
Document Managers, Employees, Teams |
| Customization |
Customizable Design, Themes, Templates |
Customizable Indexing, Metadata, Forms |
| Collaboration |
Content Collaboration and Publishing |
Document Collaboration and Sharing |
| Security and Compliance |
Content Security, Permissions, Access |
Document Security, Encryption, Compliance |
| Integration |
Integrates with Web Platforms, Extensions |
Integrates with CRM, ERP, Email, Cloud |
Conclusion:
-
Content Management System (CMS) is focused on managing, publishing, and organizing digital content, such as text, images, videos, and documents, on websites and online platforms. CMS provides tools and features to create, edit, design, customize, and publish web content without technical expertise.
-
Document Management System (DMS) is specialized for capturing, storing, managing, retrieving, tracking, and securing documents, files, and records within organizations. DMS provides tools and features to digitize, organize, categorize, index, version control, collaborate, share, and secure documents and files effectively.
While both CMS and DMS aim to manage and organize digital content and documents, they have distinct focuses and objectives:
-
CMS is tailored for website content management, publishing, design, and customization to manage and present digital content effectively and attractively on websites and online platforms.
-
DMS is designed for document and file management, organization, storage, retrieval, collaboration, sharing, and security to manage and control documents and records securely and compliantly within organizations.
Organizations may adopt CMS, DMS, or both depending on their needs, objectives, and requirements to manage digital content, documents, and information effectively and efficiently in the dynamic and evolving digital landscape.
Information Systems (IS) in Education
Information Systems (IS) in education refer to the integrated systems and technologies used to manage, process, analyze, and disseminate information within educational institutions. These systems play a pivotal role in enhancing teaching and learning, administrative efficiency, decision-making, and communication. Here are the key areas where Information Systems are applied in education:
1. Educational Management Information System (EMIS):
- Purpose: Manages administrative and operational aspects of education.
- Features:
- Student information management (enrollment, attendance, grades).
- Faculty and staff management.
- Curriculum and course management.
- Financial management (budgeting, expenditures, payroll).
- Benefits: Enhances efficiency, transparency, accountability, and decision-making in educational management.
2. Learning Management System (LMS):
- Purpose: Facilitates online and blended learning environments.
- Features:
- Course management and content delivery.
- Online assessments and grading.
- Communication and collaboration tools.
- Student tracking and analytics.
- Benefits: Enables flexible learning experiences, collaboration, personalized instruction, and student engagement.
3. Student Information System (SIS):
- Purpose: Manages student-related data and processes.
- Features:
- Student profiles and academic records.
- Enrollment and registration.
- Attendance and behavior tracking.
- Reporting and analytics.
- Benefits: Streamlines student administration, enhances data accuracy, accessibility, and supports informed decision-making.
4. Library Management System (LMS):
- Purpose: Manages library resources, services, and operations.
- Features:
- Cataloging and circulation.
- Resource management and acquisitions.
- Patron management and services.
- Reporting and analytics.
- Benefits: Improves library operations, enhances resource accessibility, searchability, and user experience.
5. Research Management Information System (RMIS):
- Purpose: Supports research administration, tracking, and compliance.
- Features:
- Research project and grant management.
- Funding opportunities and applications.
- Publication tracking and reporting.
- Compliance and regulatory management.
- Benefits: Facilitates research management, enhances compliance, transparency, and supports research excellence.
6. Collaboration and Communication Systems:
- Purpose: Enhances communication, collaboration, and networking.
- Features:
- Email, messaging, and communication tools.
- Collaboration platforms and tools (e.g., Google Workspace, Microsoft Teams).
- Networking and community engagement platforms.
- Benefits: Facilitates communication, collaboration, knowledge sharing, and community building among stakeholders.
In summary, Information Systems (IS) in education encompass a wide range of systems and technologies designed to support and enhance various aspects of education, including management, teaching, learning, administration, research, and communication. By leveraging Information Systems effectively, educational institutions can streamline operations, enhance teaching and learning experiences, improve administrative efficiency, support research excellence, and foster collaboration and communication among stakeholders. As technology continues to evolve, the role and impact of Information Systems in education will continue to grow, driving innovation, transformation, and excellence in the education sector.
Specialized Information Systems designed for Educational Managment:
Academic Management Information Systems (AMIS)
Management of Academic Information System (AIS)
Academic Management Information System (ACMIS)
Quizzes, Tests, and Exams
A software system for quizzes, tests, and exams in educational or corporate settings typically includes a range of features to facilitate the creation, administration, and assessment of assessments. Here are some key components and features that such a system may include:
- Question Bank Management: A centralized repository for storing, organizing, and managing questions. This allows educators or administrators to create, edit, categorize, and tag questions for easy retrieval and reuse.
- Question Authoring Tools: Tools for creating and formatting various types of questions, including multiple-choice, true/false, short answer, essay, and more. These tools may include rich text editors, multimedia integration, and support for mathematical equations or diagrams.
- Assessment Creation: Functionality to assemble quizzes, tests, or exams by selecting questions from the question bank. Educators can create customized assessments with specified parameters such as question randomization, time limits, and scoring rules.
- Delivery Modes: Options for administering assessments in different formats, including online, offline, synchronous, or asynchronous modes. This may include web-based testing platforms, mobile apps, or printable paper-based exams.
- Remote Proctoring: Integration with remote proctoring services or features to monitor student behavior and prevent cheating during online exams. This may include webcam monitoring, screen recording, identity verification, and AI-powered proctoring algorithms.
- Scoring and Grading: Automated scoring and grading functionality to streamline the assessment process. The system should support various scoring methods, including automatic grading for multiple-choice questions and manual grading for subjective responses.
- Analytics and Reporting: Analytics dashboards and reporting tools to provide insights into student performance, item analysis, and assessment outcomes. Educators can use this data to identify areas for improvement, track student progress, and adjust teaching strategies accordingly.
- Feedback and Review: Options for providing feedback and reviewing assessment results to students. This may include immediate feedback after completing an assessment, detailed score reports, and opportunities for students to review their answers.
- Security and Integrity: Robust security measures to protect the integrity of assessments and prevent cheating. This includes features such as secure login authentication, browser lockdown, question randomization, and encrypted data transmission.
- Accessibility: Accessibility features to accommodate diverse learners, including those with disabilities. This may include support for screen readers, alternative formats, captioning, adjustable fonts, and color contrast options.
- Integration with Learning Management Systems (LMS): Seamless integration with LMS platforms to streamline course management, enrollment, and grade synchronization. This allows educators to deliver assessments within the context of their existing learning environment.
- Customization and Branding: Customization options to align the assessment system with the organization's branding and visual identity. This may include custom logos, colors, themes, and branding elements.
By incorporating these features into a comprehensive software system, educators and organizations can streamline the assessment process, enhance the integrity of exams, and provide valuable feedback to learners. Additionally, students benefit from a more efficient and effective assessment experience, leading to improved learning outcomes.
Content Authoring Tools
A software system for textbooks and presentations in educational settings typically encompasses various functionalities to facilitate content creation, organization, delivery, and presentation. Here are some key components and features that such a system may include:
- Content Authoring Tools: Authoring tools allow educators or content creators to create and customize digital textbooks, presentations, lecture materials, and learning resources. These tools may include text editors, slide editors, multimedia integration features, templates, and interactive elements.
- Multimedia Integration: Support for integrating multimedia elements such as images, videos, audio clips, animations, and interactive simulations into textbooks and presentations. This enhances engagement and facilitates more dynamic and interactive learning experiences.
- Content Organization and Navigation: Features for organizing and structuring content within textbooks and presentations, including chapters, sections, headings, and subheadings. Intuitive navigation tools make it easy for users to navigate through the content and find relevant information.
- Interactive Elements: Interactive features such as hyperlinks, navigation buttons, interactive quizzes, polls, and surveys add interactivity to textbooks and presentations, promoting active learning and engagement.
- Collaboration and Co-authoring: Collaboration tools that allow multiple users to collaborate on the creation and editing of textbooks and presentations in real-time. Users can collaborate remotely, share feedback, and work together to create high-quality content.
- Version Control: Version control features ensure that changes to textbooks and presentations are tracked, documented, and easily reversible. This helps prevent version conflicts and ensures that users always have access to the latest version of the content.
- Accessibility Features: Accessibility features to ensure that textbooks and presentations are accessible to users with disabilities. This may include support for screen readers, alternative text for images, captioning for videos, and adjustable font sizes and colors.
- Export and Sharing Options: Options for exporting and sharing textbooks and presentations in various formats, including PDF, PowerPoint, HTML, and e-book formats. Users can easily share content with students, colleagues, or other stakeholders.
- Integration with Learning Management Systems (LMS): Integration with LMS platforms allows seamless integration of textbooks and presentations into course materials. This enables educators to deliver content within the context of their existing learning environment and track student engagement and progress.
- Analytics and Usage Tracking: Analytics dashboards and usage tracking tools provide insights into how textbooks and presentations are being used, including metrics such as views, engagement, and interactions. Educators can use this data to assess the effectiveness of their content and make data-driven decisions.
- Customization and Branding: Customization options to align textbooks and presentations with the organization's branding and visual identity. This may include custom logos, colors, themes, and branding elements.
By incorporating these features into a comprehensive software system, educational institutions can create engaging, interactive, and accessible textbooks and presentations that enhance the learning experience for students and educators alike.
Textbooks, Question
A software system for textbooks, tests, and exams in educational settings typically encompasses various functionalities to facilitate content creation, delivery, assessment, and management. Here are some key components and features that such a system may include:
- Content Authoring Tools: Authoring tools allow educators to create and customize digital textbooks, study materials, and learning resources. These tools may include text editors, multimedia integration features, interactive elements, and templates for designing engaging content.
- Content Management System (CMS): A CMS enables the organization, storage, and retrieval of digital textbooks, lecture notes, study guides, and other educational resources. It provides a centralized repository for content management, version control, and access control.
- Learning Management System (LMS): An LMS serves as a platform for delivering educational content, conducting assessments, and tracking student progress. It may include features such as course management, student enrollment, gradebook, discussion forums, and communication tools.
- Assessment and Testing Tools: These tools allow educators to create, administer, and grade tests, quizzes, and exams digitally. They may include question banks, randomization features, automated grading, and analytics for assessing student performance.
- Online Exam Proctoring: Some systems may integrate online exam proctoring features to monitor student behavior and prevent cheating during remote exams. This may include webcam monitoring, screen recording, and AI-powered proctoring algorithms.
- Accessibility and Accommodations: Software systems for textbooks and exams should prioritize accessibility features to accommodate diverse learners, including those with disabilities. This may include support for screen readers, alternative formats, captioning, and adjustable fonts.
- Integration with Learning Tools: Integration with third-party learning tools and platforms, such as educational apps, simulations, and virtual labs, can enhance the learning experience and provide additional resources for students and educators.
- Analytics and Reporting: Analytical tools provide insights into student engagement, performance trends, and learning outcomes. Educators can use analytics dashboards and reports to identify areas for improvement, track student progress, and make data-driven decisions.
- Security and Data Privacy: Robust security measures are essential to protect sensitive student data, exam content, and intellectual property. Software systems should comply with data privacy regulations and implement encryption, authentication, and access control mechanisms.
- Mobile Compatibility: With the increasing use of mobile devices in education, software systems should be compatible with smartphones and tablets, allowing students to access textbooks, study materials, and exams anytime, anywhere.
- Customization and Scalability: Flexible and scalable software solutions allow educational institutions to customize the system according to their specific needs, scale up as the student population grows, and adapt to changing requirements over time.
- User Support and Training: Comprehensive user support and training resources help educators, administrators, and students effectively use the software system. This may include documentation, tutorials, helpdesk support, and professional development opportunities.
By integrating these features into a comprehensive software system, educational institutions can enhance teaching and learning experiences, streamline administrative tasks, and improve student outcomes in textbook creation, testing, and exam administration.
Project Management Systems (PMS)
Project Management Systems: Project management systems help businesses plan, execute, monitor, and control projects effectively. These systems provide tools for task management, resource allocation, time tracking, collaboration, and project reporting to ensure projects are completed on time and within budget.
Project Management Systems (PMS) are software tools designed to help plan, execute, monitor, and control projects effectively. These systems provide a centralized platform for project managers, team members, and stakeholders to collaborate, track progress, and manage project-related tasks, resources, and documentation. Here are some key features and functionalities commonly found in project management systems:
- Task Management: PMS allow users to create, assign, prioritize, and track tasks associated with the project. Tasks can be organized into lists or boards, with features such as deadlines, dependencies, and task assignments.
- Scheduling and Planning: Users can create project schedules, timelines, and milestones using Gantt charts, calendars, or other planning tools. PMS may also support resource allocation, workload balancing, and critical path analysis to optimize project schedules.
- Collaboration and Communication: PMS provide communication tools such as messaging, comments, and notifications to facilitate collaboration among team members. Users can share updates, discuss project-related issues, and provide feedback in real-time.
- Document Management: PMS offer document storage and version control capabilities to manage project documentation, files, and attachments. This ensures that team members have access to the latest project documents and can collaborate on shared files.
- Resource Management: PMS help manage project resources, including human resources, equipment, materials, and budget. Users can allocate resources, track resource utilization, and monitor budget expenses to ensure efficient resource management.
- Risk and Issue Management: PMS enable users to identify, assess, and mitigate project risks and issues. Users can log risks and issues, assign owners, set priorities, and track resolution progress to minimize potential disruptions to the project.
- Reporting and Analytics: PMS provide reporting and analytics tools to track project progress, performance metrics, and key performance indicators (KPIs). Users can generate custom reports, dashboards, and charts to monitor project status and make data-driven decisions.
- Integration with Third-party Tools: PMS often integrate with other business tools and systems such as calendar applications, email clients, document management systems, and collaboration platforms. This allows seamless data exchange and workflow automation across different tools.
- Customization and Configuration: PMS offer customization options to adapt to the unique requirements of each project or organization. Users can configure project settings, workflows, and user permissions to align with specific project needs and organizational processes.
- Mobile Accessibility: Many PMS offer mobile apps or responsive web interfaces, allowing users to access project information, collaborate with team members, and manage tasks on-the-go from their smartphones or tablets.
Overall, Project Management Systems (PMS) play a critical role in helping organizations efficiently plan, execute, and monitor projects, ensuring successful project delivery and achieving business objectives. These systems streamline project workflows, improve collaboration, and provide visibility into project progress and performance.
Compare PMS & PMIS
Project Management Systems (PMS) and Project Management Information Systems (PMIS) are both software tools designed to facilitate project planning, execution, monitoring, and control. While they share similar objectives, there are some differences in their focus and scope:
-
Project Management Systems (PMS):
- PMS typically refer to standalone software tools or platforms specifically designed to manage projects and project-related tasks.
- These systems focus primarily on managing project tasks, schedules, resources, and collaboration among team members.
- PMS may include features such as task management, scheduling, document management, communication tools, and reporting capabilities.
- Examples of PMS include Trello, Asana, Jira, and Basecamp.
-
Project Management Information Systems (PMIS):
- PMIS encompass a broader range of tools, processes, and technologies used to support project management activities within an organization.
- PMIS integrate project management functionalities with other organizational systems and processes, such as enterprise resource planning (ERP) systems, document management systems, and customer relationship management (CRM) systems.
- PMIS focus not only on managing individual projects but also on capturing, analyzing, and disseminating project-related information across the organization.
- PMIS may include features such as project portfolio management, resource allocation, financial management, risk management, and integration with other business systems.
- Examples of PMIS include Microsoft Project Server, Oracle Primavera, SAP Project System, and Planview.
In summary, while both PMS and PMIS are used for project management purposes, PMS are standalone tools focused primarily on managing individual projects, while PMIS encompass a broader set of tools and processes that integrate project management with other organizational systems and processes. PMIS are often used in larger organizations with complex project portfolios and a need for centralized project management capabilities across the enterprise.
Quality Management Systems (QMS)
Quality Management Systems (QMS): QMS focus on ensuring product and service quality by implementing standardized processes, procedures, and controls. These systems help businesses achieve compliance with quality standards, regulations, and customer requirements, while continuously improving quality and customer satisfaction.
Affiliate Marketing Management System
Marketing Information Systems
An Affiliate Marketing Management System is a software platform or solution designed to manage, track, and optimize affiliate marketing programs. It provides advertisers (merchants or brands) and affiliates (publishers or partners) with the tools, features, and functionalities needed to create, launch, monitor, and analyze affiliate marketing campaigns effectively. The system automates various aspects of affiliate marketing, streamlining operations, improving efficiency, and maximizing ROI for both advertisers and affiliates.
Key Features of Affiliate Marketing Management System:
- Affiliate Tracking: Automatically tracks affiliate referrals, clicks, sales, and commissions using unique affiliate links or tracking codes.
- Commission Management: Manages affiliate commissions, payouts, and payment schedules based on predefined commission rates, rules, and thresholds.
- Campaign Management: Enables advertisers to create, launch, and manage multiple affiliate marketing campaigns, promotions, or offers.
- Affiliate Onboarding: Streamlines the process of recruiting, onboarding, and managing affiliates by providing registration, approval, and communication tools.
- Reporting and Analytics: Provides comprehensive reporting and analytics tools to monitor, analyze, and optimize affiliate performance, traffic sources, conversions, and ROI.
- Creative Management: Offers tools for creating, managing, and distributing marketing materials, banners, links, and promotional content to affiliates.
- Fraud Detection and Prevention: Implements fraud detection mechanisms and security measures to identify and prevent fraudulent activities, click fraud, and affiliate abuse.
- Communication Tools: Facilitates communication and collaboration between advertisers and affiliates through messaging, notifications, and alerts.
- Integration Capabilities: Integrates with other marketing platforms, eCommerce platforms, payment gateways, and CRM systems to streamline workflows and data exchange.
Benefits of Affiliate Marketing Management System:
- Efficiency and Automation: Automates repetitive tasks, streamlines operations, and reduces manual efforts in managing affiliate marketing programs.
- Scalability: Enables advertisers to scale their affiliate marketing efforts by managing a large number of affiliates, campaigns, and promotional activities efficiently.
- Data-Driven Decisions: Provides actionable insights, data, and analytics to make informed decisions, optimize performance, and maximize ROI.
- Compliance and Security: Ensures compliance with affiliate agreements, regulations, and industry standards, while implementing security measures to protect against fraud and abuse.
- Improved Collaboration: Facilitates better communication, collaboration, and relationship management between advertisers and affiliates, fostering a productive and mutually beneficial partnership.
Popular Affiliate Marketing Management Platforms:
- Post Affiliate Pro: A comprehensive affiliate marketing platform with advanced tracking, management, and reporting capabilities.
- AffTrack: A cloud-based affiliate marketing platform that offers real-time analytics, tracking, and optimization tools.
- HasOffers by TUNE: A popular affiliate marketing platform with robust tracking, reporting, and campaign management features.
- ClickBank: A global affiliate marketing platform that connects advertisers with affiliates to promote digital products and services.
- ShareASale: An affiliate marketing network and platform that offers a wide range of tools, features, and support for advertisers and affiliates.
In summary, an Affiliate Marketing Management System plays a crucial role in managing and optimizing affiliate marketing programs by providing advertisers and affiliates with the tools, features, and insights needed to succeed. Whether it's tracking affiliate referrals, managing commissions, launching campaigns, or analyzing performance, a well-designed affiliate marketing management system can help advertisers and affiliates streamline operations, improve efficiency, and achieve their affiliate marketing goals more effectively.
School Information Management Systems (SIMS)
School Information Management Systems (SIMS) cover school administration, often including teaching and learning materials.
Educational Management Information System (EMIS)
An Educational Management Information System (EMIS) is a comprehensive system designed to manage and analyze data related to educational institutions, students, teachers, staff, curriculum, and administrative processes. EMIS plays a crucial role in enhancing the efficiency, effectiveness, and accountability of educational management by providing accurate, timely, and relevant information to stakeholders.
Focus:
- Educational Management: Focuses on managing and supporting various aspects of educational institutions, including student information, curriculum, courses, faculty, staff, facilities, finance, and administration.
Key Components:
- Student Information System (SIS): Manages student enrollment, attendance, grades, academic records, and personal information.
- Teacher Information System (TIS): Manages teacher profiles, qualifications, assignments, and performance evaluations.
- Curriculum and Course Management: Manages curriculum frameworks, course offerings, schedules, and resources.
- Financial Management: Manages budgets, funding, expenditures, and financial transactions.
- Facility and Resource Management: Manages school facilities, infrastructure, equipment, and resources.
Key Components of EMIS:
-
Student Information System (SIS):
- Manages student enrollment, attendance, grades, academic records, and personal information.
- Tracks student progress, performance, and achievements over time.
-
Teacher Information System (TIS):
- Manages teacher profiles, qualifications, training, assignments, and performance evaluations.
- Facilitates teacher recruitment, professional development, and training programs.
-
Curriculum and Course Management:
- Manages curriculum frameworks, course offerings, schedules, and resources.
- Tracks curriculum implementation, alignment, and updates based on educational standards and requirements.
-
Financial Management:
- Manages budgets, funding, expenditures, and financial transactions.
- Tracks financial resources, allocations, and utilization across departments and programs.
-
Facility and Resource Management:
- Manages school facilities, infrastructure, equipment, and resources.
- Tracks maintenance, repairs, upgrades, and utilization of facilities and resources.
-
Reporting and Analytics:
- Generates reports, dashboards, and analytics to monitor and evaluate performance, trends, and outcomes.
- Facilitates data-driven decision-making and strategic planning processes.
Key Features of EMIS:
- Data Collection and Integration: Collects, consolidates, and integrates data from various sources and systems within the educational institution.
- Data Validation and Quality Assurance: Ensures data accuracy, consistency, and reliability through validation, verification, and quality assurance processes.
- User Access and Security: Provides secure access controls, user roles, and permissions to safeguard sensitive data and ensure compliance with privacy regulations.
- Scalability and Flexibility: Scalable and adaptable to accommodate growth, changes, and evolving needs of educational institutions over time.
- Interoperability: Interoperable with other systems, platforms, and databases to facilitate seamless data exchange and integration.
Benefits:
- Enhances administrative efficiency and effectiveness.
- Supports strategic planning, policy-making, and decision-making.
- Improves student engagement, performance, and outcomes.
- Enhances transparency, accountability, and governance.
Benefits of EMIS:
- Enhanced Decision Making: Provides accurate, timely, and relevant information to stakeholders for informed decision-making and strategic planning.
- Efficient Operations: Streamlines administrative processes, reduces manual tasks, and enhances operational efficiency across various departments and functions.
- Improved Accountability: Enhances transparency, accountability, and governance by tracking performance, compliance, and outcomes.
- Data-Driven Insights: Enables data-driven insights, analytics, and reporting to monitor, evaluate, and improve educational performance, outcomes, and stakeholder satisfaction.
In summary, An Educational Management Information System (EMIS) is a comprehensive solution that plays a vital role in managing, analyzing, and leveraging data to enhance educational management and outcomes. By integrating various components, features, and functionalities, EMIS empowers educational institutions to streamline operations, improve decision-making, enhance accountability, and deliver quality education to students. As technology continues to evolve, EMIS will continue to play a crucial role in transforming educational management and fostering innovation, efficiency, and excellence in the education sector.
Educational Management Information System (EMIS) and Research Management Information System (RMIS) are both specialized information systems designed to support and enhance management, operations, and decision-making within educational and research institutions, respectively. While they share some similarities in terms of managing information, data, and processes, they also have distinct features, focuses, and functionalities tailored to the unique needs and requirements of education and research management. Let's explore the differences and similarities between EMIS and RMIS:
Research Management Information System (RMIS)
A Research Management Information System (RMIS) is a specialized system designed to support and streamline the management of research activities, projects, grants, funding, publications, collaborations, and compliance within academic, government, and private research institutions. RMIS plays a crucial role in enhancing the efficiency, effectiveness, and transparency of research management by providing comprehensive tools and functionalities to researchers, administrators, and stakeholders.
Focus:
- Research Management: Focuses on managing and supporting various aspects of research activities, projects, grants, funding, publications, collaborations, compliance, and reporting within academic, government, and private research institutions.
Key Components:
- Research Project Management: Manages research projects, grants, funding sources, timelines, milestones, deliverables, and budgets.
- Grants and Funding Management: Manages grants, funding opportunities, applications, approvals, disbursements, and reporting.
- Researcher Profiles and Expertise: Manages researcher profiles, expertise, qualifications, publications, projects, and collaborations.
- Publications and Outputs Management: Manages research publications, citations, bibliographic information, impact metrics, and dissemination.
- Compliance and Regulatory Management: Ensures compliance with research ethics, regulations, standards, policies, and reporting requirements.
Benefits:
- Enhances research efficiency, productivity, and collaboration.
- Facilitates compliance, governance, and reporting.
- Enables data-driven insights, analytics, and decision-making.
- Fosters innovation, excellence, and impact in research.
Comparison:
-
EMIS: Focuses on managing and supporting educational management, operations, and processes within educational institutions, including student information, faculty, curriculum, finance, facilities, and administration.
-
RMIS: Focuses on managing and supporting research activities, projects, grants, funding, publications, collaborations, compliance, and reporting within academic, government, and private research institutions.
In summary, while both Educational Management Information System (EMIS) and Research Management Information System (RMIS) are specialized information systems designed to support and enhance management, operations, and decision-making within educational and research institutions, they differ in focus, components, and benefits. EMIS focuses on managing and supporting educational management and operations, while RMIS focuses on managing and supporting research activities and projects. By leveraging the unique features, functionalities, and benefits of EMIS and RMIS, educational and research institutions can streamline management, enhance collaboration, improve efficiency, and achieve excellence in education and research across various disciplines and fields.
Key Components of RMIS:
- Research Project Management:
- Manages research projects, grants, funding sources, timelines, milestones, deliverables, and budgets.
- Tracks project progress, expenditures, and compliance with grant requirements and regulations.
- Grants and Funding Management:
- Manages grants, funding opportunities, applications, approvals, disbursements, and reporting.
- Tracks funding sources, allocations, utilization, and compliance with grant conditions and regulations.
- Researcher Profiles and Expertise:
- Manages researcher profiles, expertise, qualifications, publications, projects, and collaborations.
- Facilitates researcher identification, networking, collaboration, and expertise matching.
- Publications and Outputs Management:
- Manages research publications, citations, bibliographic information, impact metrics, and dissemination.
- Tracks research outputs, citations, impact, and compliance with publishing requirements and policies.
- Compliance and Regulatory Management:
- Ensures compliance with research ethics, regulations, standards, policies, and reporting requirements.
- Manages regulatory approvals, certifications, audits, and documentation.
- Reporting and Analytics:
- Generates reports, dashboards, and analytics to monitor, evaluate, and assess research activities, outcomes, and impact.
- Facilitates data-driven decision-making, strategic planning, and performance assessment.
Key Features of RMIS:
- User Access and Security: Provides secure access controls, user roles, and permissions to safeguard sensitive data and ensure compliance with privacy regulations.
- Data Integration and Interoperability: Interoperable with other systems, platforms, and databases to facilitate seamless data exchange, integration, and interoperability.
- Scalability and Flexibility: Scalable and adaptable to accommodate growth, changes, and evolving needs of research activities, projects, and disciplines.
- User-Friendly Interface: User-friendly interface with intuitive navigation, search functionality, and customizable features to enhance user experience and satisfaction.
Benefits of RMIS:
- Enhanced Research Efficiency: Streamlines research activities, project management, grants and funding management, compliance, and reporting to enhance research efficiency and productivity.
- Data-Driven Insights: Enables data-driven insights, analytics, and reporting to monitor, evaluate, and assess research performance, outcomes, and impact.
- Collaborative Research: Facilitates collaboration, networking, and knowledge sharing among researchers, teams, and institutions to foster innovation and excellence in research.
- Compliance and Governance: Ensures compliance with research ethics, regulations, standards, and governance policies to uphold integrity, transparency, and accountability in research practices.
In summary, A Research Management Information System (RMIS) is a comprehensive solution that plays a vital role in supporting and enhancing research management, collaboration, compliance, and reporting within academic, government, and private research institutions. By integrating various components, features, and functionalities, RMIS empowers researchers, administrators, and stakeholders to streamline research processes, improve collaboration, generate insights, and contribute to advancements in knowledge, innovation, and excellence in research across various disciplines and fields. As research continues to evolve, RMIS will continue to play a crucial role in transforming research practices, fostering collaboration, and driving advancements in science, technology, and academia.
Learning Management Systems (LMS)
A Learning Management System (LMS) is a software application or platform designed to facilitate and manage the administration, documentation, tracking, reporting, and delivery of educational courses, training programs, learning content, and resources within educational institutions, organizations, corporations, and businesses. LMS provides educators, instructors, trainers, administrators, learners, and stakeholders with a centralized and integrated platform to create, deliver, manage, and assess learning experiences, activities, and outcomes in a flexible, scalable, and interactive environment.
Components of Learning Management Systems (LMS):
-
Course Management:
- Course Creation: Enables educators and instructors to create, design, develop, and organize courses, modules, lessons, and learning content.
- Content Repository: Provides a centralized repository to store, manage, and share educational materials, resources, documents, videos, and multimedia content.
-
Learner Management:
- User Profiles: Manages learner profiles, registrations, enrollments, progress, achievements, and performance.
- Progress Tracking: Tracks and monitors learner progress, completion, participation, and engagement in courses, activities, and assessments.
-
Assessment and Evaluation:
- Quizzes and Exams: Enables creation, delivery, and grading of quizzes, exams, assignments, and assessments.
- Feedback and Reporting: Generates reports, analytics, and feedback on learner performance, outcomes, strengths, weaknesses, and areas for improvement.
-
Communication and Collaboration:
- Discussion Forums: Facilitates discussion forums, chat rooms, and messaging for communication, collaboration, and interaction among learners, educators, and peers.
- Notifications and Announcements: Sends notifications, reminders, updates, and announcements regarding courses, activities, events, and deadlines.
-
Integration and Customization:
- Integration with Tools: Integrates with external tools, platforms, and services for content creation, collaboration, communication, assessment, and analytics.
- Customization and Personalization: Allows customization, branding, and personalization of the LMS interface, features, and functionalities to meet organizational and user needs.
Advantages of Learning Management Systems (LMS):
-
Accessibility and Flexibility:
- Anytime, Anywhere Learning: Enables anytime, anywhere access to educational courses, content, resources, and activities for learners to study and learn at their own pace, place, and convenience.
-
Efficiency and Scalability:
- Streamlined Operations: Enhances efficiency, productivity, and management of educational courses, content, learners, and resources through automation and integration.
- Scalability and Growth: Scales and expands to accommodate increasing numbers of courses, learners, educators, and organizations.
-
Engagement and Interaction:
- Interactive Learning: Promotes interactive, engaging, and collaborative learning experiences, activities, and environments through multimedia, simulations, and gamification.
- Communication and Collaboration: Facilitates communication, collaboration, and interaction among learners, educators, and peers to foster community, teamwork, and networking.
-
Assessment and Analytics:
- Performance Tracking: Enables tracking, monitoring, and assessment of learner performance, progress, achievements, and outcomes.
- Analytics and Insights: Provides analytics, insights, and reports on learner engagement, participation, satisfaction, and success to inform and improve teaching, learning, and outcomes.
-
Compliance and Reporting:
- Compliance Management: Ensures compliance with educational standards, regulations, policies, and requirements through tracking, documentation, and reporting.
- Reporting and Accountability: Generates comprehensive reports, analytics, and documentation for accountability, transparency, and decision-making.
Challenges of Learning Management Systems (LMS):
-
Usability and User Experience: Involves usability issues, learning curves, and user experience challenges requiring intuitive interfaces, training, and support for users.
-
Integration and Compatibility: Encounters challenges with integration, alignment, and compatibility with existing systems, technologies, platforms, and databases within organizations.
-
Content Creation and Management: Faces issues with content creation, development, quality, relevance, currency, and management requiring resources, expertise, and updates.
-
Security and Privacy: Concerns with data security, privacy, protection, and compliance with data management, privacy, and security policies, regulations, and standards.
In summary, Learning Management System (LMS) is a pivotal platform and tool for facilitating, managing, and enhancing educational and training experiences, activities, and outcomes within educational institutions, organizations, corporations, and businesses. LMS empowers educators, instructors, trainers, learners, administrators, and stakeholders with the capabilities, tools, and resources to create, deliver, manage, assess, and optimize learning in a flexible, interactive, scalable, and personalized environment. By embracing and adopting LMS, organizations and institutions can leverage technology, innovation, and collaboration to enhance teaching, learning, engagement, efficiency, effectiveness, accountability, and success in achieving educational and training goals, objectives, and outcomes in the dynamic and evolving landscape of education, training, and lifelong learning.
Virtual Classroom Software
Virtual Classroom Software is a specialized online learning platform and tool designed to facilitate and support the delivery, management, and interaction of educational courses, training programs, and learning experiences in a virtual and interactive environment. Virtual Classroom Software enables educators, instructors, trainers, and learners to connect, communicate, collaborate, and engage in real-time through various multimedia tools, features, and functionalities, such as video conferencing, chat, whiteboards, polls, quizzes, and interactive content, to create, deliver, manage, and optimize online learning and teaching experiences.
Key Features of Virtual Classroom Software:
-
Video Conferencing:
- Live Video Sessions: Enables live video sessions and lectures with high-quality video and audio to facilitate real-time interaction, communication, and engagement among educators and learners.
-
Interactive Whiteboard:
- Digital Whiteboard: Provides a digital whiteboard for educators and learners to create, annotate, share, and collaborate on content, diagrams, notes, and illustrations during live sessions and lectures.
-
Chat and Messaging:
- Real-Time Chat: Facilitates real-time chat, messaging, and communication among educators, learners, and participants during live sessions and lectures.
-
Screen Sharing and Recording:
- Screen Sharing: Allows screen sharing and presentation of content, documents, slides, and multimedia during live sessions and lectures.
- Session Recording: Enables recording and playback of live sessions and lectures for review, revision, and accessibility by learners.
-
Polls, Quizzes, and Assessments:
- Interactive Polls: Conducts interactive polls, surveys, and feedback to engage learners and gather insights, opinions, and responses.
- Online Quizzes: Offers online quizzes, assessments, and evaluations to test, measure, and assess learner knowledge, understanding, and performance.
-
Content Sharing and Collaboration:
- Content Sharing: Allows sharing, uploading, and accessing of educational materials, resources, documents, videos, and multimedia for teaching, learning, and collaboration.
- Group Collaboration: Supports group collaboration, teamwork, and interaction among learners through breakout rooms, group activities, and projects.
Examples of Virtual Classroom Software:
-
Zoom:
- Features: Video conferencing, chat, whiteboard, screen sharing, recording, polls, quizzes, breakout rooms, and integration with learning management systems.
- Use Cases: Online education, virtual classrooms, webinars, meetings, training sessions, and collaborative projects.
-
Microsoft Teams:
- Features: Video conferencing, chat, whiteboard, screen sharing, document sharing, collaboration tools, and integration with Office 365.
- Use Cases: Online learning, virtual classrooms, team collaboration, meetings, webinars, and project management.
-
Google Meet:
- Features: Video conferencing, chat, screen sharing, recording, captions, and integration with Google Workspace.
- Use Cases: Online education, virtual classrooms, meetings, webinars, presentations, and collaborative work.
-
Adobe Connect:
- Features: Virtual classrooms, video conferencing, chat, whiteboard, interactive content, breakout rooms, and analytics.
- Use Cases: Online learning, webinars, training sessions, virtual classrooms, meetings, and events.
-
Blackboard Collaborate:
- Features: Virtual classrooms, video conferencing, chat, whiteboard, content sharing, breakout rooms, and integration with Blackboard LMS.
- Use Cases: Online education, virtual classrooms, webinars, training sessions, and collaborative learning.
-
6. BigBlueButton:
- Features: ..
- Use Cases: .
In summary, Virtual Classroom Software is a versatile and essential tool for facilitating, managing, and enhancing online learning, teaching, collaboration, and engagement in today's digital and remote learning landscape. Virtual Classroom Software enables educators, instructors, trainers, and learners to connect, communicate, collaborate, and interact in real-time through various multimedia tools, features, and functionalities to create, deliver, manage, and optimize online learning and teaching experiences. By leveraging Virtual Classroom Software, organizations, educational institutions, and businesses can adapt, innovate, and transform traditional learning and training models into interactive, engaging, flexible, and accessible online learning experiences that foster knowledge, skills, collaboration, and success in the dynamic and evolving world of education, training, and lifelong learning.
Research Information System (RIS)
A Research Information System (RIS) is a specialized software solution and platform designed to manage, organize, integrate, share, and disseminate research-related information, data, publications, projects, activities, and outputs within research institutions, organizations, universities, and funding agencies. RIS facilitates the tracking, monitoring, evaluation, and reporting of research activities, performance, impact, and outcomes to enhance transparency, accountability, collaboration, and decision-making among researchers, administrators, managers, stakeholders, and funders in the research ecosystem.
Components of Research Information System (RIS):
-
Researcher Profiles and Portfolios:
- Researcher Information: Manages and maintains researcher profiles, biographies, affiliations, expertise, publications, projects, and contributions.
- Collaboration and Networking: Facilitates connectivity, collaboration, and networking among researchers, teams, departments, institutions, and stakeholders.
-
Publications and Outputs Management:
- Publication Database: Catalogs, indexes, and archives research publications, articles, papers, theses, dissertations, and conference proceedings.
- Open Access Repository: Provides access to open access publications, datasets, and research outputs for wider dissemination and visibility.
-
Research Projects and Grants Tracking:
- Projects and Funding: Tracks and monitors research projects, grants, funding, budgets, timelines, deliverables, and compliance.
- Reporting and Analytics: Generates reports, dashboards, and analytics to monitor, evaluate, and analyze research performance, impact, outcomes, and trends.
-
Research Data Management (RDM):
- Data Management: Manages and preserves research data, datasets, code, software, documentation, and metadata.
- Data Sharing and Collaboration: Facilitates data sharing, collaboration, compliance, and security of research data and information.
-
Collaboration and Communication Tools:
- Collaborative Tools: Integrates with collaboration, communication, and project management tools and platforms to support teamwork, projects, and activities.
- Messaging and Notifications: Sends alerts, notifications, and updates regarding research activities, projects, publications, and events.
Advantages of Research Information System (RIS):
- Efficient Research Management: Enhances efficiency, productivity, and management of research activities, projects, data, publications, and outputs.
- Transparency and Accountability: Provides visibility, tracking, and monitoring of research processes, performance, impact, and outcomes for transparency and accountability.
- Collaboration and Networking: Facilitates connectivity, collaboration, and networking among researchers, teams, departments, and institutions to foster innovation and interdisciplinary research.
- Compliance and Governance:Compliance and Governance: Ensures compliance with research policies, regulations, standards, and governance for integrity, ethics, and responsible conduct of research.
- Visibility and Impact: Research Visibility and Impact: Increases visibility, recognition, and impact of research, publications, and contributions within the research community, disciplines, and fields.
Challenges of Research Information System (RIS):
- Integration and Compatibility: Encounters challenges with integration, alignment, and compatibility with existing systems, technologies, and databases within the organization.
- Data Quality and Integrity: Faces issues with data quality, accuracy, consistency, completeness, and integrity requiring proper management, validation, and maintenance of data and information.
- Security and Privacy: Concerns with data security, privacy, protection, and compliance with data management, privacy, and security policies, regulations, and standards.
- Usability and User Experience: Involves usability issues, learning curves, and user experience challenges requiring intuitive interfaces, training, and support for users.
In summary, Research Information System (RIS) is a pivotal tool and platform for managing, organizing, integrating, sharing, and disseminating research-related information, data, publications, projects, and outputs within the research ecosystem. RIS empowers researchers, administrators, managers, stakeholders, and funders with the capabilities, tools, and platforms to enhance efficiency, transparency, collaboration, decision-making, compliance, visibility, and impact in the dynamic and interconnected world of research and academia. By embracing and adopting RIS, organizations and institutions can optimize research management, governance, integrity, ethics, collaboration, communication, and success in advancing knowledge, innovation, and solutions to address global challenges and opportunities in research, science, technology, education, and interdisciplinary fields.
Current Research Information System (CRIS)
Current Research Information System (CRIS) is a specialized information management system and platform designed to support and manage the collection, organization, integration, sharing, and dissemination of research-related information, data, publications, projects, activities, and outputs within research institutions, organizations, universities, and funding agencies. CRIS facilitates the tracking, monitoring, evaluation, and reporting of research activities, performance, impact, and outcomes to enhance transparency, accountability, collaboration, and decision-making among researchers, administrators, managers, stakeholders, and funders in the research ecosystem.
Components of Current Research Information System (CRIS):
-
Research Information Management (RIM):
- Profiles and Portfolios: Manages and maintains researcher profiles, portfolios, expertise, affiliations, publications, and contributions.
- Projects and Grants: Tracks and monitors research projects, grants, funding, budgets, timelines, and deliverables.
-
Publications and Outputs Repository:
- Publication Database: Catalogs, indexes, and archives research publications, articles, papers, theses, dissertations, and conference proceedings.
- Open Access Repository: Provides access to open access publications, datasets, and research outputs for wider dissemination and visibility.
-
Research Data Management (RDM):
- Data Catalog and Repository: Manages and preserves research data, datasets, code, software, and documentation.
- Data Sharing and Collaboration: Facilitates data sharing, collaboration, and compliance with data management, privacy, and security policies and regulations.
-
Collaboration and Networking:
- Research Networking and Collaboration: Connects researchers, teams, departments, institutions, and stakeholders to foster collaboration, communication, and networking.
- Collaborative Tools and Platforms: Integrates with collaboration tools, platforms, and services to support teamwork, projects, and activities.
-
Reporting and Analytics:
- Performance Monitoring and Analytics: Generates reports, dashboards, and analytics to monitor, evaluate, and analyze research performance, impact, outcomes, and trends.
- Compliance and Reporting: Ensures compliance with research policies, regulations, standards, and reporting requirements for transparency and accountability.
Advantages of Current Research Information System (CRIS):
- Efficient Research Management: Enhances efficiency, productivity, and management of research activities, projects, data, publications, and outputs.
- Transparency and Accountability: Provides visibility, tracking, and monitoring of research processes, performance, impact, and outcomes for transparency and accountability.
- Collaboration and Networking: Facilitates connectivity, collaboration, and networking among researchers, teams, departments, and institutions to foster innovation and interdisciplinary research.
- Compliance and Governance: Ensures compliance with research policies, regulations, standards, and governance for integrity, ethics, and responsible conduct of research.
- Visibility and Impact: Increases visibility, recognition, and impact of research, publications, and contributions within the research community, disciplines, and fields.
Challenges of Current Research Information System (CRIS):
- Integration and Compatibility: Encounters challenges with integration, alignment, and compatibility with existing systems, technologies, and databases within the organization.
- Data Quality and Integrity: Faces issues with data quality, accuracy, consistency, completeness, and integrity requiring proper management, validation, and maintenance of data and information.
- Security and Privacy: Concerns with data security, privacy, protection, and compliance with data management, privacy, and security policies, regulations, and standards.
- Usability and User Experience: Involves usability issues, learning curves, and user experience challenges requiring intuitive interfaces, training, and support for users.
In summary, Current Research Information System (CRIS) plays a vital role in supporting and managing research-related information, activities, projects, publications, and outputs within research institutions, organizations, universities, and funding agencies. CRIS empowers researchers, administrators, managers, stakeholders, and funders with the capabilities, tools, and platforms to enhance efficiency, transparency, collaboration, decision-making, compliance, visibility, and impact in the dynamic and interconnected world of research and academia. By embracing and adopting CRIS, organizations and institutions can optimize research management, governance, integrity, ethics, collaboration, communication, and success in advancing knowledge, innovation, and solutions to address global challenges and opportunities in research, science, technology, education, and interdisciplinary fields.
Research Networking Tools
Research Networking Tools are specialized platforms, software, and technologies designed to support and enhance collaboration, communication, networking, and sharing of resources, expertise, knowledge, and information among researchers, scientists, scholars, academicians, professionals, and stakeholders within the research community. These tools facilitate the discovery, connection, collaboration, and engagement of researchers with peers, experts, institutions, organizations, and communities to foster innovation, creativity, learning, and advancement in research, science, technology, education, and interdisciplinary fields.
Types of Research Networking Tools
- Academic and Research Platforms:
- ResearchGate: A professional network for researchers to share, discover, and discuss research papers, publications, projects, and ideas.
- Academia.edu: An academic platform for researchers to share papers, monitor research impact, and follow research topics and authors.
- Mendeley: A reference manager, academic collaboration network, and research database to organize, annotate, share, and discover research papers and publications.
- Collaboration and Communication Tools:
- Slack: A collaboration hub and messaging platform for teams, projects, and communities to communicate, share, and collaborate in real-time.
- Microsoft Teams: A collaboration and communication platform integrated with Office 365 to facilitate teamwork, meetings, chats, and file sharing.
- Networking and Discovery Platforms:
- LinkedIn: A professional networking platform for researchers, professionals, and organizations to connect, network, share, and discover opportunities, insights, and expertise.
- Google Scholar: A freely accessible web search engine that indexes scholarly articles, theses, books, conference papers, and patents to facilitate research discovery and access.
- Data Sharing and Repository Platforms:
- figshare: A data sharing and repository platform for researchers to upload, share, and discover research data, datasets, figures, and media.
- Zenodo: A research data repository and platform to upload, preserve, and share research outputs, datasets, software, and publications.
- Conference and Event Platforms:
- Eventbrite: An event management and ticketing platform for organizing, promoting, and attending research conferences, workshops, seminars, and events.
- Zoom: A video conferencing and webinar platform for hosting virtual meetings, presentations, and events with remote participants and attendees.
Advantages of Research Networking Tools:
- Collaboration and Networking: Facilitates connectivity, collaboration, and networking among researchers, peers, experts, and communities to foster innovation, learning, and advancement.
- Knowledge Sharing and Discovery: Enables access to research papers, publications, datasets, and insights to support learning, discovery, and research development.
- Communication and Engagement: Enhances communication, engagement, and interaction among researchers, teams, and communities to share, discuss, and collaborate on research topics, projects, and ideas.
- Visibility and Impact: Increases visibility, recognition, and impact of research, publications, and contributions within the research community, disciplines, and fields.
- Productivity and Efficiency: Improves productivity, efficiency, and organization of research activities, tasks, and workflows through collaboration, communication, and management tools.
In summary, Research Networking Tools play a pivotal role in fostering collaboration, communication, networking, and sharing of resources, expertise, knowledge, and information within the research community. By leveraging these tools, researchers, scientists, scholars, academicians, professionals, and stakeholders can connect, collaborate, discover, share, and advance research, science, technology, education, and interdisciplinary fields. Research Networking Tools empower users with the capabilities, opportunities, and platforms to foster innovation, creativity, learning, growth, and success in the dynamic and interconnected world of research and academia.
Conclusion
Research Information System (RIS), Current Research Information System (CRIS), and Research Networking Tools are all designed to support and enhance research activities, collaboration, and management within academic and research institutions. While they share similarities, each has distinct features, functionalities, and focuses that cater to different aspects of research management, data integration, and collaboration. Let's explore the differences and similarities between these systems and tools:
Research Information System (RIS):
Definition: A Research Information System (RIS) is a comprehensive system designed to manage and support research activities, projects, grants, publications, and collaborations within academic and research institutions.
Key Features:
- Research Management: Manages research projects, grants, funding, timelines, milestones, and deliverables.
- Publications Management: Manages research publications, citations, bibliographic information, and impact metrics.
- Data Management: Manages research data, datasets, metadata, and documentation.
- Reporting and Analytics: Generates reports, dashboards, and analytics to monitor, evaluate, and assess research activities and outcomes.
Focus: Comprehensive research management, data management, and reporting across various disciplines and research areas.
Current Research Information System (CRIS):
Definition: A Current Research Information System (CRIS) is a specialized system designed to capture, manage, and showcase current research activities, outputs, and impact within academic and research institutions.
Key Features:
- Current Research Outputs: Focuses on capturing and managing current research activities, projects, publications, and impact.
- Integration with External Systems: Interoperable with external databases, repositories, and platforms to facilitate data exchange and integration.
- Compliance and Reporting: Ensures compliance with research regulations, standards, and reporting requirements.
Focus: Capturing and showcasing current research activities, outputs, and impact to internal and external stakeholders.
Research Networking Tools:
Definition: Research Networking Tools are specialized tools designed to facilitate collaboration, networking, and knowledge sharing among researchers, teams, and institutions.
Key Features:
- Collaboration and Networking: Facilitates collaboration, communication, and networking among researchers, teams, and institutions.
- Profile Management: Manages researcher profiles, expertise, publications, projects, and collaborations.
- Search and Discovery: Enables search, discovery, and identification of researchers, projects, publications, and expertise.
- Integration with CRIS and RIS: Integrates with Current Research Information Systems (CRIS) and Research Information Systems (RIS) to enhance collaboration, data sharing, and visibility.
Focus: Enhancing collaboration, networking, and knowledge sharing among researchers, teams, and institutions.
Comparison:
-
RIS: Comprehensive research management and data management across various disciplines.
-
CRIS: Specialized in capturing and showcasing current research activities, outputs, and impact.
-
Research Networking Tools: Specialized in facilitating collaboration, networking, and knowledge sharing among researchers and institutions.
In summary, While Research Information Systems (RIS) and Current Research Information Systems (CRIS) focus on research management, data management, and showcasing research outputs, Research Networking Tools specialize in enhancing collaboration, networking, and knowledge sharing among researchers, teams, and institutions. Each system and tool plays a unique and complementary role in supporting and enhancing research activities, collaboration, and management within academic and research institutions. By integrating these systems and tools, institutions can create a holistic and collaborative research environment that fosters innovation, excellence, and impact across various disciplines and research areas.
Electronic Government
Electronic Government, often referred to as e-Government, is the use of digital technologies and the internet to provide public services, improve administrative efficiency, and enhance the interaction between government and citizens. It aims to make government operations more accessible, transparent, and effective. Here are key components and benefits of e-Government:
Key Components of e-Government:
Government-to-Citizen (G2C):
Online Services: Provision of services like tax filing, license renewals, and social security applications through online portals.
Information Dissemination: Access to government information, policies, and announcements via government websites and social media.
Government-to-Business (G2B):
E-Procurement: Online tendering and procurement processes to streamline business interactions with the government.
Regulatory Compliance: Simplified compliance processes for businesses, including permits, licenses, and reporting.
Government-to-Government (G2G):
Inter-agency Collaboration: Sharing data and resources among different government departments and agencies to improve coordination and efficiency.
Unified Systems: Integrated systems for various functions like law enforcement, health services, and emergency response.
Government-to-Employee (G2E):
Human Resource Management: Digital systems for managing government employees, including payroll, training, and performance evaluations.
Intranet Services: Internal communication and collaboration tools for government employees.
Benefits of e-Government:
Improved Service Delivery:
Convenience: Citizens can access services online at any time, reducing the need for physical visits to government offices.
Speed: Faster processing of applications and services due to automated workflows.
Increased Transparency:
Access to Information: Citizens have easier access to government information, enhancing accountability and trust.
Public Participation: Platforms for public feedback and engagement in decision-making processes.
Cost Efficiency:
Operational Savings: Reduction in paper-based processes and manual labor.
Resource Optimization: Efficient allocation and utilization of government resources through data-driven decision-making.
Enhanced Citizen Engagement:
Communication Channels: Multiple channels for citizens to interact with the government, including websites, mobile apps, and social media.
Participatory Governance: Tools for online surveys, polls, and consultations to involve citizens in governance.
Better Data Management:
Data Integration: Centralized databases and interoperable systems for seamless data sharing across government entities.
Analytics and Insights: Use of big data and analytics to gain insights into public needs and policy impacts.
Security and Privacy:
Secure Transactions: Implementation of robust cybersecurity measures to protect sensitive data and ensure secure online transactions.
Privacy Policies: Policies and regulations to safeguard the privacy of citizens' data.
Examples of e-Government Initiatives:
Digital India: An initiative by the Government of India to transform India into a digitally empowered society and knowledge economy by providing government services online, promoting digital literacy, and building infrastructure for digital connectivity.
Gov.uk: The United Kingdom's centralized digital platform for accessing government services and information, simplifying interactions between citizens and the government.
e-Estonia: Estonia's advanced digital society framework that offers a wide range of e-services, including e-residency, digital identity, and online voting, making government services highly accessible and efficient.
USA.gov: The U.S. government's official web portal that provides a gateway to government services and information for citizens, businesses, and government employees.
Challenges and Considerations:
Digital Divide: Ensuring that all citizens, including those in remote or underserved areas, have access to the internet and digital skills.
Cybersecurity: Protecting government systems and data from cyber threats and ensuring secure online interactions.
Interoperability: Ensuring that different government systems and databases can communicate and share data effectively.
Privacy Concerns: Balancing the benefits of data sharing with the need to protect citizens' privacy and comply with data protection regulations.
Change Management: Managing the transition from traditional processes to digital systems and ensuring that government employees and citizens are adequately trained.
e-Government represents a significant shift towards more efficient, transparent, and citizen-centric governance, leveraging technology to enhance public administration and service delivery.
E-government involves the use of information and communication technologies (ICT) to deliver government services, facilitate communication with citizens, and enhance government operations. Implementing e-government solutions presents several key issues, which can be categorized into security, technical, social, and administrative challenges. Here are some of the main key issues:
Security Issues
- Data Privacy and Confidentiality: Protecting personal and sensitive information of citizens from unauthorized access and breaches.
- Authentication and Identity Management: Ensuring that only authorized users can access specific services, typically through robust identity verification processes.
- Data Integrity: Ensuring that data remains accurate and unaltered during storage and transmission.
- Access Control: Implementing policies to ensure only authorized personnel have access to certain data or systems.
- Cyber Threats and Attacks: Defending against hacking, malware, denial-of-service attacks, and other cyber threats.
- System Availability and Reliability: Ensuring e-government services are available and reliable, minimizing downtime.
- Data Encryption: Using encryption to protect data both in transit and at rest from interception and unauthorized access.
- Audit and Compliance: Ensuring compliance with relevant laws, regulations, and standards, and maintaining logs for auditing purposes.
- Disaster Recovery and Business Continuity: Planning for and mitigating the impact of disasters to ensure continued service availability.
- User Awareness and Training: Educating users about security best practices and risks to prevent social engineering attacks.
Technical Issues
- Interoperability: Ensuring that different government systems and platforms can communicate and work together seamlessly.
- Scalability: Designing systems that can handle increasing numbers of users and data without performance degradation.
- System Integration: Integrating legacy systems with new technologies and platforms.
- Technical Infrastructure: Establishing and maintaining the necessary hardware, software, and network infrastructure to support e-government services.
- Performance Optimization: Ensuring systems are efficient and responsive to user needs.
Social Issues
- Digital Divide: Addressing inequalities in access to technology and the internet among different segments of the population.
- Public Awareness and Adoption: Educating citizens about available e-government services and encouraging their use.
- Trust and Confidence: Building trust in e-government services by ensuring security, reliability, and transparency.
Administrative Issues
- Policy and Regulation: Developing and enforcing policies and regulations that support e-government initiatives and ensure data privacy and security.
- Change Management: Managing the transition from traditional to digital services, including training staff and modifying existing processes.
- Resource Allocation: Ensuring adequate funding and resources for the development and maintenance of e-government services.
- Stakeholder Engagement: Involving all relevant stakeholders, including citizens, businesses, and government agencies, in the development and implementation of e-government services.
Legal Issues
- Legal Framework: Establishing a legal framework that supports digital transactions, electronic signatures, and data protection.
- Compliance with International Standards: Ensuring that e-government systems comply with international standards and regulations, especially for cross-border services and data exchanges.
Ethical Issues
- Privacy Concerns: Ensuring that citizens' privacy is respected and protected in all e-government interactions.
- Transparency and Accountability: Ensuring that government actions and processes are transparent and that officials are held accountable for their actions.
Addressing these key issues is crucial for the successful implementation and sustainability of e-government initiatives, ensuring they are secure, efficient, and accessible to all citizens.
E-government security issues are crucial for the integrity, confidentiality, and availability of services provided to citizens and businesses. Common key security issues in e-government typically include:
- Data Privacy and Confidentiality: Protecting sensitive citizen data from unauthorized access.
- Authentication and Identity Management: Ensuring that only authorized users can access certain services.
- Data Integrity: Ensuring that data is accurate and has not been tampered with.
- Access Control: Managing permissions to ensure only authorized personnel can access certain data or services.
- Cyber Threats and Attacks: Protecting against cyber threats such as hacking, malware, and denial-of-service attacks.
- System Availability and Reliability: Ensuring that e-government services are available to users whenever needed and that downtime is minimized.
- Data Encryption: Protecting data in transit and at rest to prevent interception and unauthorized access.
- Audit and Compliance: Ensuring systems are compliant with relevant laws and regulations, and maintaining logs for auditing purposes.
- Disaster Recovery and Business Continuity: Planning for and mitigating the impact of disasters to ensure continued service availability.
- User Awareness and Training: Educating users about security best practices and risks.
Given this context, here are some topics that are not typically considered key e-government security issues:
Non-Key E-Government Security Issues
- User Interface Design: While important for usability, UI design is not directly a security issue.
- Service Personalization: Customizing e-government services to user preferences is a usability feature, not a core security issue.
- Interoperability of Services: Ensuring different systems and services work together seamlessly is a technical and functional issue, not a direct security concern.
- Performance Optimization: While performance is crucial for user satisfaction, it is not inherently a security issue.
- Mobile App Development: The development of mobile applications involves security, but the process itself is not a security issue.
- Public Relations and Outreach: Communicating and marketing e-government services are important for adoption but are not security issues.
- Citizen Engagement and Feedback: Encouraging citizen participation and collecting feedback are essential for service improvement but not security concerns.
- Service Expansion: Adding new services to an e-government platform is a growth strategy, not directly related to security.
- Localization and Language Support: Providing services in multiple languages is about accessibility and inclusivity, not security.
- User Experience (UX) Enhancements: Improving the overall user experience is important but not directly related to security.
While these non-key issues are important for the overall success and functionality of e-government services, they do not directly address the security challenges that protect the integrity, confidentiality, and availability of the system.
When discussing e-government security, it's crucial to identify the key issues that can affect the integrity, availability, and confidentiality of government services and data. Here are some common e-government security issues, along with some that are not typically considered key issues:
Key E-Government Security Issues
-
Data Privacy and Protection:
- Ensuring the confidentiality and integrity of citizen data.
- Compliance with regulations such as GDPR, CCPA, etc.
-
Identity and Access Management (IAM):
- Implementing robust authentication and authorization mechanisms.
- Preventing unauthorized access and ensuring that only legitimate users can access services.
-
Cybersecurity Threats:
- Protection against malware, ransomware, phishing, and other cyber-attacks.
- Implementing intrusion detection/prevention systems and firewalls.
-
Secure Communication Channels:
- Ensuring data is encrypted in transit using protocols like HTTPS, TLS.
- Protecting communications between users and government services.
-
System Vulnerability Management:
- Regularly updating and patching systems to fix known vulnerabilities.
- Conducting security audits and vulnerability assessments.
-
Incident Response and Recovery:
- Having a well-defined incident response plan.
- Ensuring data backup and disaster recovery procedures are in place.
-
User Education and Awareness:
- Educating citizens and government employees about cybersecurity best practices.
- Training on recognizing phishing attempts and other scams.
-
Regulatory Compliance:
- Adhering to national and international laws and standards related to data protection and cybersecurity.
-
Infrastructure Security:
- Securing physical and virtual infrastructure, including servers, databases, and network components.
-
Authentication and Authorization:
- Using multi-factor authentication (MFA) and strong password policies.
Issues That Are Not Typically Key E-Government Security Issues
-
General Internet Browsing Security:
- While important, the security of general internet browsing (like personal use of social media) is not a primary focus of e-government security.
-
Consumer Electronics Security:
- Security concerns related to personal devices like smartphones or laptops, unless specifically used for government services.
-
Non-Critical IT Services:
- Issues related to non-essential or non-critical IT services that do not impact government operations or citizen services.
-
Personal Data Leakage from Non-Governmental Sources:
- While relevant, personal data breaches from non-governmental sources, unless directly affecting government-held data, are not core issues.
-
Non-Cyber Threats:
- Physical threats like natural disasters or terrorism not related to digital infrastructure are generally managed separately from cybersecurity concerns.
-
Non-Compliance with Industry Standards Not Applicable to E-Government:
- Standards and practices that are not relevant to public sector data and services, such as certain consumer-facing software standards.
Conclusion
In summary, while e-government security is multifaceted, the focus is on issues directly impacting the integrity, availability, and confidentiality of government services and data. Issues like data privacy, IAM, cybersecurity threats, secure communications, and regulatory compliance are central. Conversely, general IT security concerns not directly impacting government services are typically outside the scope of key e-government security issues.
Business marketing with Information Technology (IT) involves leveraging digital tools and platforms to promote products or services, engage with customers, and analyze market trends. IT has revolutionized the field of marketing, enabling businesses to reach wider audiences, personalize marketing efforts, and measure the effectiveness of their campaigns more accurately. Here are key aspects of business marketing with IT:
IT Marketing
Key Components of Business Marketing with IT:
-
Digital Marketing Channels:
- Websites: A well-designed, SEO-optimized website serves as the digital storefront for businesses.
- Social Media: Platforms like Facebook, Instagram, LinkedIn, and Twitter are used for brand building, customer engagement, and targeted advertising.
- Email Marketing: Personalized email campaigns to nurture leads and maintain customer relationships.
- Content Marketing: Creating valuable content (blogs, videos, infographics) to attract and engage a target audience.
- Pay-Per-Click (PPC) Advertising: Paid advertising on search engines and social media to drive traffic and generate leads.
-
Customer Relationship Management (CRM):
- CRM Systems: Tools like Salesforce, HubSpot, and Zoho CRM help manage customer interactions, track sales, and analyze customer data.
- Personalization: Using CRM data to personalize marketing messages and offers to individual customers based on their preferences and behaviors.
-
Analytics and Data-Driven Marketing:
- Web Analytics: Tools like Google Analytics to track website traffic, user behavior, and conversion rates.
- Marketing Analytics: Analyzing data from various marketing channels to measure campaign performance and ROI.
- Predictive Analytics: Using data analysis to predict future market trends and customer behaviors.
-
Search Engine Optimization (SEO):
- On-Page SEO: Optimizing website content and structure to improve search engine rankings.
- Off-Page SEO: Building backlinks and improving online presence through social media and content marketing.
- Technical SEO: Ensuring the website is technically sound, with fast loading times, mobile-friendliness, and secure connections (HTTPS).
-
E-commerce Platforms:
- Online Stores: Platforms like Shopify, WooCommerce, and Magento for selling products online.
- Payment Gateways: Secure payment processing through gateways like PayPal, Stripe, and Square.
- Order Management: Tools for managing inventory, orders, and shipping.
-
Marketing Automation:
- Automation Tools: Platforms like Mailchimp, Marketo, and Pardot to automate repetitive marketing tasks such as email campaigns, social media posting, and lead nurturing.
- Workflow Automation: Creating automated workflows to streamline marketing processes and improve efficiency.
Benefits of Using IT in Business Marketing:
-
Enhanced Reach:
- IT enables businesses to reach a global audience through digital channels, breaking geographical barriers.
-
Cost-Effective Marketing:
- Digital marketing is often more cost-effective than traditional marketing methods, providing higher ROI.
-
Targeted Marketing:
- IT tools allow businesses to segment their audience and deliver personalized marketing messages, improving conversion rates.
-
Real-Time Data and Insights:
- Access to real-time data helps businesses make informed marketing decisions and quickly adapt to market changes.
-
Improved Customer Engagement:
- Interactive digital channels foster better customer engagement and build stronger relationships.
-
Scalability:
- IT solutions can scale with business growth, accommodating increasing marketing needs and customer interactions.
Examples of IT in Business Marketing:
-
HubSpot: A comprehensive inbound marketing platform that offers CRM, email marketing, content management, and analytics tools to help businesses attract, engage, and delight customers.
-
Google Analytics: A web analytics service that tracks and reports website traffic, helping businesses understand user behavior and optimize their online presence.
-
Mailchimp: An email marketing and automation platform that allows businesses to create, send, and analyze email campaigns, and manage subscriber lists.
-
Hootsuite: A social media management tool that enables businesses to schedule posts, track engagement, and analyze social media performance across multiple platforms.
-
Salesforce: A leading CRM platform that provides sales, customer service, marketing automation, and analytics solutions to help businesses manage customer relationships and drive growth.
Challenges and Considerations:
- Data Privacy and Security: Ensuring customer data is protected and compliant with regulations such as GDPR and CCPA.
- Keeping Up with Technology: Staying current with rapidly evolving digital marketing technologies and trends.
- Integration: Ensuring seamless integration of various IT tools and platforms to provide a unified view of marketing activities.
- Skill Development: Continuously upskilling marketing teams to effectively use IT tools and interpret data insights.
- Measuring ROI: Accurately measuring the return on investment of digital marketing activities and adjusting strategies accordingly.
By effectively leveraging IT, businesses can enhance their marketing efforts, reach wider audiences, and achieve better results in today's digital landscape.
Introduction to IT Marketing
IT marketing, or Information Technology marketing, is a specialized field that focuses on promoting products and services related to technology. In today's digital age, IT marketing plays a crucial role in helping businesses reach their target audience, increase brand awareness, and drive sales. This discipline encompasses a wide range of strategies and tactics tailored specifically to the unique challenges and opportunities within the technology sector.
Key Components of IT Marketing
1. Understanding the Audience
Successful IT marketing begins with a deep understanding of the target audience. This includes IT professionals, decision-makers in businesses, technology enthusiasts, and consumers interested in tech products. Marketers must identify their pain points, motivations, and preferences to tailor messages effectively.
2. Product Positioning and Differentiation
IT products and services often face stiff competition in the marketplace. Effective IT marketing involves clearly defining the unique value propositions of products and services. This may include superior performance, innovative features, cost-effectiveness, or specific industry certifications.
3. Digital Marketing Strategies
a. Search Engine Optimization (SEO): Optimizing websites and content to rank higher in search engine results pages (SERPs), thereby increasing organic traffic and visibility.
b. Pay-Per-Click (PPC) Advertising: Using platforms like Google Ads to bid on keywords relevant to IT products/services and paying only when users click on ads.
c. Content Marketing: Creating informative and engaging content such as blogs, whitepapers, case studies, and videos to attract and educate prospects.
d. Social Media Marketing: Leveraging platforms like LinkedIn, Twitter, and Facebook to engage with IT professionals, share industry insights, and promote offerings.
4. Relationship Building through CRM
Customer Relationship Management (CRM) systems play a vital role in IT marketing by managing interactions with current and potential customers. These systems track customer behavior, preferences, and communication history to personalize marketing efforts and improve customer retention.
5. Thought Leadership and Industry Influence
Establishing thought leadership involves positioning a company or its executives as authoritative voices within the IT industry. This can be achieved through speaking engagements, participation in industry events, publishing articles, and contributing to relevant forums and communities.
6. Data-Driven Decision Making
IT marketing relies heavily on analytics and data to measure campaign effectiveness, track ROI, and make informed decisions. Marketers use tools like Google Analytics, marketing automation platforms, and CRM systems to monitor performance metrics and optimize strategies.
Conclusion
In conclusion, IT marketing is a dynamic and rapidly evolving field that requires a blend of technical knowledge, creativity, and strategic thinking. By understanding the target audience, effectively communicating value propositions, leveraging digital channels, nurturing customer relationships, and embracing data-driven insights, IT marketers can drive growth and achieve competitive advantage in the technology sector.
Game in Education Management
Games in education management refer to the use of game-based learning and gamification techniques to enhance educational management processes, engage stakeholders, and improve learning outcomes. Integrating games into educational management can make administrative tasks more interactive, motivate stakeholders, and foster a collaborative and engaging learning environment. Here's how games can be applied in various aspects of education management:
1. Staff Training and Professional Development
- Simulation Games: Use simulation games to train school administrators, teachers, and staff in management, leadership, and decision-making skills.
- Scenario-Based Games: Develop scenario-based games that simulate real-world challenges and situations encountered in educational management.
- Role-Playing Games: Implement role-playing games to practice communication, teamwork, and problem-solving skills among staff.
2. Student Engagement and Motivation
- Educational Games: Integrate educational games into the curriculum to make learning more engaging, interactive, and enjoyable for students.
- Gamified Learning Platforms: Use gamified learning platforms that reward students with points, badges, and achievements to motivate participation and completion of tasks.
- Collaborative Games: Implement collaborative games that promote teamwork, communication, and critical thinking skills among students.
3. Parent and Community Engagement
- Gamified Communication Platforms: Use gamified communication platforms to engage parents and community members in school activities, events, and decision-making processes.
- Interactive Surveys and Feedback Games: Develop interactive surveys and feedback games to gather input, opinions, and suggestions from parents and community stakeholders.
- Community Challenges and Contests: Organize community challenges, contests, or events that promote collaboration, creativity, and community involvement in education management.
4. Data Management and Analytics
- Data Visualization Games: Use data visualization games to help educational managers and stakeholders understand and interpret complex data, trends, and patterns related to student performance, attendance, and behavior.
- Gamified Analytics Tools: Implement gamified analytics tools that reward users for analyzing and interpreting data, making informed decisions, and improving educational outcomes.
5. Leadership and Strategic Planning
- Strategic Planning Games: Use strategic planning games to facilitate discussions, brainstorming sessions, and collaborative decision-making among educational leaders, administrators, and stakeholders.
- Leadership Development Games: Implement leadership development games that focus on leadership skills, strategic thinking, and decision-making processes relevant to educational management.
Benefits of Using Games in Education Management
- Engagement: Games can increase engagement, motivation, and participation among stakeholders, leading to better outcomes.
- Collaboration: Games promote collaboration, teamwork, and communication skills among students, staff, parents, and community members.
- Skill Development: Games can help develop critical thinking, problem-solving, decision-making, and leadership skills necessary for effective educational management.
- Data-Driven Decision Making: Games and gamified tools can facilitate data-driven decision-making processes by making complex data more understandable and accessible.
In summary, Incorporating games into education management can transform traditional administrative tasks, enhance stakeholder engagement, and improve learning experiences for students. Whether it's staff training, student engagement, parent and community involvement, data management, or strategic planning, games offer innovative and interactive solutions that can make educational management more effective, collaborative, and engaging. By leveraging the power of games and gamification, educational institutions can create a dynamic and supportive environment that fosters growth, innovation, and success for all stakeholders involved in the education process.
Video games, gamification, and ludology are related concepts within the broader field of gaming, but they have distinct meanings and applications. Let's explore each term to understand their differences and relationships:
Gamification
Definition: Gamification is the application of game-design elements and game principles in non-game contexts to engage users, motivate actions, promote learning, and solve problems.
Gamification in management and organization refers to the application of game-design elements and principles in non-game contexts, such as business, management, and organizational settings. By incorporating elements like challenges, rewards, competition, and feedback, gamification aims to enhance engagement, motivation, productivity, collaboration, and performance among employees, teams, and stakeholders. Let's explore how gamification is applied in various aspects of management and organization:
1. Employee Engagement and Motivation
- Gamified Training and Onboarding: Utilizes gamified training modules, simulations, and quizzes to facilitate interactive and engaging onboarding experiences.
- Performance Recognition and Rewards: Implements gamified reward systems, leaderboards, badges, and points to recognize and reward employees for achievements, milestones, and performance.
- Goal Setting and Progress Tracking: Incorporates gamified goal-setting tools and progress trackers to motivate employees, monitor performance, and encourage goal attainment.
2. Learning and Development
- Gamified Learning Platforms: Utilizes gamified learning management systems (LMS) and platforms to enhance employee training, skill development, and knowledge acquisition.
- Interactive and Immersive Learning Experiences: Offers interactive and immersive learning experiences through gamified simulations, scenarios, and challenges to facilitate experiential learning and skill application.
- Collaborative Learning and Team Building: Promotes collaborative learning, teamwork, and communication among employees through gamified group activities, challenges, and competitions.
3. Productivity and Task Management
- Gamified Task Management Tools: Incorporates gamified task management tools and platforms to enhance productivity, organization, and time management.
- Achievement and Progress Tracking: Utilizes gamified achievement trackers, progress bars, and milestones to motivate employees, monitor task completion, and track progress towards goals.
- Team Collaboration and Communication: Facilitates team collaboration, communication, and coordination through gamified collaboration platforms, tools, and activities.
4. Customer Engagement and Loyalty
- Gamified Customer Experiences: Enhances customer engagement, satisfaction, and loyalty through gamified marketing campaigns, loyalty programs, and customer experiences.
- Reward and Incentive Programs: Implements gamified reward and incentive programs, contests, and promotions to incentivize customer participation, referrals, and loyalty.
- Feedback and Reviews: Encourages customer feedback, reviews, and participation through gamified feedback mechanisms, surveys, and interactive experiences.
5. Innovation and Problem Solving
- Gamified Innovation Challenges: Promotes innovation, creativity, and problem-solving among employees through gamified innovation challenges, brainstorming sessions, and ideation platforms.
- Collaborative Problem Solving: Facilitates collaborative problem-solving, teamwork, and communication among employees through gamified problem-solving activities, challenges, and competitions.
- Feedback and Iteration: Encourages feedback, iteration, and continuous improvement through gamified feedback mechanisms, voting systems, and review processes.
Benefits of Gamification in Management and Organization
- Enhanced Engagement and Motivation: Increases employee engagement, motivation, satisfaction, and retention by making work more enjoyable, challenging, and rewarding.
- Improved Performance and Productivity: Boosts performance, productivity, efficiency, and quality of work by incentivizing and rewarding desired behaviors, achievements, and outcomes.
- Enhanced Learning and Skill Development: Facilitates continuous learning, skill development, knowledge acquisition, and career growth through interactive, experiential, and immersive learning experiences.
- Foster Collaboration and Teamwork: Promotes collaboration, teamwork, communication, and coordination among employees, teams, and stakeholders through collaborative and competitive gamified activities.
- Enhanced Customer Engagement and Loyalty: Increases customer engagement, satisfaction, loyalty, and advocacy by creating interactive, personalized, and rewarding customer experiences.
Characteristics:
- Engagement: Uses game elements like points, badges, leaderboards, and challenges to engage and motivate users.
- Motivation: Encourages desired behaviors or actions through rewards, feedback, and incentives.
- Education and Training: Applied in education, training, marketing, health, fitness, productivity, and more.
- Sustainability: Aims to sustain engagement and participation over time through ongoing challenges and rewards.
In summary, Gamification in management and organization offers a powerful and innovative approach to enhancing engagement, motivation, productivity, collaboration, and performance among employees, teams, and stakeholders. By leveraging game-design elements and principles effectively, organizations can create engaging, rewarding, and interactive experiences that drive positive behaviors, outcomes, and results. As organizations continue to embrace digital transformation and seek innovative ways to enhance employee and customer experiences, gamification will continue to play a pivotal role in shaping the future of work, learning, collaboration, innovation, and customer engagement in the modern workplace.
Video Games
Definition: Video games are electronic games played on a device such as a console, computer, or mobile device that involves user interaction with a visual interface to generate visual feedback.
Video games have gained significant attention in the field of education as powerful tools for engaging students, promoting learning, fostering collaboration, and enhancing critical thinking skills. Educational video games, also known as "edutainment" games, are designed to combine entertainment and educational content to make learning more enjoyable, interactive, and effective. Let's explore how video games are being used in education and their impact on teaching and learning:
1. Enhanced Engagement and Motivation
- Interactive Learning Experiences: Video games offer interactive and immersive learning experiences that engage students in active learning, problem-solving, and exploration.
- Personalized Learning: Games can be customized to adapt to each student's learning pace, style, and preferences, providing personalized learning pathways and experiences.
- Immediate Feedback and Rewards: Games provide immediate feedback, rewards, and encouragement, motivating students to persevere, overcome challenges, and achieve goals.
2. Skill Development and Learning Outcomes
- Critical Thinking and Problem-Solving: Many educational games require students to use critical thinking, problem-solving, and decision-making skills to progress and succeed.
- Subject Mastery and Knowledge Retention: Games can help students master complex concepts, theories, and skills by presenting information in engaging and memorable ways.
- Collaboration and Communication: Multiplayer and collaborative games promote teamwork, communication, and collaboration among students, enhancing social and interpersonal skills.
3. Curriculum Integration and Subject Areas
- Math and Science Games: Math and science games can help students practice and apply mathematical concepts, scientific principles, and problem-solving skills in interactive and engaging ways.
- Language Arts and Literacy Games: Language arts and literacy games can help students develop reading, writing, vocabulary, and grammar skills through storytelling, puzzles, and interactive activities.
- History and Social Studies Games: History and social studies games can help students explore and understand historical events, cultures, societies, and geography through simulations, role-playing, and interactive narratives.
4. Assessment and Feedback
- Formative Assessment: Games can be used for formative assessment to monitor student progress, identify learning gaps, and inform instructional decisions.
- Data Analytics and Insights: Game-based learning platforms often provide analytics and insights into student performance, engagement, and learning outcomes, enabling educators to track progress, assess effectiveness, and make data-driven decisions.
5. Accessibility and Inclusivity
- Adaptive Learning: Games can be designed to adapt to students' abilities, needs, and preferences, providing inclusive and accessible learning experiences for all students, including those with disabilities.
- Flexible Learning Environments: Games can be accessed and played anytime, anywhere, allowing for flexible and convenient learning opportunities that accommodate diverse learning styles and needs.
6. Teacher Support and Professional Development
- Game-Based Learning Platforms: Platforms and resources that offer game-based learning experiences can support teachers in integrating games into their instruction, curriculum, and classroom practices.
- Professional Development: Game-based learning can be incorporated into teacher professional development programs to help educators learn about and effectively use games in their teaching, assessment, and classroom management.
Characteristics:
- Interactive: Players actively engage with the game through controls or gestures.
- Entertainment: Designed primarily for entertainment purposes, but can also educate or inform.
- Narrative and Gameplay: Combines storytelling (narrative) with gameplay mechanics to create an immersive experience.
- Genres: Includes various genres such as action, adventure, role-playing, simulation, strategy, sports, and more.
In summary, video games in education offer innovative, engaging, and effective ways to enhance teaching and learning across various subjects, grade levels, and learning environments. By leveraging the power of games to engage students, promote active learning, foster collaboration, and develop critical thinking skills, educators can create enriching and impactful learning experiences that inspire curiosity, creativity, and lifelong learning. As technology continues to evolve and game-based learning continues to gain momentum, video games will continue to play a pivotal role in shaping the future of education and empowering students to succeed in the 21st century.
Ludology
Definition: Ludology is the study of games, including their design, rules, gameplay, and player experiences, from a theoretical and academic perspective.
Ludology refers to the study of games, particularly video games, focusing on the rules, design, and gameplay mechanics that make them engaging and interactive. In the context of education, ludology emphasizes the potential of games as powerful learning tools that can foster critical thinking, problem-solving, collaboration, and engagement among students. Let's explore how ludology is applied in education and its impact on teaching and learning:
1. Understanding Game Design and Mechanics
- Game Design Principles: Ludology in education emphasizes understanding the principles of game design, including rules, objectives, challenges, feedback mechanisms, and progression systems, to create engaging and effective learning experiences.
- Gameplay Mechanics: Understanding gameplay mechanics such as exploration, decision-making, problem-solving, resource management, and strategy can help educators design games that promote these skills in students.
2. Engagement and Motivation
- Intrinsic Motivation: Games often leverage intrinsic motivation by providing challenges, rewards, feedback, and a sense of accomplishment, which can enhance student engagement and motivation.
- Flow State: Games can facilitate the "flow state," a state of complete immersion and focused attention, which can enhance learning, creativity, and enjoyment.
3. Skill Development and Learning Outcomes
- Critical Thinking and Problem-Solving: Games can promote critical thinking and problem-solving skills by presenting students with challenges, puzzles, and scenarios that require strategic thinking, analysis, and decision-making.
- Collaboration and Communication: Multiplayer and cooperative games can foster collaboration, teamwork, communication, and interpersonal skills among students.
4. Subject Integration and Curriculum Alignment
- Subject-Specific Games: Ludology in education involves integrating subject-specific games that align with curriculum standards and learning objectives to help students practice and apply academic concepts and skills.
- Cross-Disciplinary Learning: Games can facilitate cross-disciplinary learning by integrating multiple subjects, themes, and skills into game-based learning experiences.
5. Assessment and Feedback
- Formative Assessment: Games can be used for formative assessment to monitor student progress, assess understanding, identify learning gaps, and provide immediate feedback.
- Data Analytics and Insights: Game-based learning platforms often offer analytics and insights into student performance, engagement, and learning outcomes, enabling educators to track progress, assess effectiveness, and make data-driven decisions.
6. Teacher Professional Development and Training
- Game-Based Learning Workshops: Ludology in education includes providing educators with workshops, training, and resources on game-based learning to help them understand, evaluate, and integrate games into their teaching practices.
- Collaborative Planning and Implementation: Educators can collaborate with game designers, developers, and experts to co-design and implement game-based learning experiences that meet the unique needs and preferences of their students.
Characteristics:
- Game Theory: Utilizes game theory to analyze and understand games as systems with rules, strategies, and outcomes.
- Player Experience: Focuses on player experiences, emotions, motivations, and interactions with games.
- Narrative vs Gameplay: Explores the relationship between narrative (storytelling) and gameplay mechanics in games.
- Cultural and Social Impact: Examines the cultural, social, and psychological aspects of gaming and its impact on society.
In summary, Ludology in education emphasizes the study, understanding, and application of game design principles, mechanics, and strategies to enhance teaching and learning. By leveraging the engaging and interactive nature of games, educators can create immersive, challenging, and effective learning experiences that promote critical thinking, problem-solving, collaboration, engagement, and motivation among students. As the field of ludology continues to evolve and game-based learning gains momentum, integrating ludology principles into education will continue to play a pivotal role in shaping the future of learning and empowering students to succeed in the 21st century.
Conclusion
Relationships
- Video Games: Video games are the tangible products or applications that players interact with, encompassing various genres, gameplay mechanics, and storytelling elements.
- Gamification: Gamification takes game elements and principles and applies them in non-game contexts to engage users, motivate actions, and achieve specific goals.
- Ludology: Ludology provides the theoretical framework and academic study of games, analyzing their design, rules, gameplay, and player experiences to understand and interpret the nature of games.
In summary,
- Video Games: Focuses on interactive electronic games played for entertainment, education, or other purposes, encompassing various genres and platforms.
- Gamification: Utilizes game elements and principles in non-game contexts to engage users, motivate actions, and achieve specific objectives.
- Ludology: Theoretical study of games that examines their design, rules, gameplay, and player experiences from an academic perspective.
While video games, gamification, and ludology are related concepts within the gaming realm, they serve different purposes and perspectives. Video games provide interactive entertainment experiences, gamification applies game elements to non-game contexts for engagement and motivation, and ludology offers a theoretical framework to study and understand games from an academic perspective. Each concept contributes to the diverse and evolving landscape of gaming, offering unique insights, applications, and experiences for players, designers, educators, and researchers alike.
BPM (Business Process Management):
Definition: Business Process Management (BPM) is a discipline and approach that focuses on optimizing, managing, and automating business processes, workflows, tasks, and operations within organizations to improve efficiency, productivity, agility, and performance. BPM involves designing, modeling, executing, monitoring, analyzing, and optimizing business processes to achieve operational excellence and business objectives.
Analytics in BPM:
- KPI (Key Performance Indicators) Monitoring: Monitors and tracks KPIs to measure and evaluate the performance, efficiency, and effectiveness of business processes.
- Process Analytics: Analyzes and visualizes process performance, bottlenecks, inefficiencies, and trends to identify areas for improvement and optimization.
- Custom Reports: Generates custom reports, dashboards, and visualizations to present insights, findings, and analytics on process performance, KPIs, and metrics.
- Predictive Analytics: Applies predictive analytics to forecast future trends, outcomes, and performance based on historical data and insights.
- Decision Support: Provides decision support tools and features to facilitate data-driven decision-making, planning, and strategy development.
ERP (Enterprise Resource Planning):
Definition: Enterprise Resource Planning (ERP) is an integrated software platform and system that integrates and manages core business processes, functions, and operations, such as finance, HR, SCM, CRM, and more, within organizations to streamline, automate, and optimize business processes, workflows, tasks, and operations to achieve operational excellence and business objectives.
Analytics in ERP:
- KPI (Key Performance Indicators) Monitoring: Monitors and tracks KPIs across various departments and functions to measure and evaluate performance, efficiency, and effectiveness.
- Financial Analytics: Analyzes and visualizes financial data, performance, budgets, forecasts, and trends to support financial management, planning, and decision-making.
- Operational Analytics: Analyzes and visualizes operational data, performance, efficiency, productivity, and trends across departments and functions.
- Custom Reports: Generates custom reports, dashboards, and visualizations to present insights, findings, and analytics on performance, KPIs, metrics, and data across the organization.
- Business Intelligence (BI) Integration: Integrates with BI tools and platforms to leverage advanced analytics, data visualization, predictive analytics, and machine learning capabilities.
Comparison:
| Criteria |
BPM (Business Process Management) |
ERP (Enterprise Resource Planning) |
| Focus |
Business Processes and Workflows |
Core Business Functions and Operations |
| Key Components |
Process Design, Modeling, Automation |
Finance, HR, SCM, CRM Integration |
| Analytics and KPIs |
Process Analytics, KPI Monitoring |
KPI Monitoring, Financial Analytics |
| Custom Reports |
Custom Process Reports, Dashboards |
Custom Financial, Operational Reports |
| Decision Support |
Process Optimization, Decision Support |
Financial, Operational Decision Support |
| Integration |
BPM Tools, Platforms, Integration |
ERP Modules, BI Integration |
| User Base |
Process Owners, Managers, Analysts |
Employees, Departments, Managers |
Conclusion:
Both BPM (Business Process Management) and ERP (Enterprise Resource Planning) provide analytics using KPIs and custom reports to measure, monitor, analyze, and optimize performance, efficiency, and effectiveness within organizations.
-
BPM focuses on optimizing and managing business processes, workflows, and operations by monitoring KPIs, analyzing process performance, and generating custom reports to identify areas for improvement and optimization.
-
ERP integrates and manages core business functions and operations, such as finance, HR, SCM, CRM, and more, by monitoring KPIs, analyzing financial and operational data, and generating custom reports to support financial management, planning, decision-making, and optimization.
Both BPM and ERP play a crucial role in providing analytics, insights, and intelligence to support data-driven decision-making, planning, optimization, and success within organizations by leveraging KPIs, custom reports, dashboards, and analytics across processes, functions, departments, and operations in the dynamic and evolving business landscape.
Website
Data Mining Process - GeeksforGeeks
10 Data Warehouse Concepts Every Analyst Should Master
Text Mining Vs Text Analytics | ExcelR
Difference between Data Analytics, Data Analysis, Data Mining, Data Science, Machine Learning, and Big Data? | by Logicmojo | Medium
A Guide: Text Analysis, Text Analytics & Text Mining | by Michelle Chen | Towards Data Science
Data Mining Vs Big Data Analytics - You Need The Right Tools And You Need To Know How To Use Them! – Fly Spaceships With Your Mind
Text Mining Vs Text Analytics | ExcelR
Understanding Text Mining | Baeldung on Computer Science
Business Intelligence - When ERP + BPM = BI



